Privileged user accounts are the ultimate goal for cyber attackers. Once attackers have privileged access, stealing sensitive information is a breeze. In many cases, attackers patiently claw and scrape their way up the access ladder from low-level accounts up to administrative ones.
IT administrators regularly face challenges identifying who has privileged access to the Active Directory environment, as well as managing new privileged users. The goal of this blog post is to help educate you on some of the methods a user can utilize to gain privileged access and compromise security. Once you know this, you can take steps to better manage your Active Directory privileged users, with the goal of reducing the volume and severity of data breaches.
Download Free Tool

Why Is Managing Privileged Access in Active Directory Important?
Privileged user accounts have unrestricted access to all critical servers, applications, and databases in an organization. They also have permission to add, remove or manage user profiles. With this in mind, it’s easy to see how such accounts can be misused.
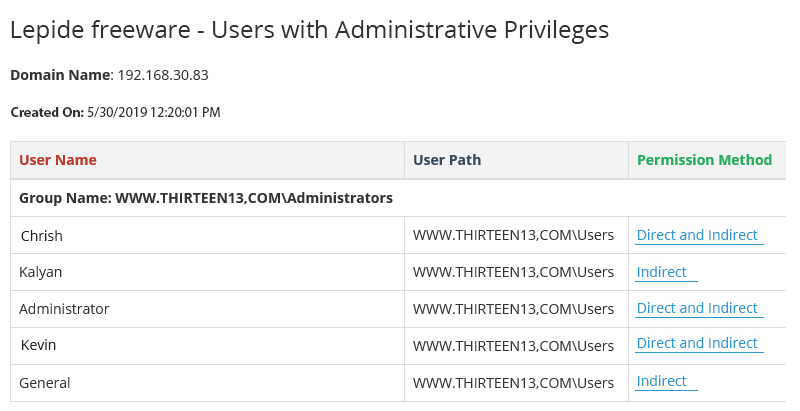
Privileged accounts are those which are assigned comparatively more permissions than a normal user account. To address any potential issues with security, a systematic method is required to identify users with excessive privileges. The best way to create a list of privileged users is by going through Active Directory Users and Computers and the Group Policy Management Console.
How to Manage Privileged Access in Active Directory?
Some strategies, such as being a member of the Domain Admins group, are a direct step towards gaining and managing access to Active Directory. Whilst attaining Local Admin access over a Domain Controller is more of an indirect approach. Let’s take a deeper look at each strategy and see where you should be focusing your efforts.
- Restrict Privileged Access to Domain Groups
- Configure Group Policy Objects to restrict Administrator accounts on Domain Controllers
- Secure Built-in Administrator accounts in Active Directory
- Delegating Individual NT User Rights
- Managing Active Directory Domain Service Accounts
- Implement Privileged Access Management
- Delegate Everyday Administrative Tasks
1. Restrict Privileged Access to Domain Groups
In each of the Active Directory domains, an Administrator account is created as part of the creation of the domain itself. This account is, by default, a privileged member of the Domain Admin and Administrator group. Below is a list that highlights members of Domain Groups that have default privileged access to Active Directory:
- Enterprise Admins
- Domain Admins
- Schema Admins
- Built-in Administrators
There should really be no permanent members of any of the groups mentioned above. Only the built-in administrator account should remain under the Domain Group. If a new user account is added, restrictions must be put in place to prevent the account from logging on from a computer with lower trust levels.
2. Configure Group Policy Objects to restrict Administrator accounts on Domain Controllers
Group Policy Objects can be configured to restrict privileged access on Domain Controllers. To do this, navigate to Computer Configuration\Policies\Windows Settings\Security Settings\Local Settings\User Rights Assignments. To manage privileged access in GPOs, you must do the following:
- Deny network access to the computer
- Deny logon as a batch job
- Deny logon as a service
- Deny logon through Remote Desktop Services
3. Secure Built-in Administrator accounts in Active Directory
Perform the following steps to secure the inbuilt Administrator accounts.
- Open ‘Active Directory Users and Computers’.
- Navigate and locate the user, which you want to manage.
- Right-click on any of the accounts with Administrator rights and click ‘Properties’.
- Next, click the Accounts tab and select ‘Account is sensitive and cannot be delegated’.
Managing privileges for built-in Administrator accounts helps to prevent attacks that leverage the delegated credentials of an account.
4. Delegating Individual NT User Rights
If you grant individual rights to users on Domain Controllers, rest assured that privileges, such as ‘Create global objects,’ are carefully monitored. In situations like these, it is advisable to grant temporary access to a highly-privileged group rather than permanent access to a specific user. PowerShell Just-Enough Administration (JEA) can also be used to restrict the permanent access users have to Active Directory objects.
5. Managing Active Directory Domain Service Accounts
Managing Active Directory Domain Service accounts may involve keeping highly-privileged Active Directory groups vacant most of the time. However, you must implement a mechanism that allows you to populate other groups whilst keeping Active Directory secure.
Create a set of discreet management accounts that are used solely to populate privileged Active Directory groups. To do this, follow the below steps:
- Create an Organizational Unit structure that separates privileged accounts from standard user accounts.
- Create an Active Directory group containing users that are allowed to enable and disable the management accounts.
- Implement strict controls on these accounts.
- Set permissions on the Admin object to allow the management accounts to manage privileged groups.
6. Implement Privileged Access Management
Windows Server 2016 introduced a variety of new features that allow organizations to gain control of compromised Active Directory forests and implement privileged access management (PAM) to secure Active Directory. This is done through Just-In-Time (JIT) administration instead of distributed access. Some of the benefits include password management, workflow, session management, pass-the-ticket attack prevention, and more.
7. Delegate Everyday Administrative Tasks
By now, if you have removed user access to highly-privileged groups, you will now need to delegate permissions to other users to maintain your Active Directory environment. Routine tasks, such as resetting passwords, adding new user accounts, or modifying group membership, can all be achieved without granting access to any privileged Active Directory groups. It can also be done by placing users in separate Organizational Units that do not contain accounts with privileged access.
The Final Verdict
Securing your Active Directory should be one of your main priorities as an organization. In situations where you must manage privileges to your users, make sure that you are minimizing the risks of potential privilege abuse. We hope this article gives you some more information on the right methods and best practices you can follow when managing privileged access in Active Directory.
If you want to find out who your privileged users are in Active Directory, try Lepide’s free tool to get a list of admin users in AD.