PowerShell was developed so that IT operations and administrative tasks in operating systems like Active Directory could be simplified and automated to save huge amounts of time and effort.
PowerShell is able to integrate with services and applications to help administrators get complete control over the management of both clients and servers. With every new update of the underlying framework, PowerShell becomes more advanced, and more features become available.
10 PowerShell Commands to Better Manage Active Directory
With that in mind, let’s take a look at some of the most commonly used PowerShell cmdlets that can help you simplify and automate the management of your Active Directory.
Before you get started, you’re going to have to import Module Active Directory. Without importing the corresponding module into the PowerShell session, you will not be able to run any of the cmdlets in the below list.
1. Create a New Computer Object
Use New-ADComputer PowerShell cmdlet to create new computer object
New-ADComputer -Name "ComputerName" -SamAccountName "ComputerName" -Path "OU=Computers,DC=Domain,DC=com"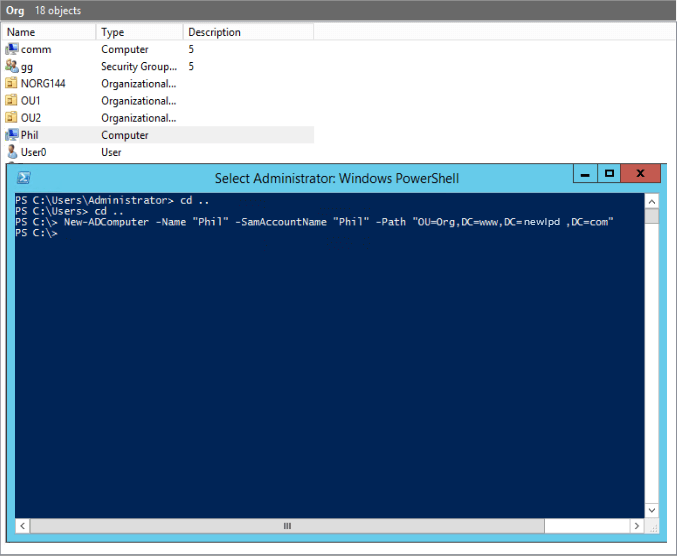
