The Cyber Kill Chain and MITRE ATT&CK Framework are two distinct models used to understand and combat cyberattacks. While both models share a common goal of understanding and mitigating cyber threats, they differ in their approach and scope. The Cyber Kill Chain is a seven-stage model that breaks down cyberattacks into stages, whereas The MITRE ATT&CK Framework takes a more granular approach.
These models enable cybersecurity teams to identify and prioritize threats, develop effective defenses, share cyber threat intelligence, and catalog adversarial tactics and procedures.
What is the Cyber Kill Chain Framework?
Inspired by the military’s kill chain, the Cyber Kill Chain is a step-by-step approach that helps identify and prevent cyber attacks. First introduced by Lockheed Martin in 2011, the Cyber Kill Chain outlines common cyberattacks in 7 stages, including the points at which an information security team can intervene, thus helping them prevent, detect, or intercept an attack. Let’s take a look:
- Reconnaissance: In this stage, the hacker collects information about the target, such as network infrastructure, security posture, employee credentials, etc. They use various tactics to gather this information.
- Weaponization: Once the hacker receives the target’s information, they look for ways to use it to gain access to their system or network. It can be done through social engineering attacks, like phishing, ransomware, etc., or other tactics to install malicious files or software into the system.
- Delivery: Now that they have identified their targets and methods to attack them, hackers penetrate through a phishing email or by exploiting vulnerabilities. By leveraging weaknesses in the system, the attackers can execute their plan without relying on an employee to install the malware, thereby increasing their likelihood of success.
- Exploitation: As a next step, hackers use the identified vulnerabilities to gain deeper access into a network and exploit this access to their advantage. They may conduct network scans or try to seize passwords.
- Installation: Next, hackers seek to establish a persistent presence by installing malicious software on multiple systems. This enables them to maintain access and resume attacks anytime, even if their entry point is discovered and removed. Their objective is to infect as many systems as possible and create backdoor access to ensure the continuity of their attack.
- Command and Control: At this stage, hackers establish a command and control infrastructure, enabling them to oversee and control the compromised systems, send commands to malware, and extract data. This step is vital for attackers to retain control over the compromised environment.
- Actions on Objectives: In the last stage, hackers accomplish their specific goals, such as stealing sensitive information, disrupting business operations, or other malicious activities. At this step, users may suddenly notice unusual notifications on their screens indicating file encryption or unavailability, as attackers openly reveal themselves.
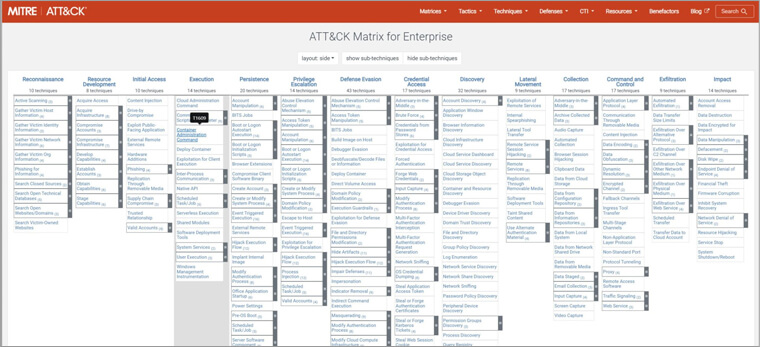
What is the MITRE ATT&CK Framework?
The MITRE ATT&CK Framework is a comprehensive resource that monitors malicious actors’ tactics and techniques throughout the attack process. It is designed to enhance an organization’s security stance by providing insights into hacker’s motivations for their actions and how these actions relate to specific defense strategies.
The framework is populated with data from public threat intelligence, incident reports, and research on new techniques from cybersecurity analysts and attackers. It is an essential framework for cybersecurity professionals to comprehend and counteract malicious behavior. It consists of 14 tactics that describe the reason for the attack. The tactics include:
- Reconnaissance: It includes methods used to collect the target’s information in preparation for targeted attacks in the future.
- Resource development: It includes setting up resources to plan or launch the attack in the future.
- Initial access: It includes methods used by attackers to establish initial entry points into a network through various attack vectors, such as social engineering attacks, credential theft, etc
- Execution: It includes installing malware into the compromised local or remote systems.
