Last Updated on December 20, 2024 by Satyendra

Remote working and COVID-19 have accelerated the use of Microsoft Teams over the last 12 months. As a collaboration and sharing platform, MS Teams has been a savior to many remote working teams. However, not unlike other collaboration and sharing platforms, MS Teams does have a number of security vulnerabilities that security and IT teams need to understand and address.
In this blog, we will go through what MS Teams is, the benefits and risks, a few ways you can use it, and (most importantly) how to use it securely.
What is Microsoft Teams?
Historically, there has been a great deal of confusion over exactly what MS Teams is and how it can be used. Some believe it to be just a chat tool, others just a more advanced version of Skype for Business. Microsoft Teams is far more powerful than this.
Microsoft Teams is essentially a competitor to Slack. Teams combines persistent workplace chat, video meetings, file storage and collaboration, and application integration. It has a whole host of features and integrations to enable remote teams (or even on-premise teams) to work closely together and collaborate more easily.
MS Teams is available for most licenses of Office 365, which makes it widely used in both business and corporate settings.
MS Teams is not a data store. Teams is the front end that sits on top of the critical Office 365 infrastructure and data stores and helps users easily communicate, access, and share data. When a new Team is created, a new security group is created in Azure AD with the Team members. A new hidden mailbox is created in Exchange Online, a new site is created in SharePoint Online, and files when shared through private chats are uploaded to OneDrive.
All of this is going on behind the scenes, unbeknownst to the user.
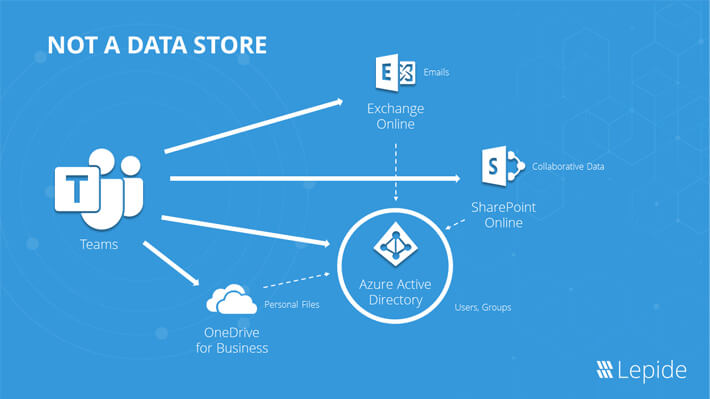
How Microsoft Teams Works
How to Use and Install Microsoft Teams
Using MS Teams requires getting to know some of the lingo. Social media users will be familiar with some of the terminology, including emojis, Stickers, and Gifs. Before we get into the nitty-gritty, though, we need to understand exactly how Teams works.
When you create a team in MS Teams, you also automatically create a SharePoint site, OneNote, and Office 365 group on the backend. Teams acts as a frontend for these backend processes.
When you open up the Teams interface, you should familiarize yourself with the app bar on the left-hand side.
Here you will find your notifications, chats, teams you are a member of, and the files you have access to. Meetings from your Outlook calendar are also synced with Teams to help you keep on top of your schedule.
When the Teams icon is selected, we can see which teams a particular user is a member of. Within a team, there could be multiple channels. Channels are dedicated sections within teams that you can organize chats and files within. Users can create new channels or hide channels they don’t want to see.
Within the channel, there are multiple tabs to select from, including conversations, files, notes, and more. Files is the directory for the SharePoint site where you can access files or add files yourself. Integrations are available so that you can add tabs from your other resources, such as a CRM.
You will need to have an Office 365 license to install MS Teams. Those with an Enterprise license can invite external users to their Teams channels through guest access. Teams can be installed on any device, so it is recommended that you have teams installed with all devices that you use to access corporate files.
If you are an Enterprise Teams customer and you need to roll it out throughout the entire organization, Microsoft does have guidelines that you can follow to do this successfully.
