Last Updated on December 26, 2024 by Satyendra

Introduction
2017 has been a year full of high profile data breaches and this week, global accounting firm Deloitte has joined the list of those affected (reports the Guardian).
If you don’t know who Deloitte are, all you need to really know is that they reportedly turned over a record $37bn in revenue last year. They also provide auditing, tax consulting and high-end cybersecurity advice to some of the world’s largest organizations. Ironic then, that they should fall victim to a cybersecurity breach that could have so easily been avoided…
As with any high-profile data breach, hindsight is a beautiful thing. However, how many more of these events are going to occur before organizations start to learn from them? I’m going to take you through three quick lessons that any IT team, regardless of the overall size of your business, can implement to immediately beef up IT security.
Why did the Deloitte breach happen?
Before we can delve deep into how to avoid data breaches similar to the one that Deloitte suffered, we need to learn a bit more about why it happened.
In the most simplistic of terms, emails to and from Deloitte’s staff (which is nearly a quarter of a million people, by the way) were stored on Microsoft’s Azure cloud service. A resourceful hacker then gained entry to this email server via an administrative account which gave them full, privileged levels of access to sensitive information. Sources close to the breach indicated that this account required only one password for access, but more on this later…
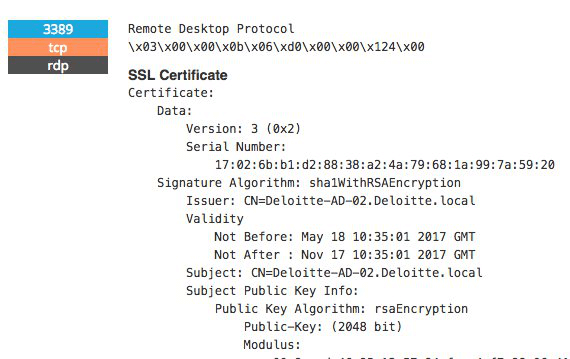
Not only this, but the Guardian also suggests that hackers had access to usernames, passwords, IP addresses and much, much more. A little more investigation into this confirms that Deloitte had left its corporate Active Directory server on the internet with remote desktop protocol open – practically inviting an internal email system attack.
This disastrous lapse in IT security best practices was uncovered by security researcher Dan Tentler, who described the problem without holding back what he thought: “The problem is they put a f****** active directory server directly on the internet with RDP exposed. [This is] the place where all the creds live… on the internet. With RDP open.”
Many people have suggested reasons for why Deloitte may have done this. However, regardless of whether this was set up as a read only server, it gives any wannabe hacker some key info; including the fact that Deloitte runs its Active Directory on an unpatched version of Windows Server 2012, R2.
Deloitte discovered the email breach back in March of this year. But it is now understood that attackers may have had access since October of 2016.
Could it have been avoided?
There’s an obvious fix for that AD issue…simply tighten up security controls. For the purposes of this article we will focus on some other, but no less glaring, ways in which Deloitte can improve their IT security.
I think it’s probably necessary to state that it’s impossible to completely eradicate the possibility of a data breach in the modern era. Having said that, this particular breach was certainly avoidable. Some simple changes in the mindset of the organization, as well as some take-up of security best practices, would have probably done the trick here. Let’s run through a few:
1. Better authentication is required
The privileged account that provided unabated access to Deloitte’s sensitive information only required the hacker to get through one password. In this day and age, multi-factor access control, such as two-factor authentication, is a necessity when it comes to privileged accounts. Some of the more common methods of multi-factor access control are:
- Using a card and pin number in conjunction with each other
- Entering a unique, generated pin number as well as the usual password (usually sent to a mobile device or email address)
- Answering a security question as well as a password
Implementing any of these security controls immediately helps to prevent hackers from gaining easy access. Obviously a sophisticated and persistent hacker may find a way to circumvent these controls, but clearly the privileged accounts should be the hardest to gain access to (even legitimately).
2. More visibility into critical systems and data is necessary
This particular breach occurred through Microsoft Azure, however that doesn’t mean your organization is safe if you’re using an on-premises email provider, such as Exchange. This attack was able to take place, and went unnoticed for so long, because there was a lack of visibility into critical changes taking place to sensitive servers and data.
The security of your critical systems can be immediately improved if you have a solution in place that gives you instant insight into changes taking place across your Active Directory and email servers. In fact, any server that provides access to critical data should be proactively and continuously monitored to ensure that no unauthorised or unwanted change goes undetected.
3. More attention should be put on the Principle of Least Privilege
Coincidentally, we wrote an article about how to master the Principle of Least Privilege (PoLP) not too long ago. Essentially, it comes down to ensuring that your users only have access to the data they require for their job, nothing more.
Let’s say, for example, a user is afforded privileges they don’t really need. This account has just immediately become the main target for attackers. Think what they can get their hands on if they get access to this account! Combine this with one-factor authentication and you essentially have a ticking time bomb in your critical IT infrastructure.
There are a few things you need to do to help you implement PoLP:
- Identify who your privileged users actually are
- Monitor their activities in your servers and check what they’re doing with your data
- Reverse any unwanted changes back to their original states
- Identify any changes in permissions that are unwanted or unauthorised
For more information on these points, you can visit our detailed page on detecting and preventing privilege abuse.
So, make sure you learn from Deloitte’s mistakes! Do you need help auditing, monitoring and alerting on activities taking place in your critical servers and to your sensitive data? If so, click here to explore how Lepide Data Security Platform will help you do just that and book a demo with one of our engineers today


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
