
In the realm of modern enterprise, data is at the core of every organization’s operations. From sensitive customer information to intellectual property and financial records, businesses rely on data to fuel their decision-making processes and maintain a competitive edge. However, with the growing complexity of data storage and regulatory requirements, organizations must adopt appropriate strategies for managing and securing their data.
Two critical concepts that often arise in the context of data management and security are Data Access Governance (DAG) and Data Classification. While these terms are sometimes used interchangeably, they represent distinct approaches to data management. In this comprehensive blog, we will explore the key differences between Data Access Governance and Data Classification, and how they work together to enhance an organization’s data security posture.
What is Data Access Governance (DAG)?
Data Access Governance refers to the processes, policies, and tools that organizations use to ensure that sensitive data is accessed only by authorized individuals. In other words, DAG focuses on who has access to what data and ensures that access is controlled based on roles, responsibilities, and the principle of least privilege.
Data Access Governance (DAG) focuses on ensuring that sensitive data is accessed only by authorized individuals through policies, tools, and procedures. It safeguards data by implementing role-based access control (RBAC) and enforcing the principle of least privilege. DAG aims to protect data from breaches, ensure compliance with regulations, monitor access activities, and conduct regular reviews to maintain proper access rights. By minimizing unauthorized access, improving visibility, and facilitating audits, DAG helps organizations manage risks and meet legal requirements like GDPR and HIPAA while preventing insider threats.
What is Data Classification?
Data Classification refers to the process of categorizing data based on its level of sensitivity and the level of protection it requires. This involves labeling data according to predefined categories, such as public, confidential, sensitive, or restricted, and applying security controls based on the classification level.
The goal of data classification is to understand the value of each data asset and apply appropriate security measures to protect it from unauthorized access or exposure. Data classification is foundational to information security because it allows organizations to prioritize resources and security controls based on the criticality of the data.
For example, an organization may classify employee payroll data as “restricted,” meaning only a few people have access, while marketing materials could be labeled “public,” meaning they can be freely shared without security concerns.
Key Differences Between Data Access Governance and Data Classification
While both Data Access Governance and Data Classification play crucial roles in safeguarding sensitive information, they are fundamentally different in their approach and purpose. Below are the key distinctions between the two:
| Category | Data Access Governance | Data Classification |
|---|---|---|
| Purpose and Focus | It focuses on controlling who has access to data and ensuring that access is limited to authorized individuals. DAG is primarily concerned with managing permissions and ensuring that only the right people can view, edit, or share sensitive data. | It focuses on determining what data is sensitive and how it should be handled. Data classification helps organizations understand the value and sensitivity of their data, which in turn influences how it is protected. |
| Methodology | Focuses on controlling who has access to data and ensuring that access is limited to authorized individuals. DAG is primarily concerned with managing permissions and ensuring that only the right people can view, edit, or share sensitive data. | Focuses on determining what data is sensitive and how it should be handled. Data classification helps organizations understand the value and sensitivity of their data, which in turn influences how it is protected. |
| Data Scope | Primarily focuses on ensuring that people have the right access to the right data. The scope of DAG includes the management of user permissions, roles, and access reviews. | Focuses on the data itself, ensuring that it is appropriately labeled and protected based on its sensitivity. The scope of data classification is broader, as it encompasses all types of data within the organization. |
| Compliance and Regulations | DAG ensures compliance with data privacy regulations that mandate restricted access to sensitive information. For example, GDPR requires organizations to implement appropriate access controls to protect personal data. | Data classification supports compliance by helping organizations identify and protect sensitive information as required by regulations. Many laws require organizations to know where sensitive data resides and to classify it accordingly. |
| Implementation | Implementation typically involves the use of identity and access management (IAM) systems, role-based access control (RBAC), and auditing tools to monitor and enforce access policies. | Implementation involves the use of data discovery tools, labeling systems, and encryption technologies to protect classified data according to its sensitivity level. |
| Ongoing Management | Requires continuous monitoring and auditing of access rights, along with regular reviews to ensure that access permissions are still appropriate. Access needs to be revoked or updated as users change roles or leave the organization. | Involves periodic reclassification of data as its value or sensitivity may change over time. Data classification also requires ongoing enforcement of security measures based on the classification level. |
Challenges in Implementing Data Access Governance and Data Classification
While the benefits of DAG and data classification are clear, organizations often face challenges in implementing these systems effectively. Below are some of the most common hurdles:
1. Data Volume and Complexity
The sheer volume of data that organizations manage today makes both data classification and DAG challenging. As data grows in size and complexity, identifying and categorizing all sensitive information becomes a monumental task. Automation tools can help, but they must be properly configured to account for all types of data.