Don’t forget that you will need to specify the Computer Name and the Sam Account Name for this script to work. After the path perimeter, you will need to specify the distinguished name in quotes (where the object is to be created).
2. Create New Security Groups
Use New-ADGroup PowerShell cmdlet to create new group
New-ADGroup -Name "Security Group Name" -SamAccountName "SecurityGroupName" -GroupCategory Security -GroupScope Global -DisplayName "Security Group Name" -Path "CN=Groups,DC=Domain,DC=com" -Description "Brief description of what the security group is used for"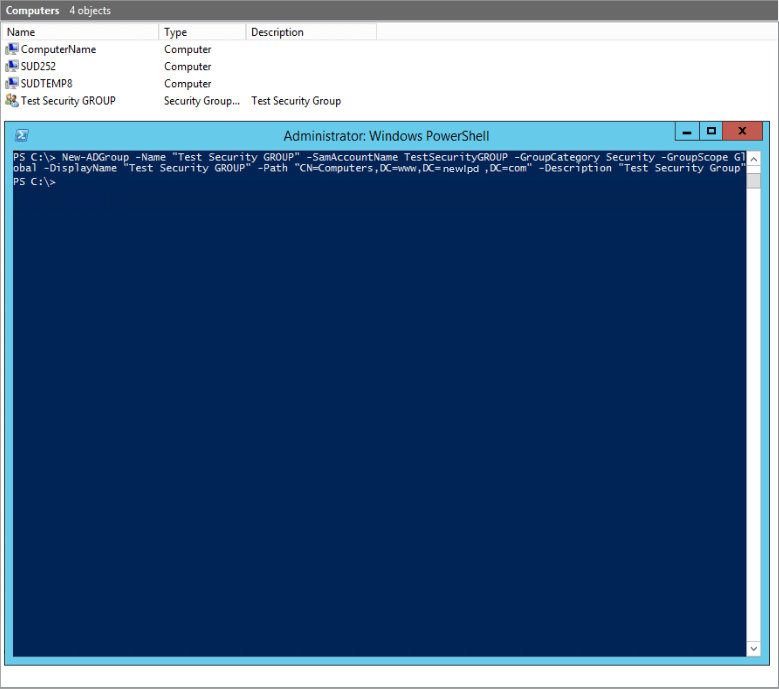
3. Create a New User Account
Use New-ADUser PowerShell cmdlet to create new user
New-ADUser -Name "User Account Name" -SamAccountName "UserAccountName" -AccountPassword (ConvertTo-SecureString "password" -AsPlainText -Force) -DisplayName "User Name" -Enabled $True -GivenName "FirstName" -Path "CN=Users,,DC=Domain,DC=com" -Server "controller.domain.com" -Surname "LastName" -UserPrincipalName "username@domain.com"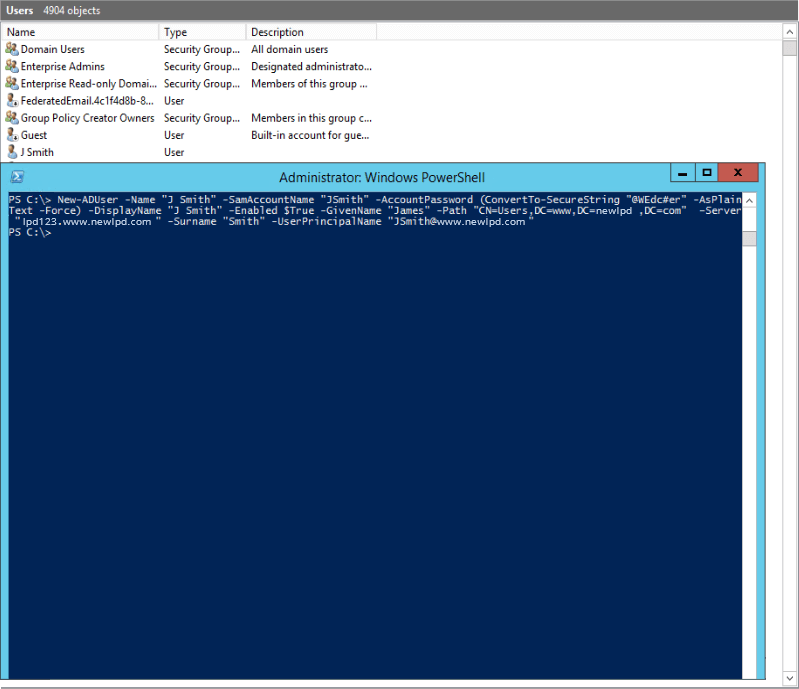
