Last Updated on January 17, 2025 by Satyendra

What is Passwordless Authentication?
Passwordless Authentication is an authentication method in which the identity of a user is verified, giving them access to a network, application, or system, but without a password, security questions, or PIN code.
Instead, the user provides some other form of verification such as a fingerprint or hardware token code. Passwordless Authentication can be used in conjunction with Multi-Factor Authentication (MFA) and Single Sign-On (SSO) solutions to improve the user experience, strengthen security, and reduce the related expense and complexity for IT management teams. Passwordless authentication is becoming an increasingly popular alternative to the traditional username and password methods.
The Problem with Passwords
Passwords are becoming an outdated verification method as they are often the weakest link in protecting digital resources. In the course of their day-to-day jobs, users are required to memorize and track a large number of frequently changing passwords. This can become an overwhelming task and so many users will try to make their lives easier by doing things such as using the same password for all the applications they need to access, using weak passwords, or writing down passwords. Attackers can take advantage of any careless password management habits to launch cyberattacks and gain access to confidential data. Because of this, as you might expect, compromised account credentials are a leading cause of data breaches.
Authentication methods that require only username and password combinations are fundamentally vulnerable as attackers can find ways to guess passwords and therefore gain access to sensitive information and IT systems. This can be done using a variety of techniques, including the following:
Brute force: They can use programs to generate and attempt to use random username and password combinations or exploit common weak passwords.
Credential stuffing: Stolen credentials from one account can be used to gain access to other accounts. This is the problem with employees reusing the same username/password combination for many different accounts.
Phishing: Fake emails or text messages can be used to trick a victim into giving away their credentials.
Keylogging: This involves installing malware on a computer to capture username and password keystrokes.
Intercepted Interactions: Communication streams (for example over public WiFi,) can be intercepted and credentials stolen.

Passwordless Technology Progression
In the 1980s, a passwordless security solution was first seen in the form of a fob, which contained authentication components to allow access to computer systems. Since then, there’s been a lot of progress made in the advancement of passwordless technology and the way in which it’s been incorporated into various solutions and cybersecurity programs. In the 1990s, we saw that the physical fob could now store much more than just a one-time password and these capabilities included time-based and hash-based protocols. Then, as SSO was being promoted, the physical fob and hardware tokens remained as standard passwordless verification options, and by the 2000’s these evolved into smart card technology.
Once AT&T patented the first MFA tool, companies started competing for passwordless technology. Microsoft helped design the tamper-resistant biometric ID card in 2004. Then, 2005 saw an increase in biometric and token-based authentication innovations. These were because the Federal Financial Institutions Examination Council’s (FFIEC) had put into place new security guidelines requiring new multiple-factor authentication measures, and these included passwordless methods.
Then in 2013, Google became entirely passwordless and MFA procedures became the new standard. That same year, Apple introduced biometric technology like Touch ID, which later evolved into Face ID. In 2020, Apple announced they would incorporate their biometric verification functions for use in the WebAuthn authenticator.
Benefits of Passwordless Authentication
Anyone who’s ever interacted with a password can see the benefits of passwordless authentication. This ranges from IT security leaders to consumers who have no IT experience.
With 92% of businesses believing that going passwordless is the future of system-access security, it is clear that they consider that the benefits outweigh the costs.
The benefits of passwordless authentication include the following:
- Improves user experiences as there is no password required for the user to create and remember
- Registration and login experience is a much simpler process
- Strengthens security by eliminating risky password management techniques and reducing credential theft and impersonation
- Organizations save money by eliminating helpdesk tickets related to password resets
- Prevents account lockout
- Simplifies IT operations by eliminating the need to issue, secure, rotate, reset, and manage passwords.
Enhanced Security
While passwords seem like a beneficial way to secure organizational data and applications, they in fact lead to additional access points which can be exploited by cybercriminals.
For example, attacks such as phishing, credential stuffing, brute force algorithms, and keylogging only work if the threat actor can first obtain the login credentials like a password or other piece of information and then use that to access a data system. By going passwordless, you eliminate that whole process and thereby strengthen your security posture.
User Convenience
Most people have many online accounts that require passwords. Using passwords which are appropriately complex, with random characters that spell nothing, can be too difficult for people to remember. Forgotten passwords lead to the need for password resets or account lockout and both of these are frustrating and time-consuming to administer. Many customers will leave a website rather than endure such a frustrating experience.
Passwordless authentication means that customers and employees can log in easily with an email link, an authenticator app, or a familiar method that they are using frequently, such as the face scan on their phones or touch id on their laptops.
Reduced Password-Related Support
As well as being insecure, passwords are also expensive to manage with many helpdesk calls being related to password resets. A recent consumer study found that the main complaint about passwords is that there are too many for most people to keep track of. This might explain why about a third of consumers say they replace their passwords every six months and a quarter replace them every month due to forgetting or misplacing them.
Those resets aren’t free. Every single password reset will be a cost to an organization and these costs will be increasing.
Compliance and Regulation
Organizations must implement security measures that protect personal data in compliance with data protection regulations, such as the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), among many others.
Passwordless authentication can help to meet compliance standards in a few key ways. First, it will significantly reduce the risk of password-related security incidents, such as phishing attacks and unauthorized access, which can expose sensitive data. In addition to this, as passwordless requires no collection and storage of passwords, it reduces the amount of personal data that organizations need to hold about their customers. The use of passwordless allows organizations to demonstrate to governing bodies that they are taking action to protect data and consumer privacy.
