
What is Group Policy Editor
Group Policy Editor is a Windows tool which offers a centralized way of mass managing and configuring a wide variety of network and computer settings within the same domain.
Group Policies are most useful for network administrators so that they can configure password requirements, startup programs, and define what applications or settings users can change.
These collections of Group Policy settings are called Group Policy Objects (GPOs). Microsoft provides a program snap-in that provides the Group Policy Management Console (GPMC) and the selections chosen within this result in a Group Policy Object. The GPO is related to selected Active Directory containers including sites, domains or organizational units (OU).
What Can You Do with the Group Policy Editor
Group policies control what version of network protocols are available and implement password rules. Corporate IT security benefits significantly by the setting up and maintaining of a strict Group Policy. Here are a few examples of good IT security group policies:
- Limit which applications can be installed or accessed by users on their managed corporate devices
- Disable removable devices like USB drives
- Disable unsecure network protocols like TLS 1.0 to enforce usage of more secure protocols
- Limit which settings a user can change with Control Panel. For example, allow them to change their screen resolution but not edit the VPN settings.
- Stop users from accessing gpedit so that they cannot change any of the above settings.
How To Access Group Policy Editor
There are several ways to open Group Policy Editor but probably the easiest way it to open the Local Group Policy Editor in Run:
- Click Search in the Toolbar and type Run
- Type ‘gpedit.msc’ in the Run command and click OK
Components of the Group Policy Editor
The Group Policy Editor window is a list view on the left and a contextual view on the right. When you click an item on the left side, it changes the display on the right to show you details about whatever has been selected on the left.
The top-level nodes on the left are Computer Configuration and User Configuration. If you open the tree for Computer Configuration, you can explore the options available to manage different system behavior features.
For example, under Computer Configuration, Administrative Templates, Control Panel, Personalization, you will see things like Do not display the lock screen on the right-hand side:
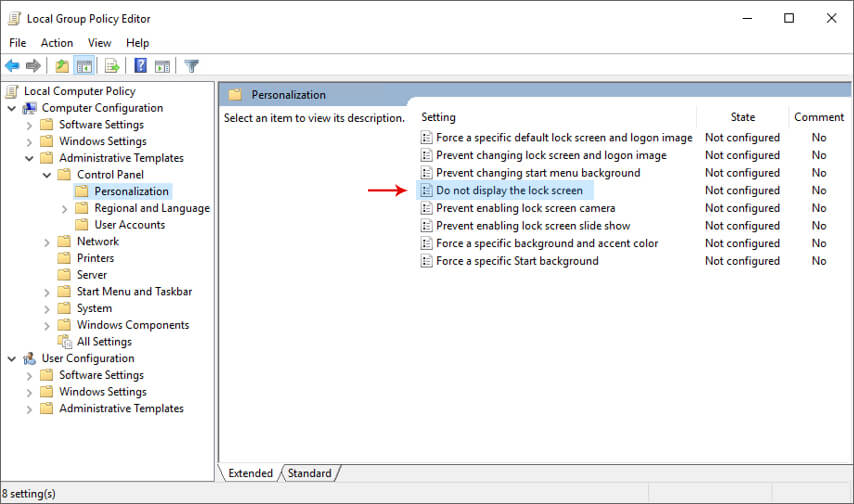
You can edit these settings by double-clicking:
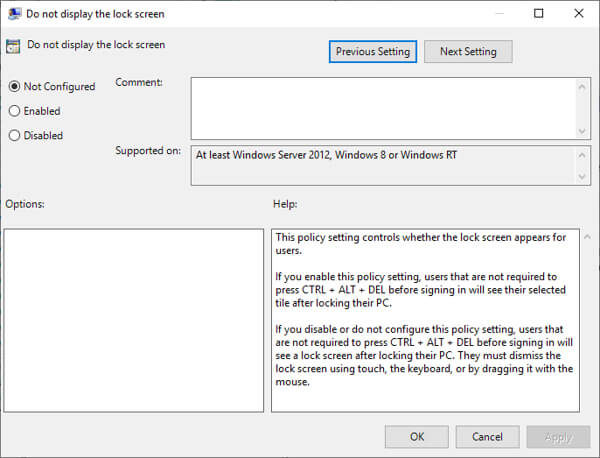
There are hundreds of different settings provided within the Group Policy Editor. Please refer to the Microsoft documentation for a complete list of all available settings.
Local Group Policy Editor Components
The Group Policy Editor consists of two main components which are Computer Configuration and User Configuration:
Computer Configuration: These policies apply to the local computer, and do not change per user.
User Configuration: These policies apply to users on the local machine and will apply to any new users in the future, on this local computer.
These components include sub-categories that administrators can customize to suit their specific needs. For example, within Computer Configuration, administrators can control network settings, Windows components, and system services. The User Configuration component allows administrators to manage user-specific options, such as desktop configurations and application restrictions.
