Last Updated on December 17, 2024 by Deepanshu Sharma

IT administrators need to have visibility over who and when computers were logged into for security and compliance reasons.
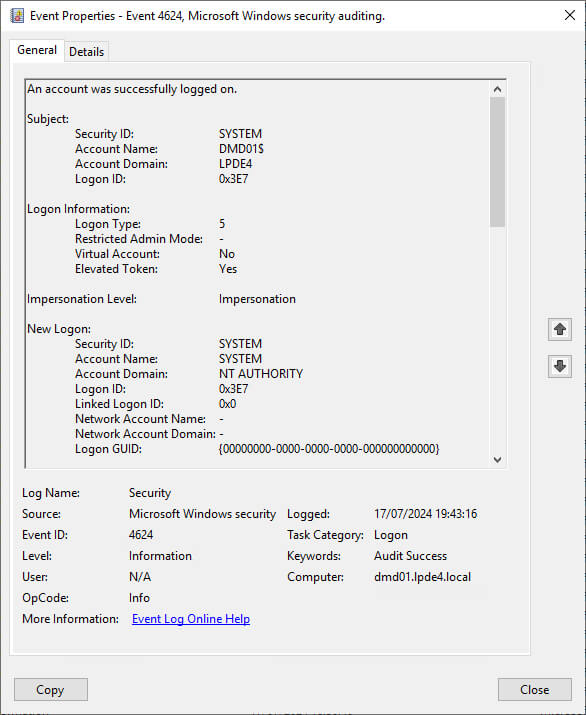
Event ID 4624 is an important event as it records all successful attempts to logon to the local computer regardless of logon type, user location or account type. This event can be linked to logoff events 4634 and 4647 using the Logon ID.
Event Fields Description
The key information that can be derived from Event 4624 includes:
Logon Type: This field reveals the kind of logon that occurred. There are a total of nine different types of logons, the most common logon types are: logon type 2 (interactive) and logon type 3 (network) and 5 (service startup). Any other logon type is a red flag.
New Logon: This section reveals the Account Name of the user for whom the new logon was created and the Logon ID, a hexadecimal value that helps correlate this event with other events.
Download Whitepaper

| Logon Type | Description |
|---|---|
| 2 | -Interactive logon Occurs when a user logs on using a computer’s local keyboard and screen. |
| 3 | +Network logon |
| 4 | +Batch logon |
| 5 | +Service logon |
| 7 | +Unlock logon |
| 8 | +NetworkClearText logon |
| 9 | +NewCredentials logon |
| 10 | +RemoteInteractive logon |
| 11 | +CachedInteractive logon |
Other information that can be obtained from Event 4624 is as follows:
- The Subject section reveals the account on the local system (not the user) that requested the logon.
- The Impersonation Level section reveals the extent to which a process in the logon session can impersonate a client. Impersonation Levels determine the operations a server can perform in the client’s context.
- The Process Information section reveals details surrounding the process that attempted the logon.
- The Network Information section reveals where the user was when they logged on. If the logon was initiated from the same computer, this information will either be blank or reflect the local computer’s workstation name and source network address.
- The Authentication Information reveals information about the authentication package used for logon.
Why Monitor Successful Logons
There are a number of reasons why successful logins need to be monitored and these are explained below:
1. Security Strategy – Auditing successful logons in Active Directory is a key element of identity security and robust data security strategy. To prevent privilege abuse, organizations need to be vigilant about the actions which privileged users are performing and this starts with logons. This can help to detect abnormal and potentially malicious activity. Examples include a logon from an inactive or restricted account, users logging on outside of normal working hours, and concurrent logons to many resources.
2. Operational Needs – Monitoring logons helps to track user activity like user attendance, peak logon times, and so on.
3. Compliance Regulations – Compliance regulations may mandate that successful logon information is recorded.
How Lepide Helps
A more straightforward approach to monitoring successful logons it to use the Lepide Data Security Platform. The Lepide Solution overcomes the limitations of native auditing and provides a simple but comprehensive way to track all the logon/logoff activities of Active Directory users.
The report below is the All Successful Authentications Report, one of the many reports included with the Lepide Active Directory Auditor and shows all successful authentications for a specified time period:
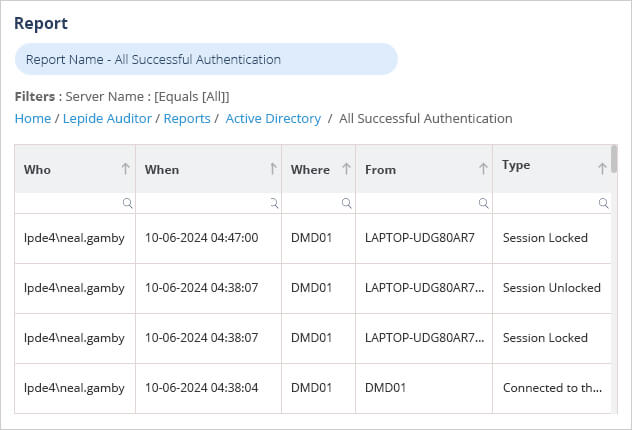
To run the report:
- Select Lepide Auditor, Reports
- Select the All Successful Authentication Report from Active Directory reports
- Specify a Date Range
- Select Generate Report
The report is generated and can be filtered, sorted and exported to CSV and PDF format.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