New-ADUser doesn’t have many mandatory parameters but you can use different parameters while creating a new user. Read more
4. Create a New OU
Use New-ADOrganizationalUnit PowerShell cmdlet to create new OU
New-ADOrganizationalUnit -Name "OU Name" -Path "DC=Domain,DC=com"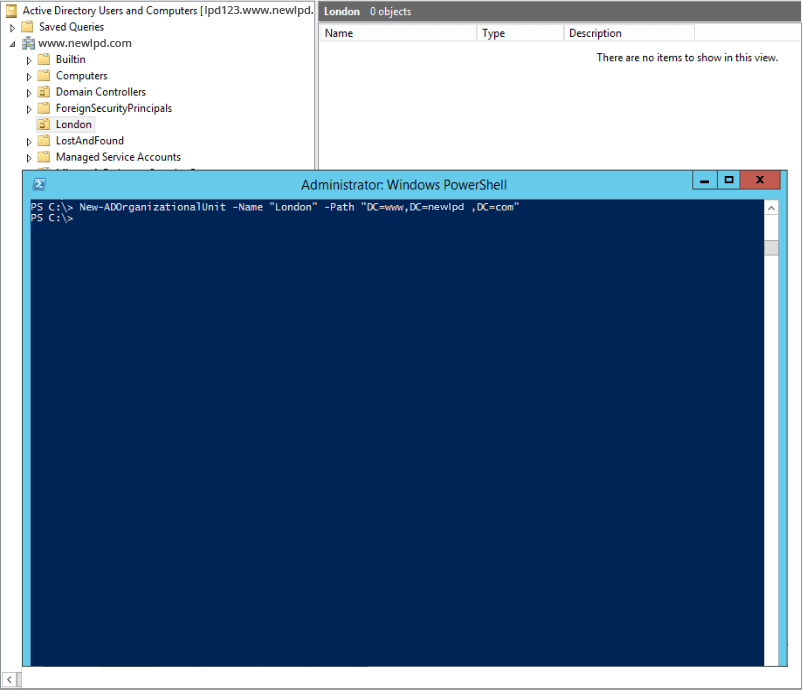
5. Add/Remove Users or Computer Objects to/From Groups
Use Add-ADGroupMember PowerShell cmdlet to add new member
Add-ADGroupMember SecurityGroupName -Members Username01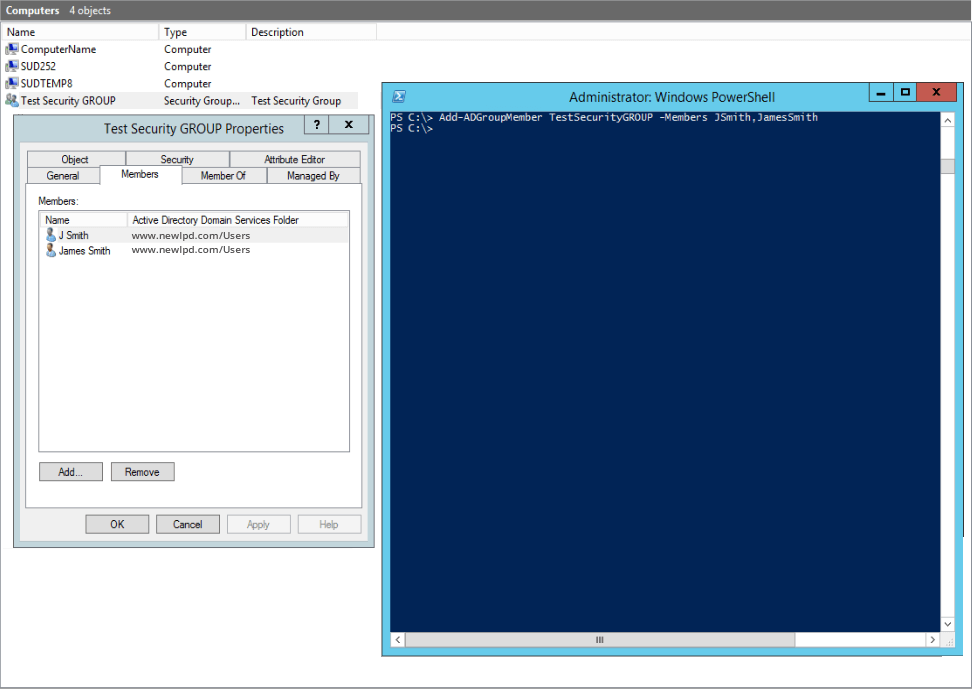
Use Remove-ADGroupMember PowerShell cmdlet to remove member
Remove-ADGroupMember SecurityGroupName -Members Username01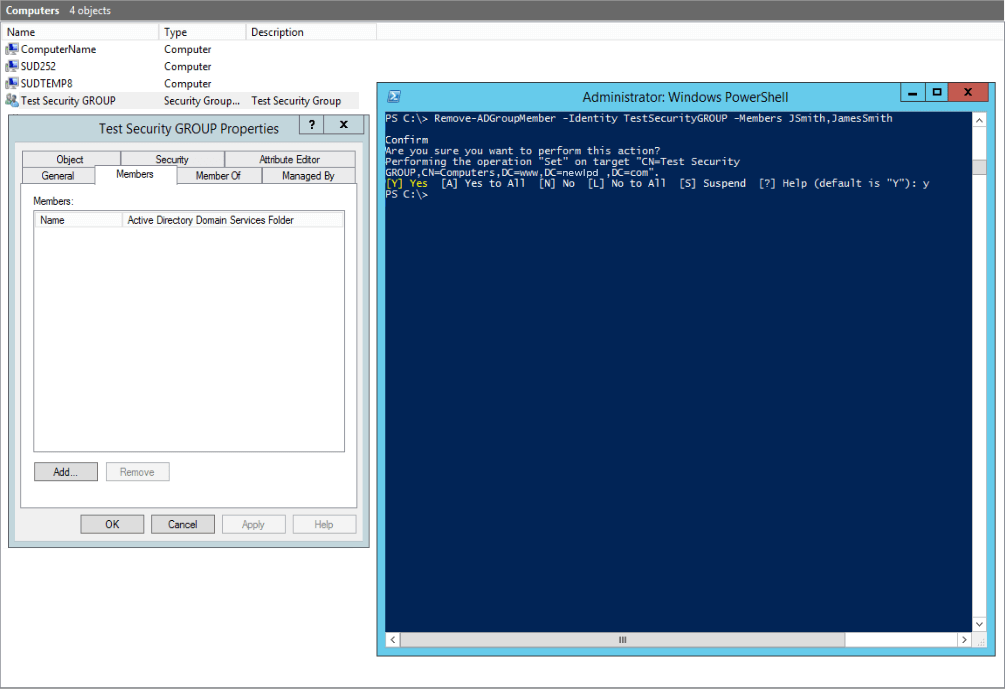
6. Find Locally Stored Password
Use Get-AdmPwdPassword PowerShell cmdlet to find locally store password
Get-AdmPwdPassword -ComputerName "computer.domain.net"For this those who want a simpler way to search for passwords stored in the computer object, need to implement the Local Administrator Password Solution (LAPS) from Microsoft. It’s free and an excellent way of displaying the details in a single report as opposed to having to go through each object to get the password.