- Persistence: It includes maintaining access to the compromised system even in case of system shutdown or modifications.
- Privilege escalation: This includes acquiring high-level access within your company’s network.
- Defense evasion: It includes employing techniques to avoid getting detected after entering the network.
- Credential access: This includes acquiring usernames, passwords, and other login credentials.
- Discovery: It includes gathering information about the target environment to identify accessible or controllable resources that can aid in executing a planned attack.
- Lateral movement: It includes controlling systems within a network, and moving laterally to access additional resources and systems.
- Collection: It includes employing various methods for gathering information from appropriate sources within your organization.
- Command and control: It includes creating secret and untraceable communication channels to gain control over the system.
- Exfiltration: It includes implementing methods that illicitly retrieve data from your network.
- Impact: It includes disrupting the availability or integrity of data and interfering with business operations by interrupting, corrupting, disabling, or destroying data or business processes.
Cyber Kill Chain Vs. MITRE ATT&CK: Key Differences
Lockheed Martin’s Cyber Kill Chain and MITRE ATT&CK both involve understanding how cyber attacks unfold, however, they have some key differences. While MITRE ATT&CK provides detailed information about various tactics, techniques, and procedures used by attackers, Cyber Kill Chain offers a more general overview with seven tactics.
The Cyber Kill Chain focuses on the idea that breaking any of the seven tactics will disrupt an attack, while MITRE ATT&CK focuses on understanding and countering individual tactics and techniques in any context they appear. Additionally, Cyber Kill Chain doesn’t include specific details for mobile or ICS attacks as MITRE ATT&CK does.
Cyber Kill Chain vs. ATT&CK: Which is Better?
The Cyber Kill Chain has several advantages over MITRE ATT&CK, including its ability to encourage proactive defense by identifying attack stages and allowing defenders to allocate security investments based on the most vulnerable stages. However, it also has limitations. For example, it may not account for the increasing sophistication of threats and all potential attack vectors. Additionally, its focus on malware may lead to a lack of attention to other types of attacks, such as insider threats.
The MITRE ATT&CK framework, on the other hand, offers a more comprehensive and granular view of the tactics, techniques, and procedures used by threat actors. It is dynamic and continuously updated to reflect the latest threats and tactics, making it a valuable resource for organizations. However, it can be overwhelming for beginners due to its complexity and the level of expertise required, and it may require continuous monitoring for new updates to ensure preparedness for the latest threats. Additionally, its dynamic nature may make it less effective in detecting and disrupting attacks in real time.
Choosing Between the Models
The choice between the Cyber Kill Chain and MITRE ATT&CK ultimately depends on the organization’s specific needs and goals. For organizations with limited cybersecurity resources or those new to cybersecurity, the Cyber Kill Chain can be a valuable starting point. On the other hand, MITRE ATT&CK provides a deeper level of analysis and guidance for organizations with more sophisticated security needs.
Applying the Models
When reviewing security architecture, the MITRE ATT&CK framework can be applied as a “lens” to assess which techniques and tactics may be mitigated or detected by current controls, and where new solutions should focus. Additionally, the framework can be used to model the attack paths and TTPs of advanced adversaries, enabling red teams to simulate attacks and improve detection and response capabilities. The framework also provides a consistent taxonomy for indicators of compromise (IOCs) and attacker behaviors, enabling effective information sharing within and amongst organizations.
The Evolving Threat Landscape
It is also important to recognize that the threat landscape is constantly evolving, and new attack techniques, tactics, and procedures emerge frequently. As a result, the MITRE ATT&CK matrix is updated regularly, highlighting the need for security teams to continually tune their protections and preparedness as attacks become more advanced.
Conclusion
The Cyber Kill Chain and MITRE ATT&CK are two pivotal frameworks for understanding and analyzing cyber-attacks. While both frameworks have their strengths and weaknesses, combining them in your defensive strategy can provide a clear understanding of the cyber-attack life cycle. MITRE ATT&CK offers a broad view of the tactics, techniques, and procedures used by threat actors, whereas the Cyber Kill Chain provides a more structured approach to understanding the development of a cyber-attack. By integrating both frameworks, you can bolster your defenses against potential threats.