Last Updated on December 24, 2024 by Satyendra

Ransomware has grown from a nuisance to one of the most feared cybersecurity threats in the world. It’s not just the technology that has evolved, it’s the strategy, impact, and financial damage that have scaled to alarming levels. As ransomware variants become more sophisticated, knowing what types exist and how they operate can help organizations and individuals better protect themselves. In this blog, we’ll delve into the most common types of ransomware and explore real-world attacks that illustrate just how damaging these cybercrimes can be.
Common Types of Ransomware
Ransomware isn’t a one-size-fits-all type of malware; it comes in various forms, each with its own method of attack and level of impact. Here’s a look at the most common types:
| Year of Attack | Type of Ransomware | Attack Method | Industries Affected | Example |
|---|---|---|---|---|
| 2010 | Locker Ransomware | Locks device, demanding ransom to unlock access. | Healthcare, education, and small businesses. | WinLock |
| 2012 | Scareware | Fakes threats, tricks users into paying for fake protection. | Consumer electronics, online services, and personal finance. | FBI Moneypak |
| 2013 | Crypto Ransomware | Encrypts files, demands ransom for decryption key. | Healthcare, finance, government, and manufacturing. | CryptoLocker |
| 2019 | Double Extortion Ransomware | Encrypts files and threatens to leak data if unpaid. | Finance, healthcare, legal, and critical infrastructure. | Maze |
| 2019 | Ransomware-as-a-Service | Provides ransomware tools for hire, enabling easy attacks. | Any industry, often targeting businesses with less security. | RaaS |
1. Crypto Ransomware
Crypto ransomware encrypts files on a victim’s computer, making them inaccessible without a decryption key. The attackers demand payment, typically in cryptocurrency, to unlock the files. This type of ransomware can target everything from personal devices to critical infrastructure.
- How It Works: Once crypto ransomware gains access to a system, it uses advanced encryption algorithms to lock files. Users often find their files renamed with extensions indicating encryption, along with a ransom note demanding payment.
- Example: CryptoLocker (2013) was one of the earliest and most notorious examples of crypto ransomware. Spread through phishing emails, it encrypted files on Microsoft Windows systems and demanded a Bitcoin ransom in exchange for the decryption key.
2. Locker Ransomware
Unlike crypto ransomware, locker ransomware doesn’t encrypt individual files. Instead, it locks the victim out of their entire system or device. Victims are prevented from accessing their operating system or applications until they pay the ransom.
- How It Works: Locker ransomware locks the screen or the computer’s entire interface. Victims are presented with a ransom demand, typically with a countdown, urging them to pay before their system is permanently disabled.
- Example: WinLock (2010) was one of the early examples of locker ransomware, targeting Windows users by locking their desktops and demanding a ransom via SMS.
3. Double Extortion Ransomware
Double extortion ransomware combines file encryption with data theft. Even if victims have backups and can restore their files without paying the ransom, the attackers threaten to release sensitive information if the ransom isn’t paid.
- How It Works: Attackers steal data before encrypting it. Victims are then given a two-part ultimatum: pay the ransom to regain access to their data, and pay an additional ransom to prevent the stolen data from being published or sold on the dark web.
- Example: Maze (2019) pioneered this tactic, which has since become widely adopted by other ransomware groups. Maze targeted high-profile companies, exfiltrated sensitive data, and threatened to publicly release it unless the ransom was paid.
4. Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service allows individuals with little technical expertise to launch ransomware attacks by purchasing ready-made ransomware kits on the dark web. RaaS operators take a percentage of the ransom collected, creating an entire ecosystem around ransomware.
- How It Works: In this model, ransomware developers sell or lease their ransomware to affiliates who carry out the attacks. The developers provide everything from software to support, in exchange for a cut of the profits.
- Example: REvil (2019) was one of the most notorious RaaS groups, responsible for numerous high-profile attacks, including the Kaseya supply chain attack, which impacted thousands of businesses globally.
5. Scareware
Scareware uses intimidation and fear tactics to coerce victims into paying a ransom, often without actually encrypting files or locking systems. These attacks rely on fake warnings and urgent messages to trick users into believing their computer is compromised.