How to Set Permissions in Microsoft Teams
Ensuring that the right people have access to your resources is the most critical part of the deployment. Most security threats involving MS Teams exist due to misconfigurations or elevated privileges. If you’re a team owner, you have the ability to set permissions within your team. Here’s how:
- Go to “More options” – “Manage team”
- In the Settings tab, you can set the member permissions and the guest permissions, as well as a host of other permissions settings. You’ll want to limit the permissions as much as possible to avoid potential privilege abuse.
The Benefits of using Microsoft Teams
Microsoft Teams is incredibly easy to set up and get using, and it’s free for Office 365 users. The cross-collaboration and sharing capabilities make it a viable option for teams that are working remotely to stay on top of their work and up to date with joint projects and other team members. Users can share files with each other, schedule tasks, discuss work and more.
Is Microsoft Teams Secure?
However, as with any sharing platform, it’s not without security risks. MS Teams can make use of the security and configuration of Azure AD through an integration, but this security is very complex and often easily exploited by attackers. Quite often, the complexity of the security and configuration settings can inhibit collaboration, which essentially takes away all the benefits of using Teams in the first place.
Mostly, the risks of MS teams can be overcome through consistent and proactive monitoring to ensure that users aren’t misbehaving and that permissions aren’t sprawling out of control.
Microsoft Teams was designed in accordance with the Trustworthy Computing Security Development Lifecycle (SDL), a key component of Microsoft’s Trustworthy Computing Initiative.
The SDL helps Microsoft develop products with security and privacy in mind. For example, using the SDL will help to ensure that code is examined for known security risks before it can be used in production.
Below are some of the other ways that Microsoft Teams helps to keep your data secure;
End-to-end encryption (E2EE)
For private calls, Teams uses end-to-end encryption on voice, video, and screen-sharing data, and only the recipient is able to decrypt the data. However, both parties will need to enable the encryption for it to work. In this scenario, not even Microsoft themselves can intercept and read the data.
Azure Active Directory (Azure AD)
Azure AD provides a secure directory service, which administrators can use to manage identities, including permissions for users, groups and roles. It provides single sign-on, multi-factor authentication, and conditional access policies.
Transport Layer Security (TLS)
TLS and other industry-standard technologies are used by Microsoft Teams to secure data, both at rest and in transit. This includes messages, documents, meetings, and other information. To authenticate a connection between two users, TLS uses certificates issued by the Certificate Authority. This helps to prevent intrusions like man-in-the-middle attacks, which allow threat actors to intercept connections and steal sensitive data while in transit.
Compliance standards
Microsoft ensures compliance with the following standards; GDPR, HIPAA, ISO 27001, ISO 27018, SSAE16 SOC 1 and SOC 2 and EU Model Clauses (EUMC).
Communication monitoring
Administrators have the ability to monitor conversations in Microsoft Teams. They can set up keyword alerts so that they are informed anytime a specific word is used. This capability can aid administrators in solving security issues more swiftly. However, beyond keyword alerts, communication monitoring must be carried out manually, and with the consent of the users.
Activity reports
The Teams Activity Report allows administrators to monitor activity relating to both the entire business and specific users. Global admins, product-specific admins (Exchange and SharePoint), and users with the “report reader” role can all access the report. The reports include information such as the total number of meetings a user has organised and attended, the amount of time users spend using the Teams Chat facility, and the types of activities that are performed.
Supervised chats
A feature called “supervised chat” can be used to prevent users from starting private chats unless certain members are included. It is intended to be used by educational institutions to stop pupils from starting private chats without a teacher present.
Microsoft Defender
Microsoft Defender is used by Teams to protect your organization from inadvertently sharing malicious files. Defender provides a “safe links” feature to help users decide which links they can trust, and which are potentially malicious. Likewise, the “Safe Attachments” feature found in the Teams admin portal can search for and block potentially malicious attachments.
