One of the best ways to know what is happening within your organizational environment is through auditing. Windows Server 2012 Active Directory provides the option to monitor operations performed on the domain and log such information in the Event Viewer. It can log both the successful and failure operations, depending on the audit configuration. As an administrator, you can audit these logs to understand what action was performed by whom and when.
Audit Account Management provides the option to audit operations (Create, modify, delete etc.) on accounts like user, groups, computer etc. Directory Service access is to monitor and audit user accessing active directory object. Auditing Account Management and Directory service access can be configured easily using Group policy object (GPO). Windows Server 2012 GPO provides two options: Traditional Audit policy and Advanced audit policy.
Traditional Audit policy is available at ‘Computer Configuration\Policies\Windows Settings\Security Settings\Local Policies\Audit Policy’ and it only provides the option to audit success and failure operations. Once enabled – refer figure1, it audits every account management and directory option performed on the domain and traditional audit policy does not provide much granular option to audit only specific operation.
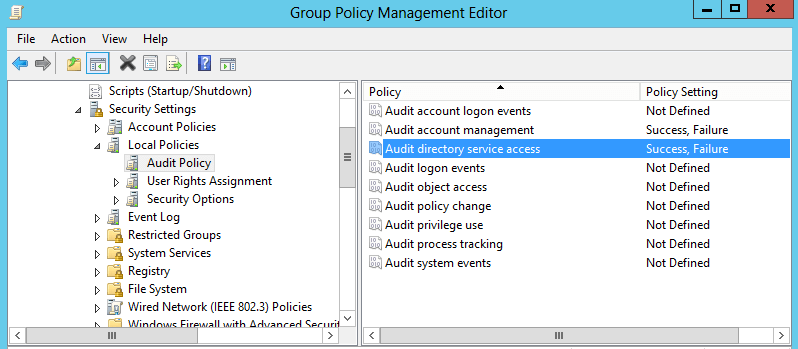
Figure 1. Traditional Audit policy
Advanced audit policy provides more granular option and allows us to enable only specific type of operation to be audited. They are available at Computer ‘Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policies’. Advanced Account management audit policy and advanced Directory service access allows administrators to enable auditing for specific operation to log both success and failure status.
Advanced Account Management audit policy
Audit Application Group Management: It allows auditing events generated by changes made to application groups such as when an application group is created, changed, deleted or member is added or removed from group.
Audit Computer Account Management: It allows auditing events generated by changes made to computer accounts such as when a computer account is created, changed, or deleted.
Audit distribution Group management: It allows auditing events generated by changes made to distribution groups such as when a distribution group is created, changed, deleted or member is added/ removed from a distribution group or distribution group type is changed.
Audit Security Group Management: It allows auditing events generated by changes made to security groups such as when a security group is created, changed, deleted or a member is added/ removed from a distribution group or the distribution group type is changed.
Audit User Account Management: It allows to audit changes to user accounts when
- User account is created, changed, deleted; renamed, disabled, enabled, locked out
- Unlocked or user account’s password is set or
- Changed or security identifier (SID) is added to the SID History of a user account
- Directory Services Restore Mode password is configured or
- Permissions on administrative user accounts are changed or
- Credential Manager Credentials are backed up or restored.
Audit other Account management Events: It allows auditing events like
- The password hash of a user account was accessed. This typically happens during an Active Directory Management Tool password migration.
- The Password Policy Checking API was called. Calls to this function can be part of an attack when a malicious application tests the policy to reduce the number of attempts during a password dictionary attack.