- How It Works: Victims receive pop-up alerts or messages claiming their system has been infected or compromised. The message demands payment to resolve the issue, but in most cases, no actual malware is present.
- Example: FBI Moneypak (2012) was a well-known scareware campaign that claimed to be from law enforcement, accusing users of illegal activity and demanding payment to avoid prosecution.
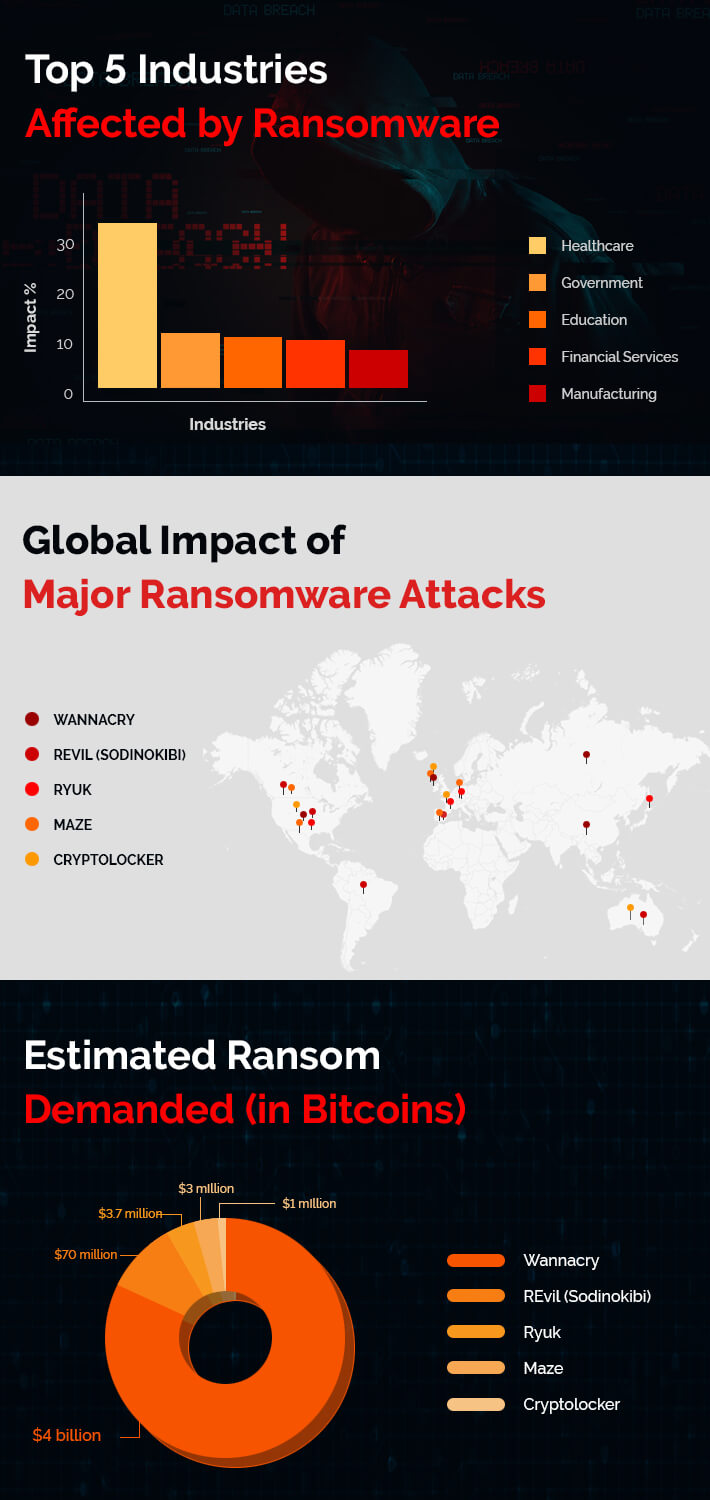
Examples of Ransomware Attacks
Here is an in-depth look at some of the most significant ransomware attacks in history. Each example showcases different methods of attack, targets, and outcomes.
1. BadRabbit
BadRabbit ransomware spread primarily through a fake Adobe Flash update, which was used to trick victims into downloading malicious software. Unlike some other ransomware variants, BadRabbit required human intervention (clicking on a malicious link or downloading a fake update) to infect devices.