2. Keeping Access Rights Updated
Ensuring that access rights are consistently updated as employees change roles or leave the company is a persistent challenge. Without regular access reviews and strong IAM processes, outdated permissions can lead to security risks, such as former employees retaining access to sensitive data.
3. Balancing Security and Productivity
Over-restricting access to data can hinder employees’ ability to do their jobs while under-restricting access can expose the organization to security risks. Striking the right balance between security and productivity is key to implementing effective DAG policies.
4. Compliance and Regulatory Changes
Compliance with data privacy laws is an evolving challenge, as regulations like GDPR, CCPA, and HIPAA are continuously updated. Organizations must stay informed about changes in regulatory requirements and adapt their DAG and data classification strategies accordingly.
5. Organizational Buy-In
For DAG and data classification to be successful, they require buy-in from all levels of the organization, not just IT. Business leaders must understand the importance of data security and provide the necessary resources for implementing these systems.
How Data Access Governance and Data Classification Work Together
While Data Access Governance and Data Classification are distinct concepts, they complement each other and are often used together in comprehensive data security strategies.
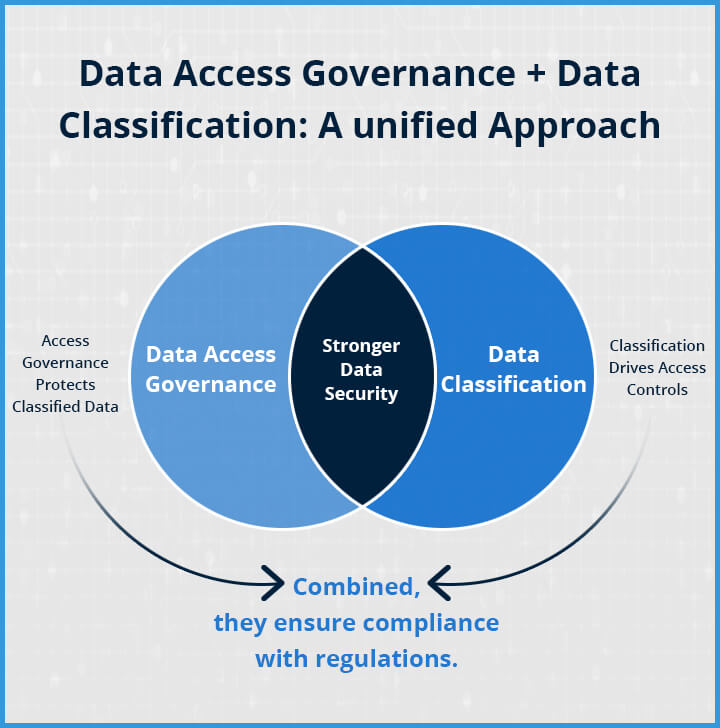
Classification Drives Access Controls
Data classification informs access control decisions. By identifying which data is sensitive, organizations can apply stricter access controls to that data. For example, data classified as “confidential” may be accessible only to high-level executives, while “internal” data may be available to a wider group of employees.
Access Governance Protects Classified Data
Once data is classified, DAG ensures that only authorized individuals can access it. For example, if a file is labeled as “restricted,” DAG policies ensure that only employees with the appropriate clearance can view or edit that file. Without DAG, classified data could still be exposed to unauthorized individuals, leading to security breaches.
Joint Role in Compliance
Many regulatory frameworks require organizations to not only identify sensitive data but also control who can access it. By implementing both data classification and DAG, organizations can meet these regulatory requirements and reduce the risk of penalties.
For instance, under GDPR, organizations are required to identify and protect personal data (data classification) and ensure that only authorized personnel can access that data (DAG). The combination of both ensures that sensitive data is properly managed, accessed, and protected.
