Last Updated on December 20, 2024 by Satyendra

In this post, I’ll explain how Privileged Access Management (PAM) in Windows Server 2016 can be used to protect privileged credentials, and provide an outline of the solution’s architecture.
It’s common to find IT staff assigned permanent domain administrator privileges, or others that are local administrators on devices used for managing the domain and sensitive systems, making it easier for malicious users to hack line-of-business systems. Adding users to privileged domain groups is often the easiest way to expedite system access, especially when there’s no delegation set up in the domain. I.e. helpdesk staff might be granted permissions to create new AD users and reset passwords in designated Organizational Units (OUs), rather than be given access to the entire domain. But while implementing the Principle of Least Privilege is a best practice worth investing in, there will always be occasions where users must be granted access to privileged domain groups.
Privileged Access Management
Windows Server 2016 includes several new technologies out-of-the-box to facilitate Just-In-Time (JIT) Administration, or Privileged Access Management as Microsoft refers to it, where users are granted elevated privileges for a restricted period to improve domain security.
Bastion Forest and Shadow Security Principals
A new type of cross-forest trust (PAM trust) has been added so that organizations can set up a new Active Directory (AD) forest, or bastion forest, where privileged accounts are isolated from what Microsoft considers to be forests that might already be compromised. A further advantage of requiring a bastion forest is that AD schema changes required to support PAM can be performed in the bastion forest, while the existing forest remains untouched.
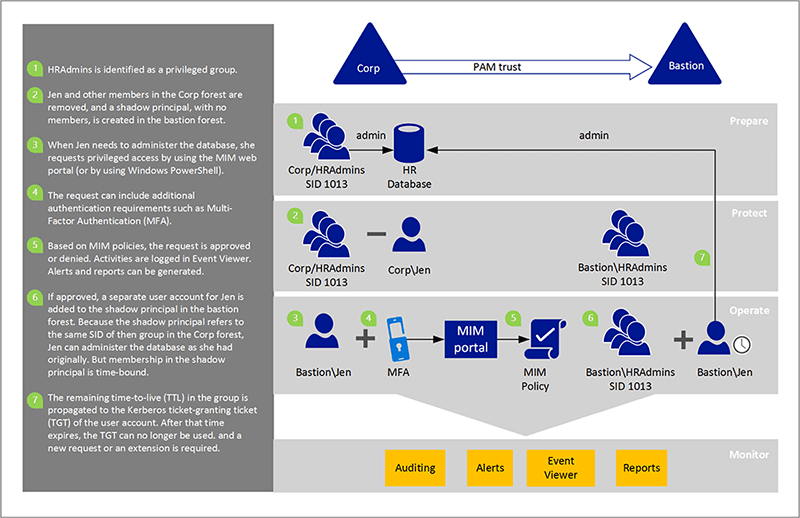
The bastion forest contains the same groups as the organizations’ existing forest, or shadow security principals, because the PAM trust allows Security Identifiers (SIDs) to be reused. Users can be identified as candidates for group membership, and when permitted via an approved workflow, a duplicate account is created for the user in the bastion forest, added to the shadow security principal, which gives the duplicate account access to resources in the existing forest. Additionally, the bastion forest user is assigned a time-to-live (TTL) value for group membership, after which time, full membership is revoked and the user is returned to candidate status.
Workflows and Microsoft Identity Manager
Users need to request permission to move from group candidate to full member. This process is controlled using Microsoft Identity Manager (MIM) workflows, where a manager might be required to give permission for a user to receive full group membership status, and certain conditions might also need to be met, such as using a virtual smart card or PIN to log in.
The bad news is that MIM is a standalone product that needs to be licensed separately from Windows Server 2016. But Azure AD (AAD) Premium includes licenses for Microsoft Identity Manager 2016, and AAD Premium is also part of Microsoft’s Enterprise Mobility + Security package, so there are different ways to get MIM.
Another way to get a handle on which users have access to privileged domain groups in your environment, is to use Lepide Data Security Platform, which offers granular reporting on changes made to Active Directory.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
