In today’s ever more complex digital world, security is a major concern for all organizations. One of the most common security challenges faced by system administrators is dealing with account lockouts. When an Active Directory user account is locked, an account lockout event ID is added to the Windows event logs. Event ID 4740 is added for domain controllers and Event ID 4625 is added to client computers. In this article, we’re going to focus on event ID 4740.
There are several reasons why account lockouts can occur. These include:
- Repeated incorrect password attempts
- Drive mapping using old credentials
- Scheduled tasks
- Programs or services using old credentials,
- Slow Active Directory replication
- Brute-force attacks,
As an example, incorrect password attempts which exceed the account lockout threshold configured in your domain, will cause the user account to be locked out and an Event ID 4740 to be recorded in the Security log of the domain controllers.
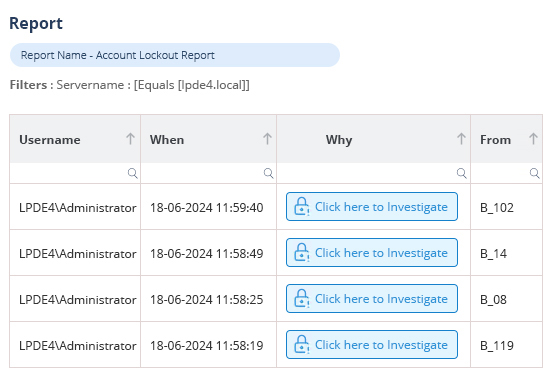
The lockout event ID provides important details about the lockout, such as the account name, time of the event, and the source computer. Understanding how to identify and analyze these event IDs is essential for troubleshooting and addressing account lockout issues effectively.
When you are identifying the causes of account lockouts on domain controllers, it’s essential to understand the various components of Event ID 4740 and how they contribute to the investigation process. These are explained below:
Understanding Event ID 4740 Components
| Component | Description |
|---|---|
| Account Name | This identifies the domain in which the user account resides. |
| Caller Computer Name | This component indicates the name of the computer from which the account lockout request was made. |
| Caller Logon ID | This is a unique identifier for the logon session that initiated the account lockout request. |
| Caller User Name | This component specifies the name of the user associated with the logon session that initiated the account lockout request. |
| Locked Account | It indicates the name of the locked-out user account. |
| Lockout Time | This component displays the date and time when the account lockout occurred. |
Analyzing each of these components of Event ID 4740 helps administrators gain insights into the lockout event’s origin and the corresponding user and computer involved.
Enabling Account Lockout Events
To start tracking account lockout events, it’s necessary to configure the necessary audit policies and enable the appropriate settings. By doing this, administrators can ensure that account lockout events are logged in the Windows event logs.
Open the Group Policy Management Console either on the domain controller or any computer with the Remote Server Administration Tools (RSAT) installed.
Modify the Default Domain Controllers Policy as follows:
Step 1– Select Computer Configuration, Policies, Windows Settings, Security Settings, Advanced Audit Policy Configuration, Audit Policies, Account Management.
Step 2– Enable both Success and Failure auditing for the Audit User Account Management policy.
Step 3– Next, enable the following settings: From Computer Configuration, Policies, Windows Settings, Security Settings, Advanced Audit Policy Configuration, Logon/Logoff select:
- Audit Account Lockout – Success and Failure
- Audit Logoff – Success and Failure
- Audit Logon – Success and Failure
- Audit Other Logon/Logoff Events – Success and Failure
With these audit policies configured, account lockout events will be recorded in the security event logs, giving essential information for investigation.
To analyze account lockout events using Event ID 4740 on domain controllers, follow the instructions given in this article.
How Lepide Account Lockout Examiner Free Tool Helps
Lepide Account Lockout Examiner Free Tool streamlines the process of navigating the complexities of AD account lockouts by providing real-time detection of lockouts and scanning endpoints for stored credentials that may be causing the issues. With its user-friendly interface, administrators can remotely unlock accounts and reset passwords, making account management more efficient.
To see how it works, download the Lepide Account Lockout Examiner Free Tool now.