Organizations use SharePoint to store, organize, share and access information from any device due to its powerful collaborative capabilities. However, keeping track of the changes being made to configurations and content can be a real challenge.
Why should you make SharePoint Security a Priority?
Because of its collaboration advantages and its ease of use, companies often share sensitive data on SharePoint, which means that it is crucial to ensure it is secure.
Each SharePoint Online site needs to have its own policies, workflows, and permissions making it a complex infrastructure where keeping track of changes can be a difficult process. If permissions are hacked or given by accident, then users can add, view, copy, edit or delete information that they should not have access to. Therefore, the regular auditing of SharePoint permissions and content is critical to ensure that content is protected, and compliance regulations are not breached.
Best Practices for SharePoint Security
Here are some useful tips to help you improve the overall security of your SharePoint environment.
1. Share Permissions
Protect Content Shared with External Users: The collaborative nature of SharePoint often requires users to share information with external parties. In these cases, the security of that information should be the top priority. In most cases, external sharing should be blocked where possible and external sharing to only be allowed when there is a legitimate business requirement for it. All external sharing sites should be isolated into a single site collection to provide more visibility and control over what is being shared externally.
Doing this will help you ensure that you don’t fall victim to privilege abuse or allow unknown third parties to access your sensitive data. By sharing externally using separate site collections and educating your employees about the best practices of sharing content externally, you’ll be able to mitigate the associated risks.
Disable Anonymous Sharing: There are times when your users want to share content quickly and anonymously and there are many ways for them to do this. Many organizations restrict attachments on email, so users will look to using Dropbox, Google Drive and other methods of anonymous sharing. SharePoint also has anonymous sharing functionality, but this can be disabled. This is recommended for a number of reasons, including limiting what your users can share without you being able to see it and being able to gather all required data sharing information in the event of a data breach investigation.
2. Groups for User Management
Permissions can be assigned individually or through security groups, and both methods have their pros and cons when it comes to the best method for controlling access and authorization. Individually assigning permissions can provide more control and often more appropriate levels of privileges, however it is more difficult to manage. Assigning permissions through security groups is far easier to control although they could potentially lead to over-privileged users if not managed correctly.
Groups allow permissions to be assigned in a way that ensures you are adhering to the principle of least privilege. Users that change roles within the organization or move on can have their permissions revoked easily by simply removing them from the security groups. Permissions assigned at user level, on the other hand, can be forgotten about and so are rarely revoked in these cases.
3. Stop Using Item Level Permissions
SharePoint does not provide an easy method to identify unique permissions and address them in the same way that File Server does. Whilst assigning permissions at item level may seem like a good way to speedily get permissions to that item, it will create an unsecured environment in the long run. For this reason, it’s better to use it sparingly.
Instead of using item-level permissions, try instead to use libraries or folders to assign permissions. This will help you control access rights, reduce the chances of broken inheritance and reduce the possibility of an increased attack surface.
4. One Administrator Per Site or Site Group
As discussed previously, groups can be created, and administrators can be assigned to each group to oversee all activity within their particular group.
By ensuring that there is only one administrator, they can be held accountable for all the sharing that goes on in the group.
5. Use Inbuilt Microsoft’s Security Features
Microsoft has some built-in security features that can help you improve the security of your account. Two of the most widely known and used features are encryption and virus detection.
Encryption: The Microsoft environment offers many levels of protection including — access security, data security, application security, physical data center security, and network security.
Encryption is divided into two phases – In-Transit encryption and At Rest encryption. In-transit encryption is used when data enters and leaves data centers. For the encryption of data at rest, there are two components involved — encrypting customer content with per-file encryption and the BitLocker disk-level encryption. Both forms of encryption are available on the SharePoint online platform.
Virus detection: The detection of viruses is another SharePoint Online feature. The feature checks all content within a site. It’s usually automated and uses a highly sophisticated anti-virus engine to scan for malware and viruses. Although the virus detection feature is effective, it is often limited. For example, it does not check files that are larger than 25MB so it is essential to have separate anti-virus detection software that can check larger files and is available offline.
6. Regularly Review Access Rights
As a collaboration tool, SharePoint often works in the background, and because of this, problems are often only spotted when data breaches occur.
It is essential, therefore, to continually audit and monitor SharePoint changes to detect anything that could potentially lead to downtime or a data breach. If you can easily report on the state of your SharePoint environment, it will be a straightforward process to remain secure and compliant with regulatory standards. You will need to carefully monitor configuration changes, permission changes and user profile changes.
7. Audit SharePoint for Changes and Access Events
SharePoint is a highly dynamic environment, so once you have configured it, you cannot just ignore it. It’s critical to audit all activity in SharePoint, including changes to services, server hardware, virtual hardware and security settings, so that you can quickly spot issues that could lead to breaches and business disruption. If you want the best threat detection and response, supplement the built-in features with a third-party monitoring tool such as Lepide Auditor for SharePoint.
8. Classify the Data you Store in SharePoint.
Most organizations understand the need to classify their data so they can control the use of sensitive and confidential content in accordance with internal security policies and industry or government mandates.
Data loss prevention (DLP) technology can identify sensitive data and then block or allow access to it according to your policies. DLP is integrated into all Microsoft 365 services and in particular, SharePoint, and it enables you to inspect the content, metadata and location of data and then apply security policies you have created to protect it. However, to identify and secure sensitive content in your on-premises SharePoint, you’ll need a third-party solution such as Lepide data classification software.
How Lepide Helps with SharePoint Security
Lepide Auditor for SharePoint, which is simple to install and configure, includes a large number of predefined audit reports (for both SharePoint On-premises and Online) that give you the ability to see every change in the SharePoint environment and the depth to create a long audit trail. You can filter, sort, group by and apply other auditing functions to these reports.
Here is an example of the All Modifications in SharePoint Online Report:
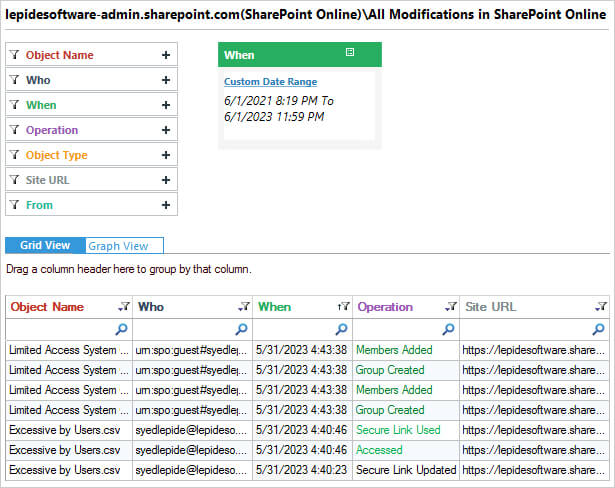
This report shows any changes which take place in SharePoint within a specified time period.
The Lepide Solution also includes the ability to create real-time alerts, with advanced filtration and threshold limits, sent as an email, as an update to the LiveFeed on the console’s Radar tab and as a push notification to Apple and Android devices. Scheduled tasks can be created to generate and deliver audit reports through email or save them in shared locations.
If you want to improve the security of your SharePoint Server, the Lepide Solution can help. The Lepide SharePoint Auditor will help you achieve a higher level of auditing and monitoring to help strengthen your security efforts. Schedule a demo of the Lepide SharePoint Auditor today.




