
Dynamic Access Control (DAC) is a new feature introduced in Windows Server 2012 and Windows 8. It allows to apply access control and restricted permission based conditional rules for accessing files and folders dynamically. For Example, if a new user joins a department or if an employee moves from one department to another department or his role changes, then the file and folder permissions changes are dynamically added and removed without the administrator’s intervention. However, it does not support any operating system prior to Windows Server 2012 and Windows 8. Some of the entities involved with Dynamic control to provide dynamic permissions are:
Claims types: It can be a user, device (computers etc.) or resources that have been published by a domain controller. To be more specific, it can be a user title, department, location, other property or a combination of these properties can be considered as a valid claim to provide access to the resources.
Resource properties: Creating classifications or tags that could be used to apply on the shared file resources. Classifications may be like tagging the folder with the department name. This value is compared with the user claim AD attribute for effective permission.
Resource property list (RPL): Each of the resource properties are added to the resource property list and it is downloaded to the file server. Any number of RPLs can be deployed on the file server and global resource property list can be deployed on all the file servers in the organization.
Central Access Rule: These rules are set of conditions involving claims which provide access or deny permissions.
Central Access Policy: It can be one or more central access rules applied to provide the necessary permissions. These are in addition to the local NTFS permission provided on the files and folders.
Now, let’s understand how to provide necessary permissions to files and folders through DAC model.
Before we configure Dynamic Access Control in the environment, we need to configure the domain to support it. Below are the steps to perform the same:
-
- Connect to the blue.com Domain control -> access Group policy management console -> Domain controllers -> Right click Default Domain Controllers Policy and select Edit.
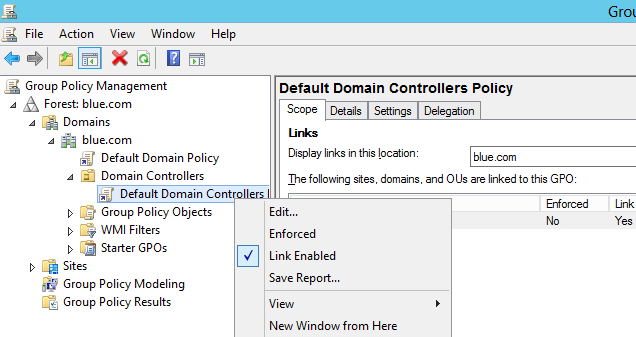
-
- In the group policy management editor, double-click computer configuration -> policies -> administrative template -> system -> KDC
- Right-click “KDC support for claims, compound authentication, and Kerberos armoring” and enable it.
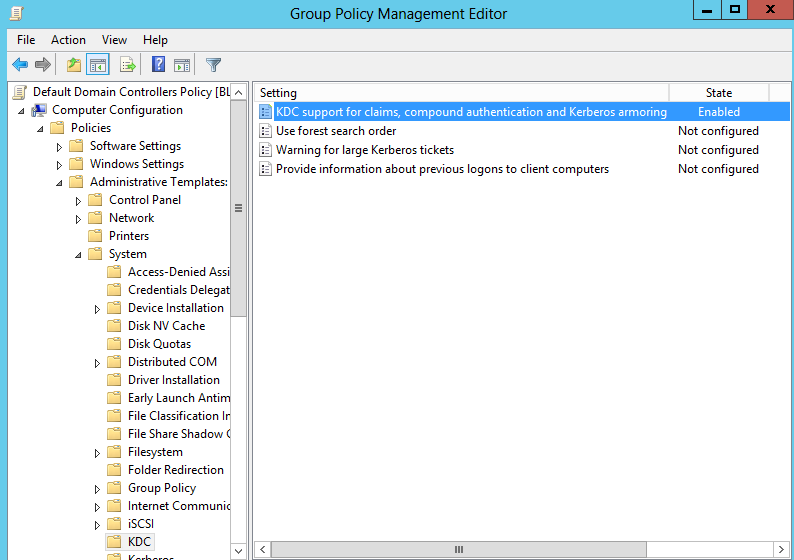
Configuring Claim Type:
In this step, we will configure claim by defining the Active Directory attribute which is used to provide access to the resource.
-
- Login to Windows Server 2012 and click on Start -> Run and type “DSAC” to start ‘Active Directory Administrative Center’.
- On the left pane, click on ‘Dynamic Access Control’ -> select Claim Type -> Right-click select ‘New’ and select Claim Type.
