Last Updated on March 5, 2025 by Satyendra

What is an Account Lockout Policy?
The Active Directory account lockout policy is designed to safeguard user accounts from unauthorized access by disabling them if an incorrect password is entered repeatedly within a specific period. The policy works by keeping a record of all failed domain logon attempt on the primary domain controller (PDC). When the threshold is met, the PDC locks the account, effectively preventing successful logon attempts. An administrator can reset the password or the account lockout period can expire, allowing the user to log in successfully again.
What Are the Main Causes of Account Lockouts?
Users may find themselves locked out of their accounts for a large number of reasons – some of which include;
- Attempted brute-force attacks;
- Service accounts with passwords that have been recently changed or have expired;
- Issues with Active Directory replication;
- Cached user credentials saved in certain programs;
- Users signing in from multiple devices;
- Poorly configured password threshold;
- Stored login details that contain overlapping credentials;
- Scheduled tasks using expired credentials;
- Shared drives using expired credentials;
- Terminal Server sessions that have been disconnected;
- Mobile gadgets that are accessing the exchange server via IIS.
Why are Account Lockout Policies Important?
Sysadmins receive numerous support tickets relating to users who are locked out of their accounts due to forgotten or mistyped passwords. These lockout incidents consume valuable resources. To illustrate the point, the average cost of handling a single ticket is around $15. Hence, it is crucial for companies to establish their account lockout guidelines to mitigate lockouts without undermining their network’s safety. While it’s impossible to prevent all lockouts, employing the following best practices can substantially decrease their frequency.
Best Practices for Account Lockouts Policy in AD
Below are some of the most commonly cited ways to prevent and manage account lockouts in Active Directory:
Enable the “Account lockout duration” policy
The duration of account lockout is determined by organization-specific factors, such as the number of users or industry type. To ensure security, setting a duration of zero locks the account until an administrator unlocks it, but this can lead to a high volume of requests to the help desk. It is advisable to set a duration between 30 and 60 minutes for optimal performance. You can edit the account lockout policy GPO at “Computer Configuration\Windows Settings\Security Settings\Account Policies\Account Lockout Policy”.
Enable the “Account lockout threshold” policy
Accidental lockouts may occur when the account lockout threshold is too low, leaving the account open to denial-of-service attacks that an attacker can easily initiate by intentionally entering incorrect passwords. Conversely, when the threshold is too high, the chances of a brute-force attack occurring increase since the attacker has more attempts to guess the credentials. A threshold of 15 to 50 is suggested as optimal.
Configure the “Reset account lockout counter after” policy
When determining the “reset account lockout counter after” value, organizations should consider the nature and severity of potential security risks, while also taking into account the expense of help desk support. It is important that this value is not greater than the account lockout duration. It is advisable to set this value to less than 30 minutes.
Configure policies based on user security level
The Fine-Grained Password Policy feature in Active Directory enables the customization of policy values for users with different security levels. To accommodate low-security users, disabling account lockouts by setting a threshold of zero is recommended. In contrast, high-security users such as administrators and managers should have an account lockout duration of zero, allowing only an admin to unlock a locked account. Considering the increased security measures required for these users, it is advised to set a low account lockout threshold to promote careful entry of login credentials.
Provide training to end users
Organizations should provide periodic cybersecurity training sessions to all employees, which should include sessions on how to prevent account lockouts.
Monitor spikes in lockout activity
When dealing with a large number of employees, it can be challenging to monitor every user’s account lockout activity. Thankfully, User Behavior Analytics (UBA) solutions can detect unusual spikes in lockout activity. To receive prompt notifications about high-security user account lockouts and speed up the unlocking process, you can configure alerts to be sent to your inbox or mobile app. Some UBA solutions can execute custom scripts that can unlock specific accounts in real time.
Ensure that credentials are up-to-date
System services, scheduled tasks, and disconnected terminal sessions frequently cause account lockouts by using outdated credentials. To resolve this problem, it is advisable to clear the credential manager and restart the computer. Users should also be cautious of mobile apps that use AD credentials, such as Outlook and Microsoft Exchange Server, as they may continue to use outdated login information. It is important for users to update their credentials after making two or more password changes. It should be noted that in Windows Server 2003 and newer versions, a password that has been previously used within the last two changes will not be considered an incorrect login attempt.
Investigate all account lockouts
In order to investigate account lockouts, it is necessary to capture logs to trace their origin. This involves enabling auditing of logon events, including events associated with Netlogon and Kerberos. You will need to identify the source of authentication failures using account lockout management tools, checking the PDC emulator, and enabling user account management auditing. Filter for event 4740 and review events to locate the affected account. Check the security, application, and system logs on the target machine for anomalies and block RDP ports if necessary.
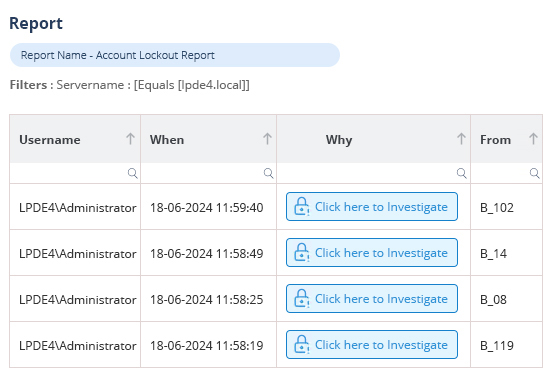
How Lepide Account Lockout Examiner Free Tool Helps?
The Lepide Account Lockout Examiner Free Tool allows administrators to quickly identify and resolve account lockout issues. By generating detailed reports on locked accounts, you can easily investigate the reasons behind each lockout and take appropriate action.
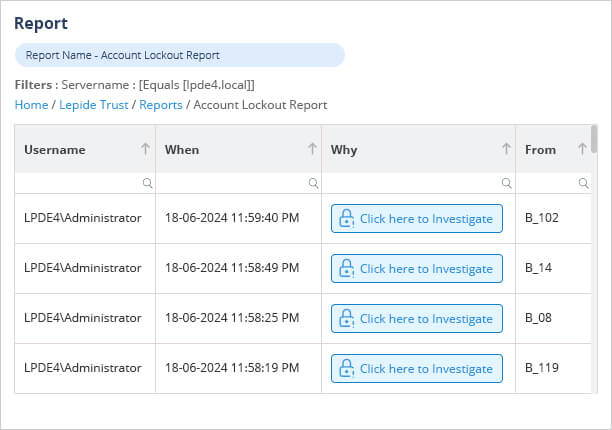
To see how it works, download the Lepide Account Lockout Examiner Free Tool now.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