Configure a Security Policy Using the Local Group Policy Editor Console
Once you have an idea of which GPOs you want to set, using Group Policy Editor to make the changes is a straightforward process.
For example, to change a password setting:
-
- In gpedit, click Windows Settings, Account Settings, Password Policy
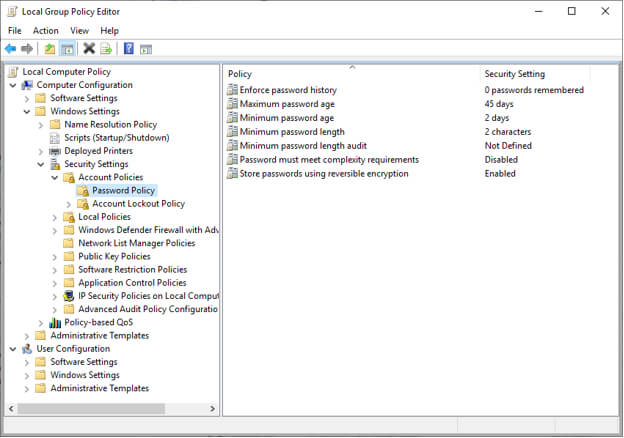
-
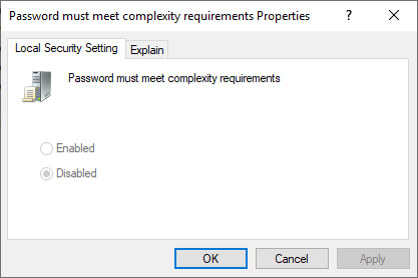
- Select the option for Password must meet complexity requirements
- Click Enabled and then Apply, and your change happens on this local computer. Applying changes to GPOs at the enterprise level is beyond the scope of this article.
How to use PowerShell to Administer Group Policies
Many system administrators are moving to PowerShell instead of the user interface to manage group policies. Here are some examples of the PowerShell GroupPolicy cmdlets:
New-GPO: This cmdlet creates a new unassigned GPO. You can include a name, owner, domain, and more parameters to the new GPO
Get-GPOReport: This cmdlet returns all or the specified GPO(s) that exist in a domain in an XML or HTML file
Get-GPResultantSetOfPolicy: This cmdlet returns the entire Resultant Set of Policy (RsoP) for a user or computer or both and creates an XML file with the results.
This is a useful way to research issues with GPOs. A policy which is set to a certain value, could be overwritten by another GPO, and the only way to find this out is to know the actual values applied to a user or computer.
Invoke-GPUpdate: This cmdlet allows you to refresh the GPOs on a computer
Limitations of Group Policy Editor
The gpedit application is very basic for a tool that is supposed to help secure your entire enterprise. GPO updates occur at different time interval on computers throughout the network or on a reboot. Therefore, the time between your changes and all computers on the network receiving this change is unknown.
It’s crucial to monitor Active Directory for any changes made to Group Policy as often, these changes are the first signs of a cyber-attack, where hackers want to stay in your network for a while, and remain hidden.
Attackers can change local group policies using the same gpedit tool, or PowerShell, which can undo any protections you have enabled on that system. It’s worth noting that gpedit does not have any native auditing built-in, so you need to audit all GPO changes independently to ensure that your enterprise remains secure. One answer to this is to use the Lepide Data Security Platform.
How Lepide can Help
Given the risks associated with Group Policy changes, it is essential that organizations have a structured and proactive approach to Group Policy auditing. The Lepide Auditor for Group Policy makes it easy to instantly see who, what, where and when changes are made, and even allows you to roll back the entire Group Policy Object to its previous state. The Lepide Solution comes with more than 40 predefined Group Policy audit reports and real-time alerts that make light work of what would otherwise be a very manual process.
Below is an example of a report from the Lepide Auditor for Group Policy showing all Group Policy Object Modifications:
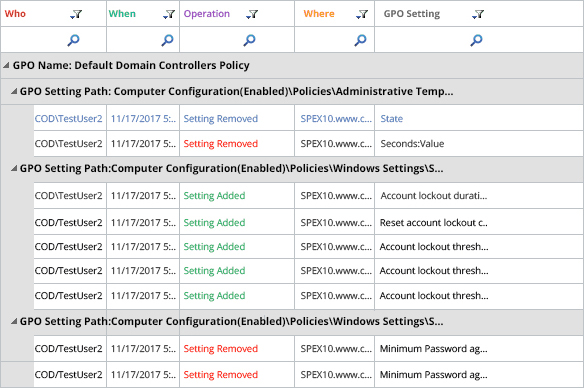
To run this report:
- From the States & Behavior window, select Group Policy Reports, Group Policy Object Modified
- Select a time period
- Click Generate Report
- The report will run and show all modified group policy objects. It can be grouped, filtered, saved and exported
It is also possible to create an alert so that you can be notified as soon as a group policy object is modified and take immediate remedial action if required.