- Search for ‘C’ to create the claim type of country and scroll down to add the suggested value as ‘India’ and Display name as ‘India’
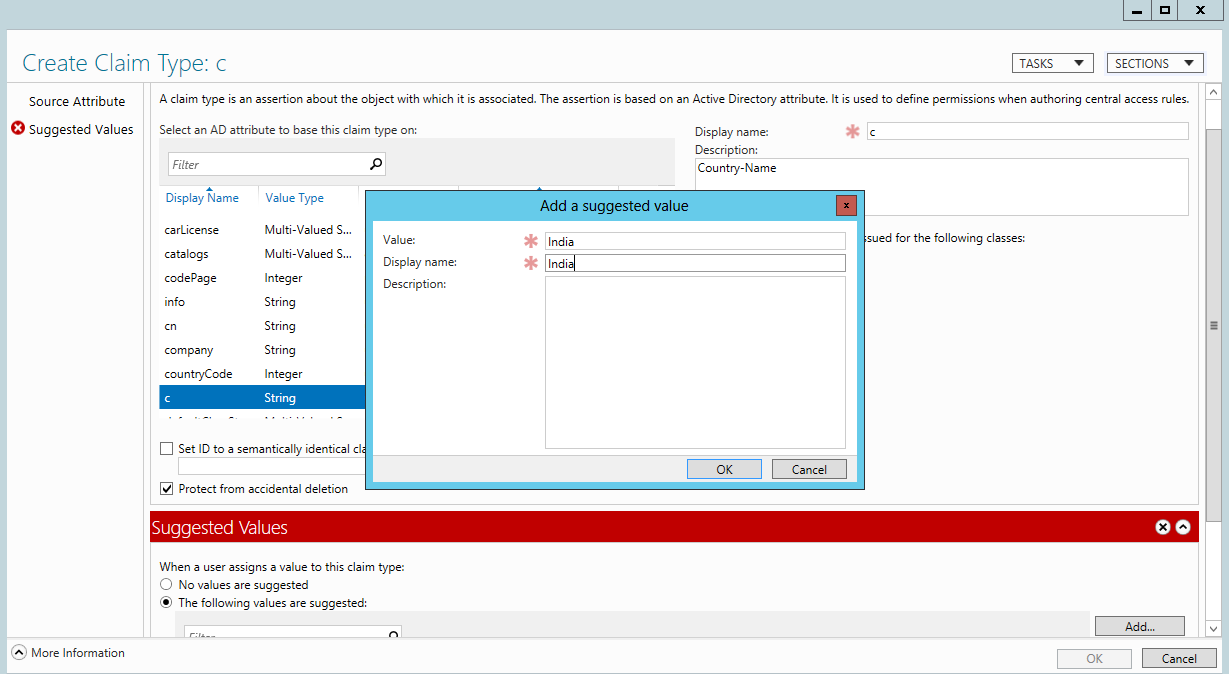
-
- Repeat the same step by searching ‘Department’ in the claim type and add ‘IT’ and click ‘OK’
Resource Properties
Dynamic Access Control allows to create resources properties, which can be downloaded to the file server and tag them for classification purpose. Below are the steps to perform the same:
-
- Connect to Active Directory Administrator Central -> select ‘Dynamic Access Control’
- Double-click Resource properties -> right click ‘Department and select ‘Enable’
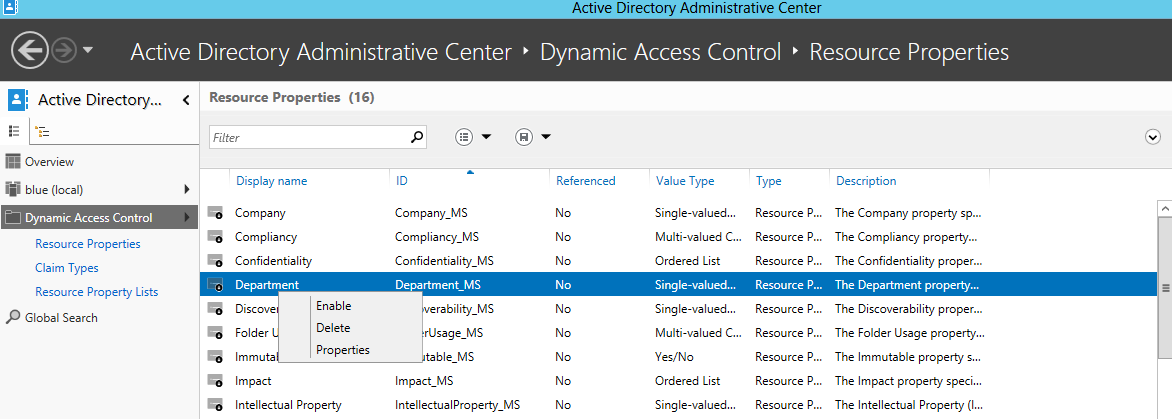
-
- From the bottom right section, select New -> Resource Property -> type display name as ‘Country’ -> click on ‘Add’ to add the suggested Values as “India” for display name.
