Last Updated on December 13, 2024 by Deepanshu Sharma

Trust is a luxury that organizations can no longer afford. It’s a new era of cyber threats that develop rapidly, and navigate gaps in traditional security solutions to steal data and resources.
This is where Zero Trust Architecture (ZTA) comes in, a security model that completely dismisses the historical “trust but verify” principle in favor of “never trust, always verify”. Since AD is used by many enterprises to address identity and access challenges, incorporating Zero Trust is not a trend, but a must.
However, when does an organization start implementing Zero Trust to get there without having to rebuild its structure from scratch? This blog goes into detail about what Zero Trust is, why it is vital in securing Active Directory, and how you can begin to implement this structure of security. Let’s get started.
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) refers to the framework or structure used by organizations to implement zero trust principles in their IT environment. In Zero Trust, all users, devices, applications, or networks are considered to be threats that will attempt to compromise the resources on a network. They all have to be verified, nobody is exempted from verification.
Unlike traditional perimeter-based security models that focus on keeping external threats out, Zero Trust Architecture operates on three key principles:
Verify Explicitly: Always validate and approve each access attempt based on all contextual data, user credentials, physical location, device status, and many others.
Use Least Privilege Access: Only grant privileges to a user based on the nature of their work to minimize exposure in the event of a breach.
Assume Breach: Implement regular security checks and verify their effectiveness with the notion that the organization’s security will be breached or perhaps has already been breached.
This proactive, encompassing strategy will help organizations to effectively protect their property in a complex and constantly evolving global environment.

Why is Zero Trust Security Important for Active Directory?
Active Directory is essentially the central component of most organization’s computing platforms. It is responsible for identities, permission, and the levels granted to individuals on the resources and, therefore, an excellent attack point. Anytime an attacker gets a foothold in AD, they have an ocean of permissions through which to slide across the network, achieve privilege escalation as well as wreak havoc.
Here’s why Zero Trust is essential for securing Active Directory:
1. Reduces Over-Reliance on Perimeter Security:
In standard AD configurations, an organization maps a perimeter that is meant to safeguard the internal assets. In the current world of work that is characterized by remote connections and integrated cloud systems, this perimeter is only vaguely defined at best. Zero Trust mitigates this by ensuring that every request for access within the network is considered as a threat from within or outside the network.
2. Mitigates Lateral Movement:
A stolen AD credential serves hackers as a master key to other networks and systems in an organization. Zero Trust compartmentalizes movements by insisting on proper identification and monitoring of users and devices as they navigate through an organization’s digital infrastructure.
3. Protects Against Insider Threats:
It is important to note that threats may originate from both insiders as well as outsiders. Hackers can take advantage of disgruntled employees, human error, or compromised insider accounts. Users are only loaded with the right level of access to be able to perform a function, reducing the risk factor if an account is compromised.
4. Enhances Visibility and Control:
One more thing that a lot of people often fail to notice is that Zero Trust is very dependent on observation and reporting. For AD, this means continuous monitoring of user sign-ins, permission updates, and suspicious actions, helping organizations to gain insights and act on them much more quickly.
How to Implement Zero Trust Architecture in Active Directory
Transitioning to Zero Trust isn’t a single step, it’s a journey. Below are actionable steps to implement Zero Trust for Active Directory effectively:
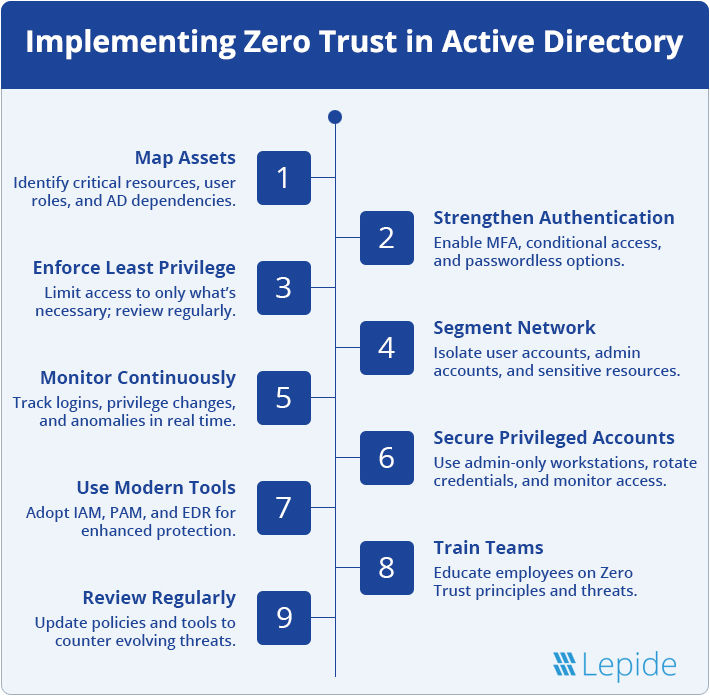
1. Map Your Assets and Dependencies
The first step in any Zero Trust strategy is understanding what you’re protecting. For Active Directory, this means:
- Identifying critical assets and resources.