The attack primarily targeted entities in Russia and Ukraine, including airports, media companies, and critical infrastructure. BadRabbit bore similarities to NotPetya but used a different encryption technique, specifically focusing on files and MFT (Master File Table) encryption. It was disruptive, but its spread was more contained compared to other ransomware outbreaks.
The attackers demanded payment in Bitcoin, asking for approximately 0.05 BTC (~$285 at the time). The ransom demand escalated if payment wasn’t made quickly.
2. BitPaymer
BitPaymer ransomware was often delivered through phishing campaigns or by exploiting vulnerable Remote Desktop Protocol (RDP) systems. Once inside a network, the attackers manually deployed the ransomware to specific targets, often gaining access to high-privilege accounts.
BitPaymer targeted high-profile organizations, including healthcare and public service sectors. It became notorious for demanding exorbitant ransom amounts based on the organization’s perceived financial ability. For instance, in some cases, BitPaymer ransomware demanded millions of dollars in exchange for decryption keys.
The ransom notes were personalized, with demands sometimes exceeding $1 million. BitPaymer would encrypt files and append unique extensions, often specific to each organization.
3. Cerber
Cerber ransomware spread primarily through phishing emails, malicious attachments, and exploit kits. Its most notable feature was its ability to operate offline, meaning it did not need to communicate with a Command and Control (C2) server for encryption, making it harder to detect.
Cerber became a popular Ransomware-as-a-Service (RaaS) platform, where attackers licensed the software to other cybercriminals in exchange for a share of the profits. It encrypted files on infected systems and added random extensions to the file names. Cerber also featured voice instructions that guided victims on how to pay the ransom.
Cerber often demanded Bitcoin payments, and its RaaS model enabled widespread distribution. Victims were provided with detailed instructions on how to buy and transfer Bitcoin.
4. CryptoLocker
CryptoLocker was distributed through malicious email attachments that appeared to be legitimate files, such as PDF documents or ZIP files. Once the victim opened the file, the ransomware would immediately begin encrypting the system’s files using RSA encryption.
CryptoLocker was one of the first major ransomware strains to use strong encryption, making it nearly impossible for victims to recover their data without the decryption key. During its peak, CryptoLocker infected hundreds of thousands of computers worldwide and caused massive financial losses, particularly in the U.S. and Europe. The FBI estimated that CryptoLocker collected over $27 million in ransom payments before it was eventually taken down in a joint operation.
The attackers demanded ransom payments in Bitcoin, typically around 2 BTC, and threatened to delete the decryption key if the ransom wasn’t paid within a certain time frame. Even after payments were made, many victims did not recover their files.
5. Dharma
Dharma ransomware (also known as CrySIS) is primarily spread through phishing emails and unsecured RDP systems. Attackers typically gain access to networks through weak RDP credentials and then manually deploy the ransomware.
Dharma has evolved into multiple variants over the years, making it one of the most persistent ransomware families. It targets businesses across various sectors, including healthcare, education, and retail. Dharma encrypts files and appends extensions like .dharma, .wallet, or .onion.
The ransom demands are typically modest, with attackers often asking for a few thousand dollars in Bitcoin. However, Dharma’s wide distribution and consistent evolution have made it a significant threat over time.
Download ebook
6. DoppelPaymer
DoppelPaymer ransomware is closely related to BitPaymer and spreads through phishing emails and exploiting vulnerabilities in RDP. Once inside a network, attackers carefully choose high-value targets before encrypting files.
DoppelPaymer became known for its double extortion technique, where attackers would steal data and then encrypt files. Victims who refused to pay the ransom faced the additional threat of having their stolen data leaked publicly. DoppelPaymer has targeted several large organizations, including healthcare systems and local governments, demanding millions of dollars in ransom payments.
Ransom demands can vary, but DoppelPaymer typically asks for hundreds of thousands to millions of dollars, depending on the target.
7. GandCrab
GandCrab was distributed through phishing campaigns, exploit kits, and RDP attacks. What made GandCrab unique was its RaaS (Ransomware-as-a-Service) model, where affiliates would spread the ransomware and share profits with the developers.