7. Add a Computer to a Domain
User Add-Computer PowerShell cmdlet to add a new computer
Add-Computer -DomainName "domain.com" -Credential Domain\Username -Restart –Force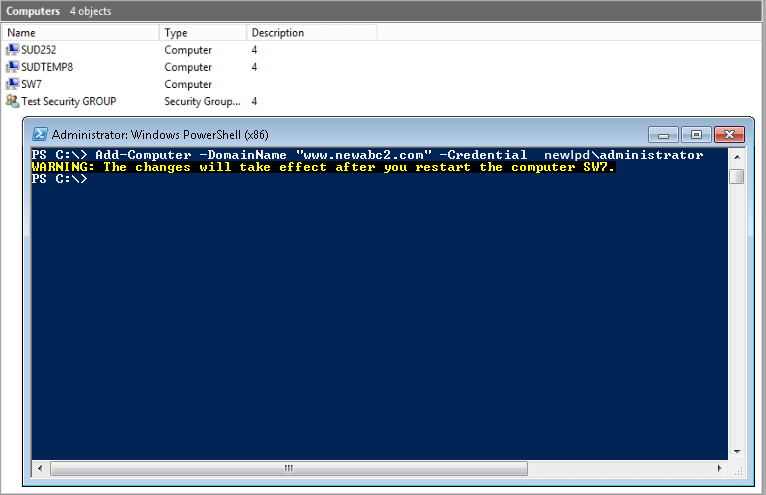
8. Enable or Disable Users, Computers and Service Accounts
Enable-ADAccount -Identity "ComputerName"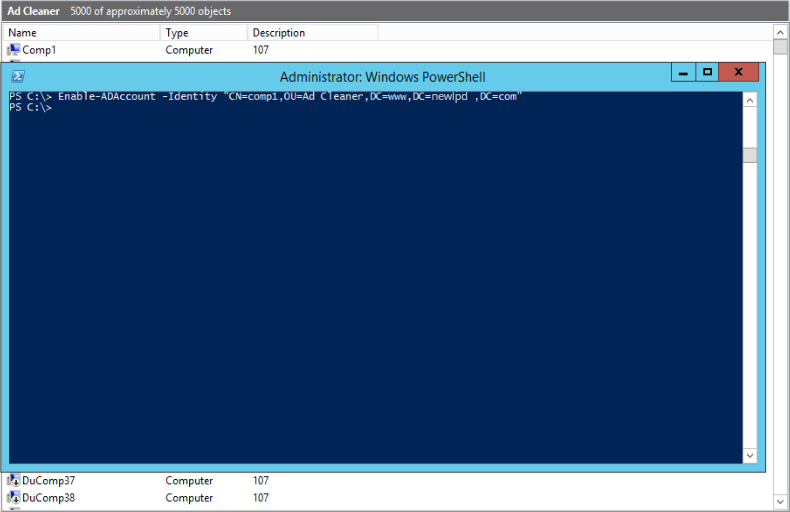
Disable-ADAccount -Identity "Username"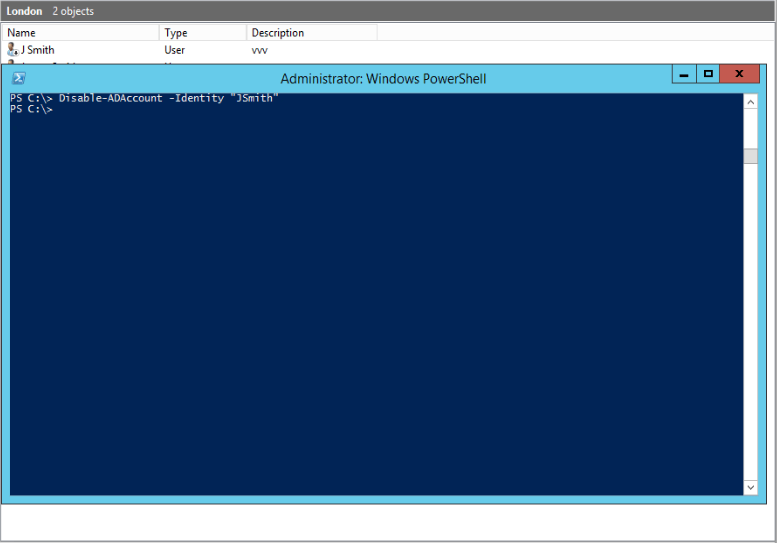
9. Unlock User Accounts
Use Unlock-ADAccount PowerShell cmdlet to unlock account
Unlock-ADAccount -Identity "Username"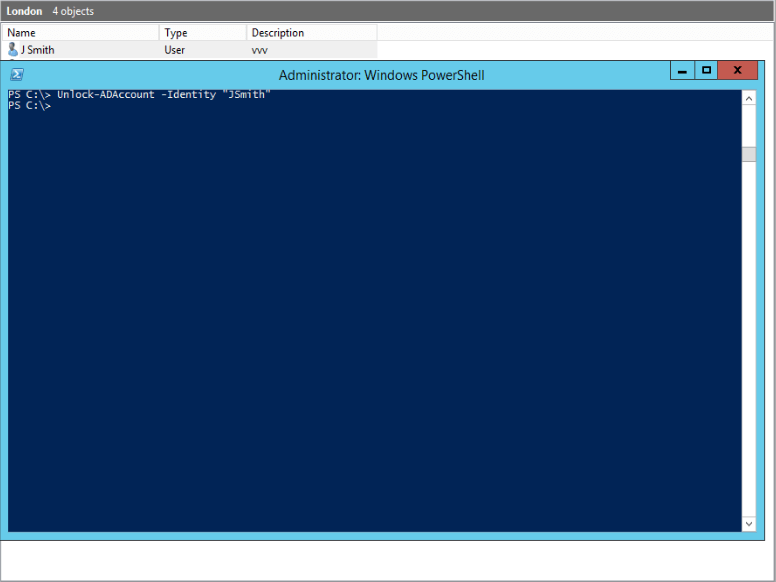
10. Find Inactive Users
Use Search-ADAccount –AccountInActive PowerShell cmdlet to find inactive accounts in Active Directory and import them in CSV.