Sensitivity labels and eDiscovery
Using sensitivity labels, administrators can control access to sensitive content created within Teams. Sensitivity labels and their corresponding policies can be configured in the Microsoft Purview compliance portal. The eDiscovery feature will also help to discover potential privacy and security issues in your Teams content.
Microsoft Teams Best Practices
Some general best practices are as follows:
- Create teams that represent your organizational structure, such as Marketing, Sales, Finance and so on.
- Within each team, create channels for different projects to help direct the conversation and keep everything focused.
- You should allow users to create teams as long as you monitor them.
- Integrate with your CRM and other technology that you use.
- Use chatbots for reminders about daily activities and upcoming tasks.
More specifically, here are some security best practices you can follow to reduce threat risk:
- Make use of multi-factor authentication to make signing on more secure.
- Implement a policy of least privilege or zero trust to limit access.
- Ensure you are able to discover and classify sensitive data being shared on Teams.
- Audit when files are shared outside of the organization.
- Ensure that files aren’t being downloaded onto unmanaged devices.
Microsoft Teams Security Tips
Fortunately, the Global security settings in Office 365 will cover most of Teams’ features. After all, file-sharing in Teams is done through SharePoint and email communication is sent via Exchange Online. OneDrive is used for storage, and authentication and authorization is handled by Azure AD. However, even if you have properly configured the relevant Office 365 security settings, there is still more work to do to ensure that your Teams implementation is secure.
1. Manage Applications
As mentioned, it is possible to extend the functionality of Teams by installing additional applications. Some of these apps are provided by Microsoft, some are provided by third-party vendors, and organizations can even build their own bespoke applications. Naturally, third-party applications pose the greatest security risk. Fortunately, administrators have the option to control which apps can be installed via the Manage apps page in the Teams admin center. They can also adjust the permissions to determine which apps can be used by which users.
2. Create Security Groups
By default, any user with an Exchange Online mailbox can create a team and become a team owner. It would be a good idea to place restrictions on who can and cannot create new teams. The simplest way to do this is to create an Office 365 group that has permissions to create new groups, and thus new teams. Any users who are permitted to create new teams can be assigned to these groups. From within these groups, you can specify whether users are able to communicate with individuals outside the organization, and which users can access and share files and meeting content. It would also be wise to ensure that all users know how to create private channels and limit the number of users in those channels, which will enable them to communicate and share confidential data in a more secure manner.
3. Limit Guest Access
In the Teams admin center, you can configure the Guest access settings to restrict the level of access granted to guest users. It is probably a good idea to either leave guest access disabled by default, or enable it, but ensure that they are granted the least privileges they need. Since guest access is typically granted to clients, you may want to limit their access to features such as video conferencing and screen sharing.
4. Enable/configure additional O365 security features
Office 365 provides a number of additional security features that can help to secure your Teams deployments, some of which include:
Advanced Threat Protection (ATP): ATP is an advanced email filtering solution that helps to protect your mailbox from malware. ATP Safe Links can detect potentially malicious URLs in emails, and ATP Safe Attachments can detect potentially malicious attachments.
Data Loss Prevention (DLP): The O365 DLP feature can help to identify sensitive data such as Social Security or credit card numbers to prevent unauthorized sharing of this data. As a part of O365’s built-in data classification feature, you can enable Automatic labeling to ensure that sensitive data is automatically classified, as and when it is found. It should also be worth noting that you can use a third-party data discovery and classification solution, which may be a preferred option if you are using a third-party auditing solution.
Automated backups: Office 365 provides automatic backups of your data to OneDrive, or a storage location of your choice.
5. Monitor User Activity
As with other Office 365 products, you can monitor all user activity within Teams, which includes user logins, permission changes, team membership changes, installation of apps, and any file-sharing that takes place across public and private channels. Again, it is entirely possible to use a third-party auditing solution, which will provide a number of additional features that might not be available with the native O365 auditing tools.