Best Practices for Implementing Data Access Governance and Data Classification
To successfully implement both Data Access Governance and Data Classification, organizations should consider the following best practices:
1. Start with Data Discovery
Before implementing DAG or data classification, it’s essential to know where all sensitive data resides. Data discovery tools can help identify data across on-premises and cloud environments, ensuring that no critical information is overlooked. This step provides a foundation for both accurate data classification and access control policies.
2. Define Clear Classification Categories
Organizations should define clear and understandable data classification categories, such as “Public,” “Internal,” “Confidential,” and “Restricted.” These categories must be aligned with the business’s specific needs and risks. Simplicity is key here—overly complex categories can lead to confusion and improper classification.
3. Automate Where Possible
Both data classification and DAG benefit from automation. Automated tools can streamline the classification process by scanning data for predefined criteria (such as keywords or file types) and applying labels accordingly. Similarly, identity and access management (IAM) tools can help automate access control based on roles and policies, reducing the burden on IT teams and ensuring more consistent enforcement.
4. Conduct Regular Access Reviews
Access needs change over time as employees change roles, leave the organization, or new regulations come into play. Conducting regular access reviews helps ensure that access rights remain appropriate and aligned with current needs. This is a critical aspect of maintaining a strong DAG framework.
5. Train Employees on Data Handling
Data classification and access controls are only as strong as the people who follow them. Providing ongoing training to employees on how to properly handle, classify, and access data ensures that the organization’s policies are followed. Training should cover topics like recognizing sensitive information, understanding classification labels, and securely sharing data.
6. Implement Strong Encryption
While DAG and data classification focus on access controls and labeling, encryption adds a layer of protection. Ensure that sensitive data, especially data classified as confidential or restricted, is encrypted both at rest and in transit to protect against unauthorized access, even if data is accidentally exposed or stolen.
7. Monitor and Audit Regularly
Continuous monitoring and auditing are vital to ensure compliance with DAG policies and classification accuracy. Organizations should have logging and alerting mechanisms in place to track who accesses data and when, and flag any suspicious activity. This not only helps in preventing unauthorized access but also aids in post-incident investigations if a breach occurs.
How Lepide Can Help
Lepide Data Access Governance and Data Classification Solution work together to simplify and enhance your organization’s approach to sensitive data management. These comprehensive solutions help you govern data access efficiently and classify sensitive information, ensuring compliance with regulatory requirements and improved data security.
1. Data Discovery and Classification
Lepide Data Security Platform provides automated data discovery and classification, allowing you to identify and classify sensitive information across your network. Whether it’s Personally Identifiable Information (PII), Payment Card Information (PCI), or intellectual property, Lepide helps you understand where your sensitive data resides and how it is being used.
2. Granular Data Access Controls
Lepide enables granular control over who can access sensitive data, ensuring that only authorized users can view or modify classified information. The solution integrates seamlessly with Active Directory and other Identity and Access Management (IAM) systems to provide powerful access management.
3. Real-Time Monitoring and Alerts
Lepide provides real-time monitoring and alerts to help you detect unauthorized access or any suspicious behavior related to sensitive data. You can set custom alerts for specific actions, such as accessing sensitive files, changes to permissions, or unusual login activity.
4. Data Risk Assessment
Lepide helps organizations assess their data risk by identifying overexposed data, inactive user accounts, and stale data that could pose a security risk. By highlighting these vulnerabilities, you can take steps to mitigate risk proactively.
5. Compliance Reporting
Lepide makes it easy to generate reports for compliance with various regulatory frameworks, including GDPR, HIPAA, SOX, and PCI-DSS. These reports provide detailed documentation of how sensitive data is classified, accessed, and protected, which can be shared with auditors or regulatory bodies.
Conclusion
Data Access Governance and Data Classification are two essential pillars of an organization’s data security strategy. While they serve different functions, DAG focuses on controlling who has access to data, and data classification focuses on categorizing data based on its sensitivity, they work together to protect sensitive information from unauthorized access, ensure compliance with regulations, and reduce the risk of data breaches.
Investing in strong DAG and data classification systems isn’t just a matter of regulatory compliance; it’s a smart business decision that enhances operational efficiency, builds customer trust, and protects the organization’s reputation. As data continues to grow in volume and importance, businesses that take a proactive approach to managing and securing their data will be better positioned to thrive.
If you want to know more about how Lepide can help, schedule a demo with one of our engineers today.