Search-ADAccount –AccountInActive –TimeSpan 90:00:00:00 –ResultPageSize 2000 –ResultSetSize $null | ?{$_.Enabled –eq $True} | Select-Object Name, SamAccountName, DistinguishedName | Export-CSV “C:\Temp\InActiveUsers.CSV” –NoTypeInformation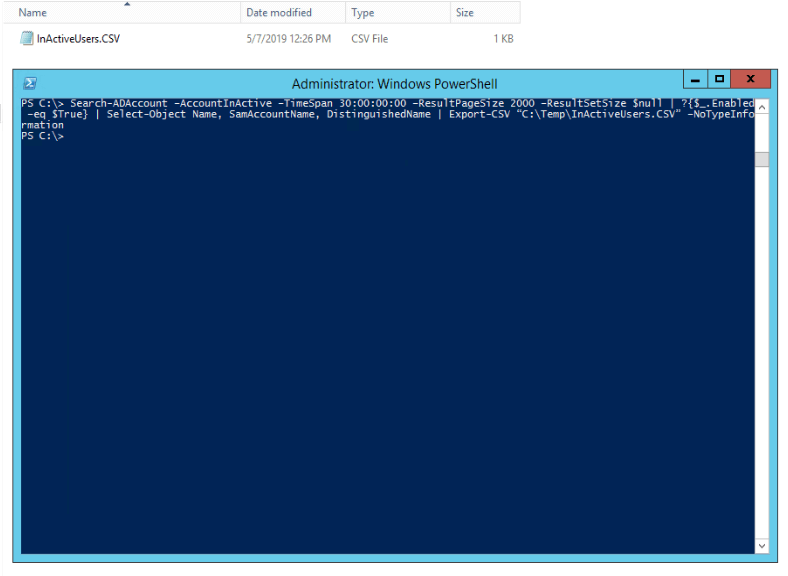
A large number of inactive users can seriously increase the potential attack surface of your organization. Attackers often use these accounts to leverage the permissions and move laterally across the network. The above cmdlet allows you to identify these inactive users. This cmdlet has a time frame to determine which users have been inactive for the last 90 days and exports the list into a CSV file.
Other important commands are:
These PowerShell commands should help you improve the basic management of your Active Directory even further. If you need more visibility into changes taking place in your AD, please see how Lepide Active Directory Auditor can help you.