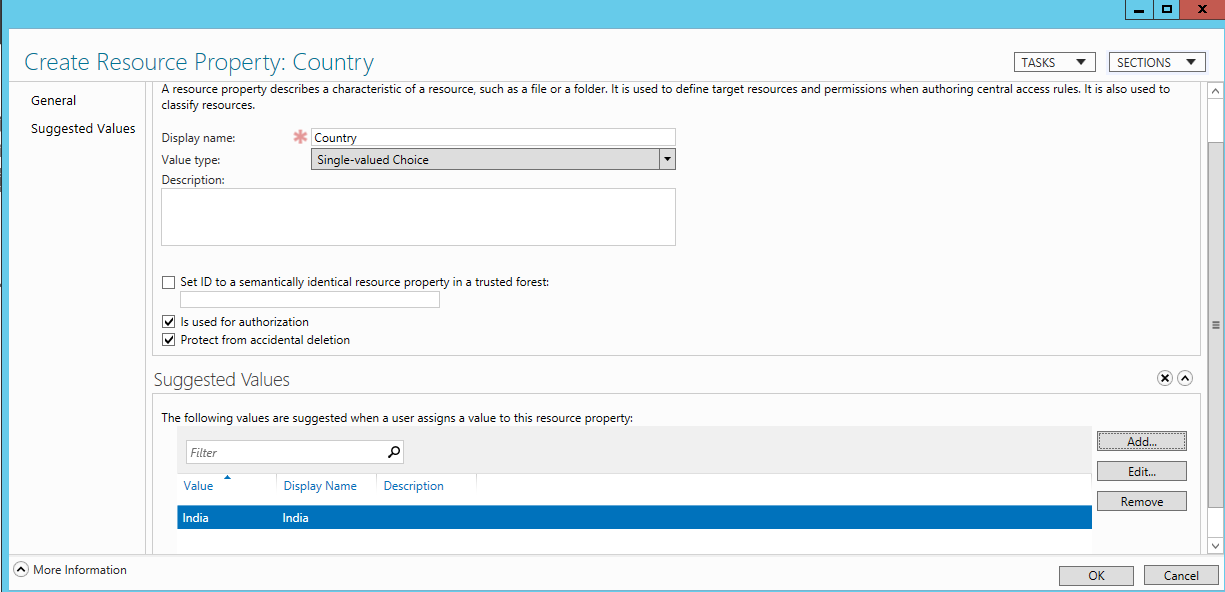
- Right-click on ‘Department’ from resource property and select ‘Enable’.
Resource Property Lists
The above created resource properties are added to the resource property list and this configuration list is downloaded to the fileserver.
-
- Connect to Windows Server 2012 and access Active Directory Administrative Center.
- Double-click on Dynamic Access Control -> select Resource Property list from the left pane.
- Double-click on Global Resource Property list from the center pane.
- Click on ‘Add’ and select country and department into the ‘Global Resource property list’ and click ‘OK’.
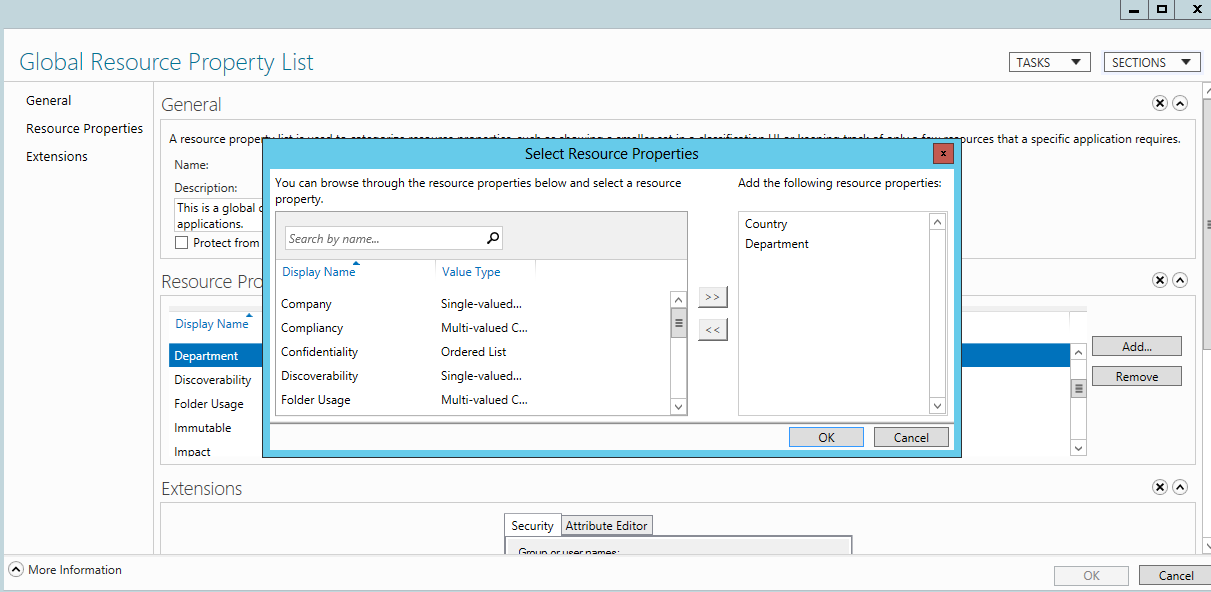
- Finally, close the Global Resource Property list window.
Thus, by the end of this part, we have almost configured the DAC for the file server. We have configured claim types, resource property and resource property list. In the next part, we will configure central access rule, central access policy, and manage the share folder to make sure that only necessary permissions are applied to the right user.