- Mapping user roles and their required access levels.
- Documenting all applications and systems dependent on AD.
This baseline allows you to create tailored access policies and prioritize your security efforts.
2. Strengthen Authentication Mechanisms
Authentication is the cornerstone of Zero Trust. For Active Directory, consider these measures:
- Implement Multi-Factor Authentication (MFA): Require users to verify their identity through a second factor, such as a one-time code or biometric scan.
- Use Conditional Access Policies: Dynamically adjust access requirements based on location, device compliance, and risk scores.
- Adopt Passwordless Authentication: Replace passwords with more secure options like biometrics or hardware tokens.
3. Enforce Least Privilege Access
Audit your AD permissions to ensure that users only have access to the resources they need. Implement role-based access controls (RBAC) and regularly review permissions to prevent privilege creep.
4. Segment Your Network and Resources
Network segmentation prevents attackers from moving freely if they breach one part of your system. For Active Directory:
- Divide your environment into logical segments, such as separating user accounts, administrative accounts, and sensitive resources.
- Use virtual LANs (VLANs) or microsegmentation to isolate critical assets.
5. Implement Continuous Monitoring and Analytics
Zero Trust thrives on data. For AD, this means:
- Enable Audit Logs: Capture all login attempts, privilege escalations, and configuration changes.
- Monitor Anomalous Behavior: Use machine learning or analytics tools to flag unusual activities, like logins from unknown locations or sudden permission changes.
- Automate Alerts: Ensure your system notifies administrators immediately when suspicious behavior occurs.
6. Protect Privileged Accounts
Administrative accounts are a top target for attackers. To secure them
- Use Dedicated Admin Workstations (DAWs): Restrict administrative tasks to hardened, isolated machines.
- Enforce Privileged Access Workstations (PAWs): Create a secure environment specifically for privileged operations.
- Rotate Admin Credentials Regularly: Change passwords for privileged accounts frequently to limit the impact of credential theft.
7. Leverage Modern Tools and Technologies
Modern security tools can supercharge your Zero Trust efforts. For Active Directory, consider:
- Identity and Access Management (IAM) Solutions: To centralize user authentication and authorization.
- Privileged Access Management (PAM): To manage and monitor administrative accounts.
- Endpoint Detection and Response (EDR): To detect and neutralize threats at the endpoint level.
8. Educate and Train Your Team
Zero Trust isn’t just a technical shift; it’s a cultural one. Train your employees to recognize security risks and the importance of following Zero Trust principles.
9. Regularly Review and Update Policies
Zero Trust is a dynamic framework that evolves with your organization. Continuously assess your policies, tools, and procedures to ensure they remain effective against emerging threats.
Conclusion
Implementing Zero Trust Architecture for Active Directory may seem daunting, but it’s a necessary evolution in today’s security environment. By assuming nothing and verifying everything, organizations can significantly reduce the risks associated with cyberattacks, insider threats, and credential misuse.
Lepide Data Security Platform simplifies the journey to zero trust with it’s Active Directory Security solution, enabling you to audit, protect, and analyze your AD environment effectively. With continuous monitoring, real-time alerts, and actionable insights, Lepide ensures your organization stays ahead of threats.
Take the first step towards a more secure AD. Schedule a demo with us to see how Lepide can help secure your IT environment with ease.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