Challenges of Passwordless Authentication
Expenditure: As with any cybersecurity solution, there are disadvantages to the implementation of passwordless authentication which can make it unsuitable for certain businesses. Incorporating this solution is long and complicated and major expenses are required for purchasing the essential hardware and software.
Training: Extensive training will be required for the employees who will use the new authentication methods together with the IT security staff who will need to administer it.
Loss of Access: There can be some limitations to using password authentication from a security perspective. For example, if an employee was using their phone to verify their identity and then lost their phone, they would be unable to gain access.
How Does Passwordless Authentication Work?
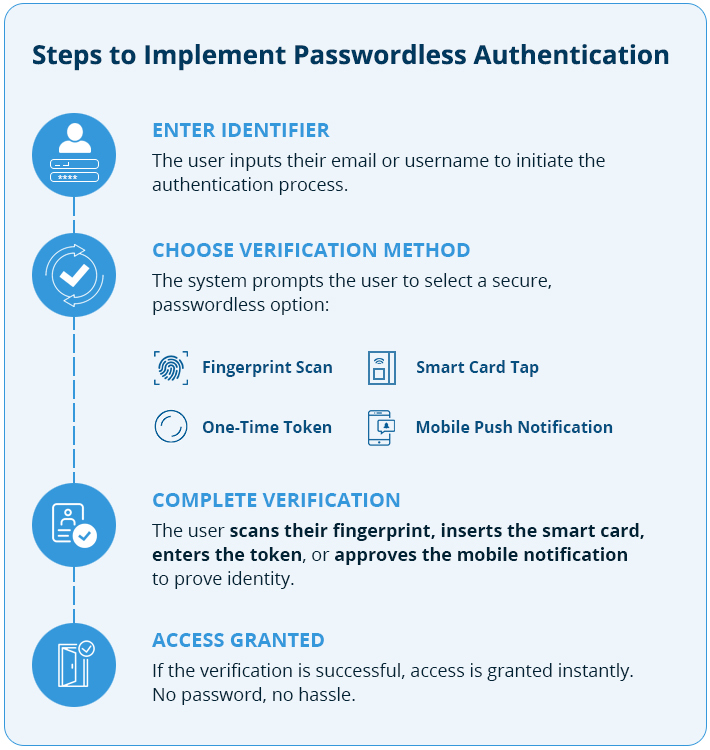
Passwordless authentication replaces passwords with other authentication methods that are safer. It works by using something the user has or something the user is to verify their identity. This contrasts with a traditional password login, which would be something the user knows.
Usually, a passwordless login starts with the user going onto a device, entering a session, or opening an application and entering some type of identifiable information like their name or email address. From there, they need to verify their identity by inserting something they have such as a smart card or clicking a link sent to a mobile device. If the identifiable information matches the information in the authenticating database, then access is given.
An alternative is that the user could use a biometric factor. So, when they try to access a device or account, they could be prompted to provide identifiable information which could be a fingerprint or facial scan.
Passwordless Authentication Methods
Passwordless authentication methods include;
- Native options – Companies such as Google or Microsoft, offer embedded passwordless authentication tools. For example, Google Chrome now lets users to log in to applications via a USB security key or an on-screen QR code that links with a user’s mobile device. Organizations could combine these tools into their overall MFA process.
- Biometrics – Biometric logins, can include fingerprint, voice, facial recognition or retina scanning. With these methods, advanced scanners or sensors capture the biometric and compare it to data saved in the database to permit or deny access. In some cases, the user’s smartphone may serve as a biometric authentication device.
- Hardware Tokens – A hardware token is an electronic device, such as a fob or USB device. A USB device works through a physical connection to the computer, whereas some of the hard tokens, such as fobs, do not. A fob works by generating a new passcode each time a user pushes a button. The user then enters the passcode into an on-screen prompt to gain access.
- Push Notifications – A software token is a digital token sent to a user’s smartphone, computer, or tablet. It usually consists of a 6-8 digit code, which the user then enters, often along with a second authentication method, to gain access.
- Magic Links – A magic link allows a user to log in to an account with a one-time URL sent via email or SMS. Once opened, a background authentication application matches the device to a token in a database.
- Smart Cards – Smart card authentication uses a physical card, a card reader and enabling software to give users access to applications. Smart cards often rely on a data-containing chip and RFID wireless connectivity to grant access privileges.
- Third-party Identity Providers – Anyone who’s signed into an application with Google or Facebook has used a third-party Identify Provider (IdP). The process is as follows: The user enters credentials from a third-party login. The IdP verifies the user and their privileges with their company’s IT and then, the user gains access to the application or resource.
- Persistent Cookies – A persistent cookie is a file stored on a particular device. Using this, it can remember the device user’s sign-on credentials and therefore can assess whether they are logged in and in turn grant access to applications. A persistent cookie can remain on a computer permanently or until a specified expiration date.
Is Passwordless Authentication Safe?
Using passwordless authentication makes it much more difficult and costly for attackers to be successful. For example, with FIDO (Fast Identity Online), the first open identity standard created to support passwordless authentication, user credentials never leave the device and are not stored anywhere on a server, which reduces the chance of phishing, password theft, and replay attacks. As well as this, passwords present a host of usability problems and so passwordless authentication greatly improves the user experience. It’s much easier for users to provide a fingerprint or speak into a microphone than it is to remember and keep track of passwords.
If you’d like to see how the Lepide Data Security Platform can help you spot the signs of privilege abuse and cyber-attacks, such as brute force attacks, schedule a demo with one of our engineers.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