6. Implement Data Management Policies
To maintain control over your organization’s data in Teams, it is crucial to implement data management policies. Define clear guidelines on data retention, deletion, and archiving to ensure compliance with regulatory requirements and protect sensitive information from unauthorized access.
Consider implementing the following data management policies:
- Establish guidelines for file sharing, specifying which files can be shared externally and internally.
- Enable version control to track and manage document revisions effectively.
- Educate users about the importance of secure file sharing practices and regularly remind them to review and update permissions as needed.
7. Data Access Control for Teams
Controlling data access is vital to prevent unauthorized disclosure or modification of sensitive information within Teams. Implementing appropriate access controls helps mitigate the risk of data breaches and ensures that only authorized individuals can view or modify data.
Here are some best practices for data access control in Teams:
- Regularly review and update user roles and permissions to align with the principle of least privilege.
- Leverage Azure Active Directory groups to streamline access management and simplify permissions assignment.
- Utilize sensitivity labels and data loss prevention (DLP) policies to enforce additional security controls and prevent data leakage.
- Monitor and log user activities to detect and investigate any suspicious or unauthorized access attempts.
Use Lobby for Meetings with External Users
To enhance the security of meetings involving external users, Microsoft Teams provides a lobby feature. Enabling the lobby allows meeting organizers to control who can join a meeting and provides an opportunity to screen participants before granting them access.
To use the lobby feature effectively:
- Configure your meeting settings to automatically place external participants in the lobby.
- Assign a designated meeting organizer who can manage participants and admit them to the meeting.
- Educate meeting organizers on the importance of verifying the identity of external participants before granting access.
- Regularly communicate with meeting organizers about potential security risks and provide guidelines for handling suspicious or unauthorized participants.
How Lepide Ensures Microsoft Teams Security
As we previously mentioned, the majority of security concerns with MS Teams come from rushed deployments resulting in misconfigured permissions. In order to use MS Teams securely, you need to ensure that you have visibility over when users are added or removed from teams, to maintain a principle of least privilege. You also need to make sure that you are aware of when sensitive data is being shared either publically or privately.
The security settings of Office 365 are confusing at best, and disruptive at worst. For enterprises, native security just isn’t going to cut it. The Lepide Data Security Platform enables you to get more visibility over how your users are interacting with Teams, including when sessions are started, when teams are created, when channels are created, and more. You can also receive real-time alerts and implement automated responses for when sensitive data is shared in teams, to help maintain a zero-trust policy.
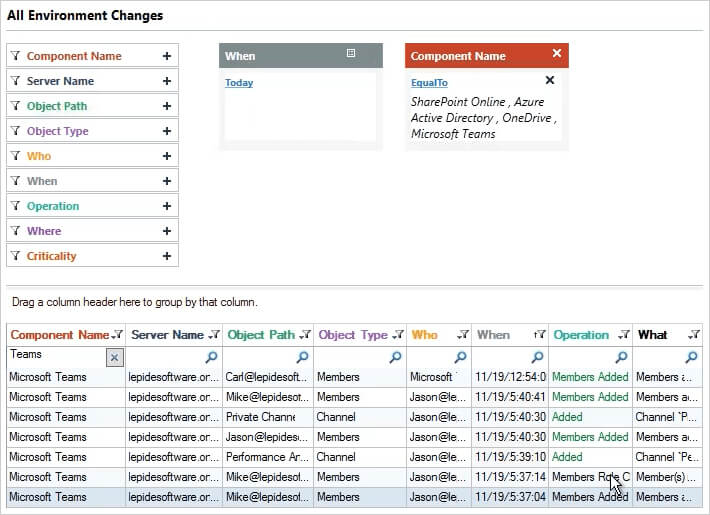
Lepide Data Security Platform – MS Teams Security
If you’d like to see how Lepide helps to improve MS Teams security, schedule a demo with one of our engineers today.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