GandCrab rapidly became one of the most widespread ransomware families, infecting over 1.5 million systems worldwide. It constantly evolved, with each new version improving its evasion tactics and encryption methods. GandCrab was responsible for attacks on a wide range of industries, including healthcare, finance, and government agencies. Despite its success, GandCrab’s operators announced their retirement in 2019 after reportedly making over $2 billion in ransom payments.
GandCrab’s ransom demands ranged from a few hundred dollars to hundreds of thousands, depending on the target.
8. Locky
Locky ransomware spread through phishing emails containing malicious attachments, such as Microsoft Word documents with macros. Once the user enabled macros, the ransomware would download and encrypt files.
Locky was highly effective in targeting organizations across various sectors, including healthcare and education. It was known for its ability to disable antivirus software and quickly spread across networks. Locky encrypted files and appended the .locky extension, making recovery difficult without the decryption key.
The ransom demands typically ranged from 0.5 to 1 Bitcoin, and victims were directed to purchase Bitcoin and send it to a specific wallet in exchange for the decryption key.
9. Maze
Maze ransomware gained notoriety for its double extortion technique, where attackers would steal sensitive data in addition to encrypting files. If the victim refused to pay the ransom, the attackers would threaten to release the stolen data publicly.
Maze was responsible for several high-profile attacks, including those on Cognizant, Xerox, and the city of Pensacola. The group behind Maze was highly organized and targeted various industries, including healthcare, finance, and government institutions. In 2020, the operators of Maze announced they were ceasing operations, but the double extortion technique they had popularized continued to be adopted by other ransomware groups.
Maze typically demanded ransom payments in Bitcoin or Monero, with demands ranging from hundreds of thousands to millions of dollars depending on the size and value of the target. The ransom note provided victims with a link to a dedicated leak site where they could verify that their data had been stolen and would be published if the ransom was not paid.
10. MedusaLocker
MedusaLocker is typically spread via phishing emails containing malicious attachments. Once the ransomware gains access to a network, it begins encrypting files and displaying a ransom note.
MedusaLocker is notorious for targeting small and medium-sized businesses across a wide variety of sectors. It uses AES encryption to lock files and demands a ransom in exchange for the decryption key. MedusaLocker also spreads laterally across networks, enabling it to infect multiple systems within an organization.
The ransom demands vary, but typically MedusaLocker requests payments in Bitcoin, ranging from several thousand to tens of thousands of dollars. It often provides detailed instructions on how victims can purchase Bitcoin and transfer it to the attacker’s wallet.
11. NetWalker
NetWalker was spread through phishing emails or by exploiting vulnerabilities in remote desktop services. Like other ransomware, it encrypts files and demands payment for the decryption key. NetWalker also employed the double extortion method, stealing sensitive data and threatening to publish it if the ransom was not paid.
NetWalker primarily targeted government organizations, healthcare institutions, and educational facilities. In 2020, during the COVID-19 pandemic, NetWalker took advantage of the chaos to attack healthcare organizations. The FBI eventually dismantled the NetWalker infrastructure, but not before it had caused significant damage globally.
NetWalker demanded large sums, often in the range of hundreds of thousands to millions of dollars, depending on the target. The attackers used a sophisticated leak site where stolen data would be published if the ransom wasn’t paid.
12. NotPetya
NotPetya initially spread through a compromised Ukrainian tax software application and used the EternalBlue exploit (also utilized by WannaCry) to propagate across networks. Unlike typical ransomware, NotPetya was classified as a wiper because it encrypted the entire hard drive but was designed to cause damage rather than recoverable encryption.
NotPetya caused massive disruption, particularly in Ukraine, where it crippled government agencies, financial institutions, and businesses. Its effects were felt globally as it spread to multinational corporations, including shipping giant Maersk and pharmaceutical company Merck, leading to billions of dollars in losses.
Although NotPetya demanded a ransom in Bitcoin for decryption, its primary intent was likely to cause irreversible damage rather than extort money. Even if the ransom was paid, recovery of the data was impossible due to the destructive nature of the encryption.