- Changes to the Default Domain Group Policy under the following Group Policy paths:
- Computer Configuration\Windows Settings\Security Settings\Account Policies\Password Policy
- Computer Configuration\Windows Settings\Security Settings\Account Policies\Account Lockout Policy
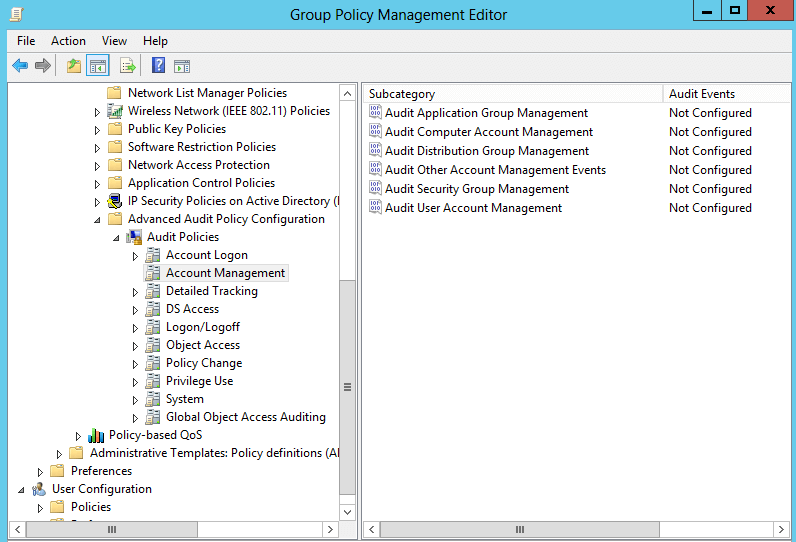
Figure 2. Advanced Audit Policies Account Management
Advanced DS Access
Audit Detailed Directory Service Replication: It allows auditing events generated by detailed Active Directory Domain Services (AD DS) replication between domain controllers.
Audit Directory Service Access: It allows auditing events generated when an Active Directory Domain Services (AD DS) object is accessed which provide the same functionality as the traditional directory service access. Audit is only generated for objects that have system access control lists (SACL) specified, and only if the type of access requested (such as Write, Read, or Modify) and the account making the request match the settings in the SACL.
Active Directory Domain Services Object Changes: It allows auditing events generated by changes to objects in Active Directory Domain Services (AD DS). Events are logged when an object is created, deleted, modified, moved, or undeleted.
Audit Directory Service Replication: It allows auditing replication between two Active Directory Domain Services (AD DS) domain controllers.
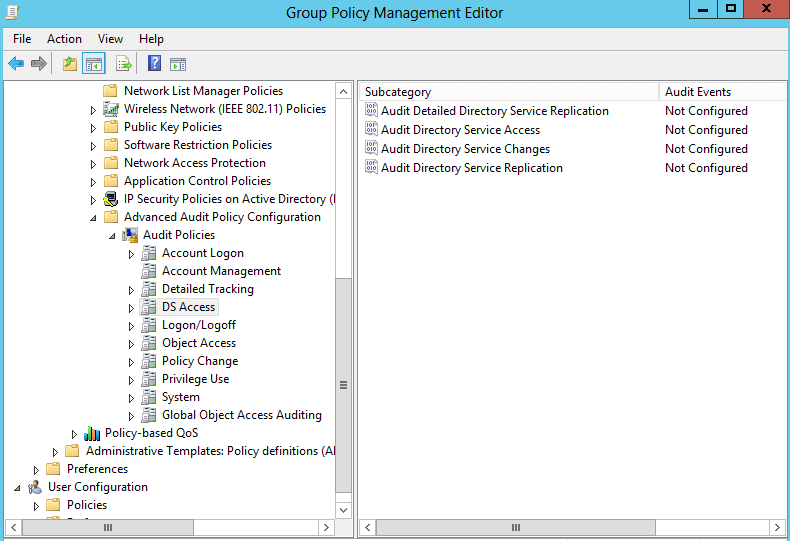
Figure 3. Advanced DS Access policy
Auditing plays a major role in securing the IT environment but enabling all the audits consume resources and can overwrite the audit logs quite soon. Make sure to configure bigger event logs size and enable only those audit logs which are necessary as per the organization’s requirement, since it consumes considerable amount of resources.
You can also try Lepide Active Directory Auditor for auditing all Active Directory changes.



