Last Updated on December 20, 2024 by Satyendra

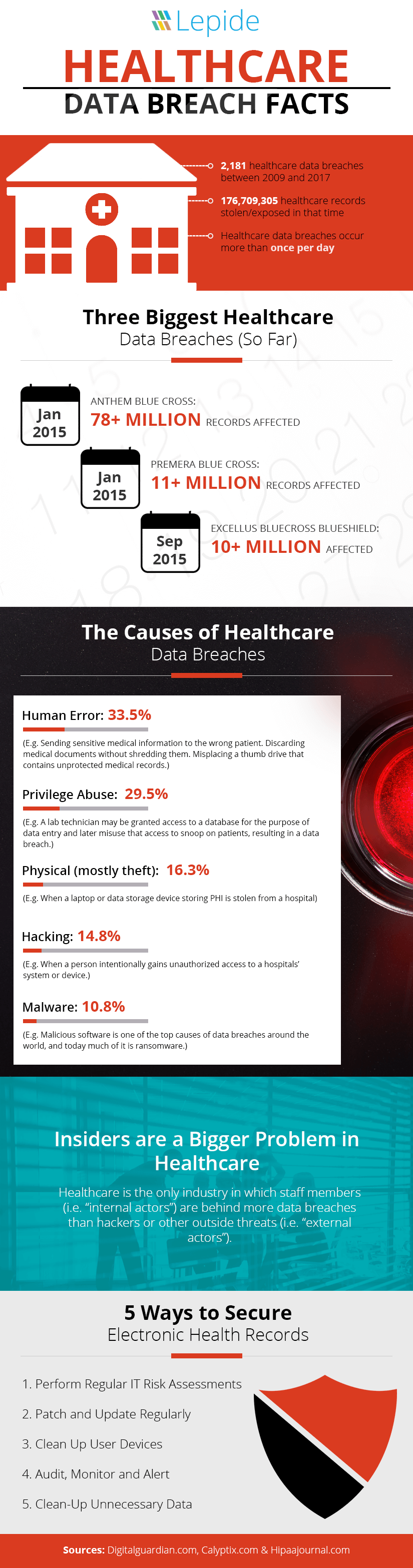
The number of Electronic Health Records (EHR) being lost or stolen is increasing year on year, despite the best efforts of healthcare organizations and the increasing strictness of HIPAA compliance.
According to the HIPAA journal, January alone saw just over half a million records breached. Now, half a million records may not sound like much compared to other breaches, such as social media breaches, the sensitive nature of an EHR makes the breach potentially incredibly damaging.
If an attacker gets hold of an EHR, or an EHR is sold on the black market, the potential risks of identity theft are huge. Some research even suggests that an EHR could be worth up to $1000 on the black market – making that half a million records breached in January suddenly take on a whole new value.
With that in mind, let’s take a quick look at some of the tactics healthcare organizations can use to increase the security of Electronic Health Records.
1. Perform Regular IT Risk Assessments
The cyber-security market, especially in the healthcare sector, is a constantly evolving world of threats. To keep up with the advancements that attackers are making, and to ensure your evolving IT environment maintains the same levels of security, regular IT risk assessments are required.
If you want more detail as to how to perform an IT risk assessment, we have written a blog on this very topic. However, the main points are to ensure you know what the risks and threats facing your critical systems and EHR are, assess the areas where you might be vulnerable, identify and organize your data based on risk and take action to mitigate potential threats.
It’s not enough to perform this once a year, or even biannually. To truly ensure that your IT environment is one step ahead of the cyber-security threat landscape, IT risk assessments need to be performed as frequently as possible.
2. Patch and Update Regularly
Many cyber-security attacks, including the now infamous WannaCry attack, are able to wreak their havoc through exploiting unpatched our out of date medical devices. Many people outside of the healthcare industry may be surprised to learn that a vast majority of hospitals and pharmaceutical companies are running common operating systems, like Linux and Windows, making them just as susceptible to cyber-attacks as everyone else.
Probably one of the most effective cyber-security techniques is the religious and almost fanatical obsession with maintaining an up to date and fully patched software environment – including every device you use.
3. Clean Up User Devices
The healthcare industry is no stranger to Bring Your Own Device (BYOD) and the associated security risks. However, healthcare organizations do need to ensure that they have put in place the appropriate security controls, practices, rules, processes and technology to ensure that healthcare information access on personal devices is protected.
Ideally, healthcare organizations would not ever allow patient data to be accessed from personal devices. Virtual desktops can facilitate this, but they often over-extend healthcare budgets due to high back-end implementation costs. Therefore, mobile devices seem to be the way to go.
However, there are ways you can ensure that BYOD doesn’t lead to vulnerabilities in your data security. Mobile Device Management solutions offer a way of encrypting data accessed on mobile devices, deleting data in the event of lost or stolen devices, separating personal and professional data and much more. It’s a must for those operating in a BYOD environment who are serious about their security.
4. Audit, Monitor and Alert
One of the biggest threats to data security in the healthcare industry, that often goes unaddressed, is insiders. Employees with privileged levels of access to the most sensitive information, including Electronic Health Records, are very often the cause of the biggest and most costly data breaches. This is because an insider threat can be malicious or accidental and go unnoticed for long periods of time due to its un-intrusive nature.
The only way to adequately defend against insider threats is to ensure that you have a way of continuously monitoring their activities and reporting on suspicious or unauthorized changes as quickly as possible. Unfortunately, the most common approach to this is through built-in log management functionality. Whilst this is better than nothing, it is nowhere near powerful enough to really affect your cyber-security posture. This is because it can be difficult to gleam meaningful information from raw logs, and the process of investigations can be both complex and time consuming.
Third-party change auditing solutions can help IT teams in healthcare industries increase their IT security through proactive auditing, monitoring and real time alerting on changes made to Electronic Health Data and critical IT systems. They can enable users to get a better understanding of where sensitive data resides, who has access to it, what changes are being made to it and much more.
5. Clean-Up Unnecessary Data
Often, organizations collect, store and process vast amounts of data unnecessarily. Data like this and stale accounts can present huge opportunities for hackers. Many compliance regulations, including HIPAA, require you to regularly review and delete unnecessary patient data for the sake of the security of that patient.
As a general rule of thumb, you need to be consistently classifying your data, separating the sensitive data from the data you can remove. Keeping your databases and systems clean can drastically reduce the risk of data breaches.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