13. Petya
Petya ransomware was initially spread via phishing emails containing malicious attachments. Unlike other ransomware that encrypts files individually, Petya encrypted the Master File Table (MFT), making it impossible to access any files on the system.
Petya primarily targeted organizations, spreading across networks and encrypting the MFT, which rendered entire systems unusable. While it started as a typical ransomware strain, later versions of Petya (such as NotPetya) took on more destructive features, acting more as wiper malware than traditional ransomware.
Petya demanded ransom payments in Bitcoin, typically in the range of 0.9 to 1.5 Bitcoin, and threatened to permanently delete the encryption key if the ransom wasn’t paid within a specified time frame.
14. REvil (Sodinokibi)
REvil ransomware (also known as Sodinokibi) was spread through phishing campaigns, RDP vulnerabilities, and exploit kits. It became particularly notorious for using the double extortion tactic, stealing data before encrypting files.
REvil targeted a wide range of industries, including finance, retail, and healthcare, demanding massive ransom payments. One of its most infamous attacks was on Kaseya in 2021, where thousands of businesses were affected by a supply chain attack that leveraged Kaseya’s software. The group behind REvil was responsible for numerous high-profile breaches, including attacks on food giant JBS and celebrity law firms.
REvil often demanded millions of dollars in ransom, and the group was known for negotiating payment terms with victims. In some cases, they auctioned stolen data on the dark web if the ransom wasn’t paid.
15. Ryuk
Ryuk ransomware spread primarily through phishing emails and exploited RDP systems. It often targeted high-value organizations, manually infiltrating networks and disabling system backups before deploying the ransomware.
Ryuk was responsible for several high-profile attacks, including on hospitals, municipal governments, and large corporations. The group behind Ryuk is believed to have ties to the North Korean Lazarus Group, and their attacks caused widespread disruption, particularly in the healthcare sector. Ryuk’s ability to disable backups made recovery nearly impossible for victims who didn’t have other mitigation strategies in place.
Ryuk was known for demanding enormous ransom payments, sometimes exceeding $10 million, depending on the size and revenue of the targeted organization.
16. SamSam
SamSam ransomware was deployed manually by attackers after gaining access to a network through weak credentials or unpatched vulnerabilities in RDP. Once inside, attackers would carefully choose which systems to encrypt.
SamSam was responsible for targeting high-profile entities, including the city of Atlanta in 2018, which suffered weeks of disruption after its systems were encrypted. Other targets included healthcare facilities, government organizations, and educational institutions. The unique nature of SamSam’s manual deployment allowed attackers to tailor each attack for maximum disruption.
SamSam typically demanded ransoms in Bitcoin, with payments ranging from a few thousand dollars to over $50,000. The group behind SamSam made over $6 million in ransom payments before being disrupted by law enforcement.
17. WannaCry
WannaCry exploited the EternalBlue vulnerability in Microsoft Windows systems to spread rapidly across networks. It was self-propagating, meaning that once it infected a system, it could automatically spread to other vulnerable systems without user interaction.
WannaCry was one of the most devastating ransomware attacks in history, infecting over 200,000 systems across 150 countries within a matter of days. It caused widespread disruption, particularly in the healthcare sector, where the UK’s National Health Service (NHS) was severely impacted. WannaCry encrypted files and demanded ransom payments, though it was later discovered that the malware contained a kill switch that effectively halted its spread.
The attackers demanded Bitcoin payments, typically around $300, with the threat of deleting encrypted files if the ransom wasn’t paid within a certain timeframe. Despite the relatively low ransom demands, the global disruption caused by WannaCry was estimated to exceed $4 billion.
Conclusion
Ransomware attacks serve as a harsh reminder of how vulnerable our digital world can be. But as alarming as these threats are, they also offer us a chance to learn. Each attack tells a story of weaknesses exploited and lessons learned. While ransomware will continue to evolve, so must our defenses. By staying informed about different ransomware types and the tactics behind high-profile attacks, we can take the steps needed to reduce risks and prevent our data from becoming collateral in this global cyberwar. Preparedness is our best defense.
If you want to know how Lepide’s Data Security Platform can help you protect your organization against Ransomware attacks, book a demo with one of our engineers today!

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
