Last Updated on January 14, 2025 by Deepanshu Sharma

A Distributed Denial of Service (DDoS) attack is where cybercriminals flood a target network with malicious traffic, thus making it unavailable. The number of DDoS attacks is on the rise, and they are becoming increasingly sophisticated and destructive. According to InfoSecurity Magazine, there were almost 3 million DDoS attacks in the first quarter of 2021 – a 31% increase over the same period in 2020. Attackers are also finding ways to profit from DDoS attacks as well. Previously, DDoS attacks were generally carried out for the sake of causing disruption and/or damaging the reputation of the target organization. Now, in some cases, the attacker will request payment from the victim in order to stop the attack.
How Do DDoS Attacks Work?
Web servers, and other network resources, can only handle a certain number of requests at any one time. If the number of requests to a server or network resource exceeds these limits, they will grind to a halt, thus preventing any new requests from being serviced. A DDoS attack typically uses a ‘botnet’ to deliver large volumes of traffic. In other words, the hackers will try to create a network of computers, or ‘zombie networks’, by compromising remote devices, usually on an ad-hoc basis, via social engineering, or some other technique. Once infected, they will be ordered to simultaneously launch an attack, thus overwhelming the target server. It’s worth noting that few cybersecurity professionals really understand how DDoS attacks work, let alone how to stop them. This is because DDoS attacks originate from outside of their networks, and don’t require the use of malware or direct phishing attempts to be effective.
What Are Some Common Types of DDoS Attacks?
In order to help us better understand how DDoS attacks work, it helps to understand a small amount about how network connections are made. Network connections on the internet are comprised of layers, as defined by the OSI model. These layers are as follows;
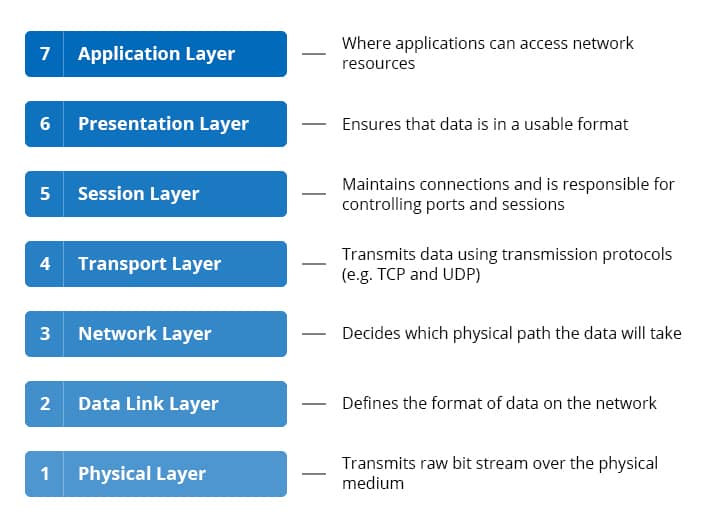
Below is a brief description of the different types of DDoS attacks, and how they relate to the OSI model;
Application layer attacks
Also referred to as layer 7 or HTTP flooding attacks, an application layer attack targets the layer that generates web pages on the server. Since servers load multiple files and run database queries in order to create a web page, a single HTTP response is computationally expensive relative to the HTTP request. It is difficult to defend against application layer attacks as there isn’t an easy way to differentiate between malicious and legitimate traffic.
Protocol attacks
Protocol attacks target network equipment, such as firewalls and load balancers. The goal of these attacks is to overwhelm network resources in order to make them unavailable. Protocol attacks target the Network Layer and the Transport Layer, which in turn renders the Application Layer inaccessible.
Volumetric attacks
The goal of a volumetric attack is to consume all of the available bandwidth on a target network. In many cases they use DNS amplification to leverage the functionality of open DNS resolvers to amplify the amount of traffic sent to the target network, thus rendering it inaccessible. However, in some cases, a botnet is used to flood the network with traffic. While bandwidth is relevant to the Physical Layer, a volumetric attack will target the Data Link Layer, Transport Layer and Network Layer.
How Can You Mitigate a DDoS Attack?
As mentioned above, the biggest problem we have when it comes to mitigating DDoS attacks is that it is very hard to differentiate between legitimate traffic and DDoS traffic. This is because DDoS traffic can arrive in many forms, from many different locations, and target many different network resources. For example, some DDoS attack vectors use multiple attack pathways, which might include HTTP flooding coupled with DNS amplification. As such, we need to adopt a layered approach, which may involve the following techniques:
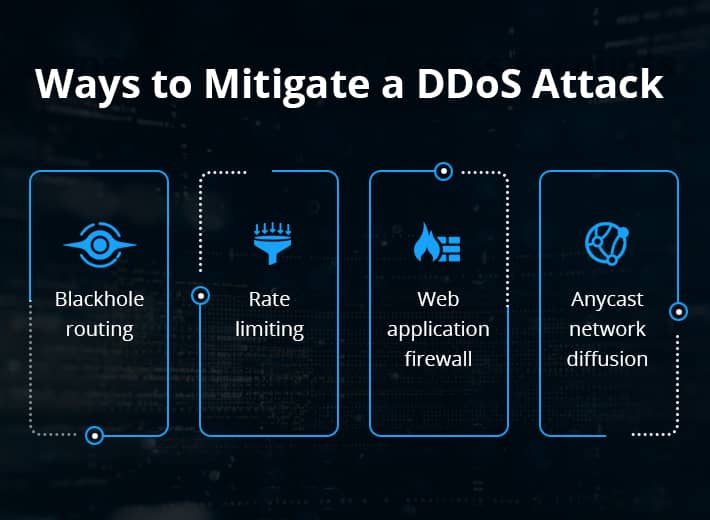
Blackhole routing
This is where you funnel traffic into a ‘blackhole’, where the traffic is essentially discarded. This approach can be effective if the restriction criteria are properly configured. If it is not, both legitimate and malicious network traffic will be lost, thus making the network inaccessible.
Rate limiting
Limiting the number of requests a server will accept over a certain time-frame is also an effective way to minimize the damage caused by a DDoS attack. However, rate limiting alone will not be able to completely prevent DDoS attacks.
Web application firewall
A Web Application Firewall (WAF) focuses on protecting the Application Layer. By placing a WAF between the internet and your network, you can filter out certain types of malicious traffic. Modern WAF solutions also use machine learning techniques to learn anomalous activity patterns.
Anycast network diffusion
Anycast is a network addressing and routing method which can route incoming requests to a variety of different locations. It essentially scatters traffic across a network of distributed servers, thus preventing the DDoS attack from making any specific server or resource inaccessible. The effectiveness of anycast network diffusion depends on both the size of the attack and the size of the network. Naturally, the bigger the network of distributed servers, the more effective it will be.
What’s the Difference between a DDoS and a DoS Attack?
Even-though DDoS (Distributed Denial of Service) and DoS (Denial of Service) attacks are both designed to flood a network with malicious traffic, there are some subtle differences between them. Unlike a DDoS attack, a DoS attack doesn’t rely on creating a botnet of distributed devices to carry out the attack. Instead, it uses a single-source SYN flood, which manipulates the TCP three-way handshake. DoS attacks tend to focus on specific servers as opposed to entire networks, and they don’t target devices between the attacker and the organization. Given that DDoS attacks are more effective than DoS attacks, they have become more popular in recent years.
Conclusion
DDoS attacks can be incredibly disruptive and damaging to your organization, so it’s vital that you have an adequate incident response plan in place. With Lepide, you can audit changes and interactions in Active Directory and data stores in real time, and respond to threats instantaneously with pre-defined threat models.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
