
Password and account lockout policies in Active Directory needn’t be all or nothing. In this article, I’ll explain how to set password and account lockout policies for specific groups of users and some best practices you should follow in the process.
What are Active Directory Account Policies
Active Directory (AD) domains are configured by default with password and account lockout policies that apply to all user accounts in the domain. Each domain has a Group Policy Object (GPO) called Default Domain Policy where you can set passwords, account lockout, and Kerberos policies under Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies. Account policies are the only settings that you should modify in the Default Domain Policy GPO.
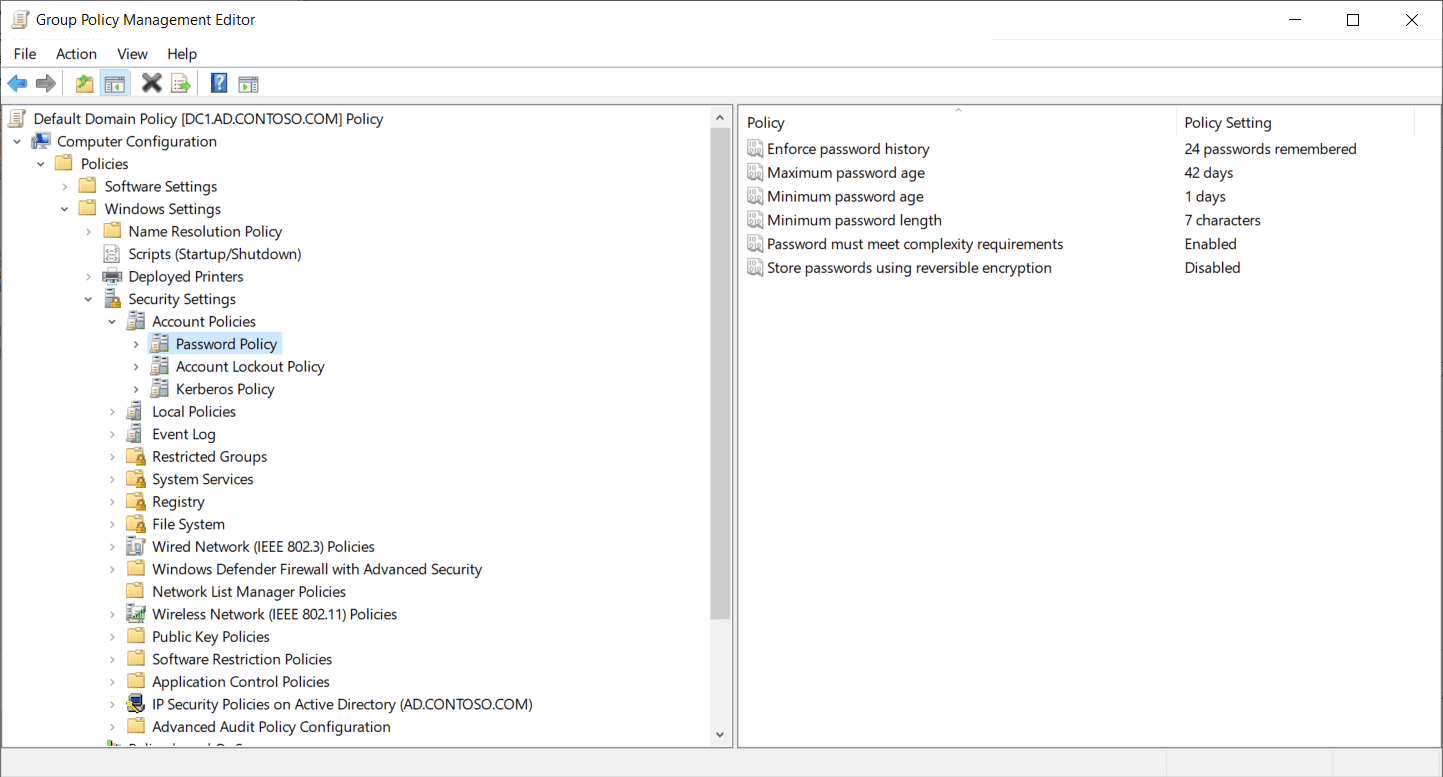 Figure1
Figure1
Password policies include the ability to enforce password history, set a minimum and maximum password age, password length, and more. Account lockout policies define the account lockout duration and the account lockout threshold, i.e. how many failed login attempts are allowed before accounts are locked out.
What is Fine-Grained Password Policy
AD supports one set of password and account lockout policies for a domain. Before Windows Server 2008, if you wanted to apply different password and account lockout policies to users, you had to set up a separate domain for them. For example, it’s common that organizations to prefer to apply stricter password policies to accounts that have privileged access to AD because they are more likely to be targeted due to the high level of access they have. But strict password and account lockout policies that might be applied to privileged domain accounts are impractical for standard employees because they create too much inconvenience.
Beginning in Windows Server 2008, you can override the default password and account lockout policies in a domain using Fine-Grained Password Policies (FGPP). To use Fine-Grained Password Policies, your domain must be at the Windows Server 2008 domain-functional level or higher. Don’t forget that raising the domain functional level is a one-way process.
How to Configure Fine-Grained Password Policy
Unlike the default password and account lockout domain policies, Fine-Grained Password Policies are set in password settings objects (PSO) in AD and not using Group Policy. There are two main ways you can configure PSOs:
- Using the Active Directory Administrative Center (ADAC)
- Using PowerShell
You must be a domain admin or have permissions delegated to you before you can create or change PSOs.
1. Using the Active Directory Administrative Center
-
- Install Remote Server Administrator Tools (RSAT). This will be needed if you use the ADAC console or PowerShell.
- Open the Active Directory Administrative Center
- Create a Policy
Follow these steps to create a new policy.
-
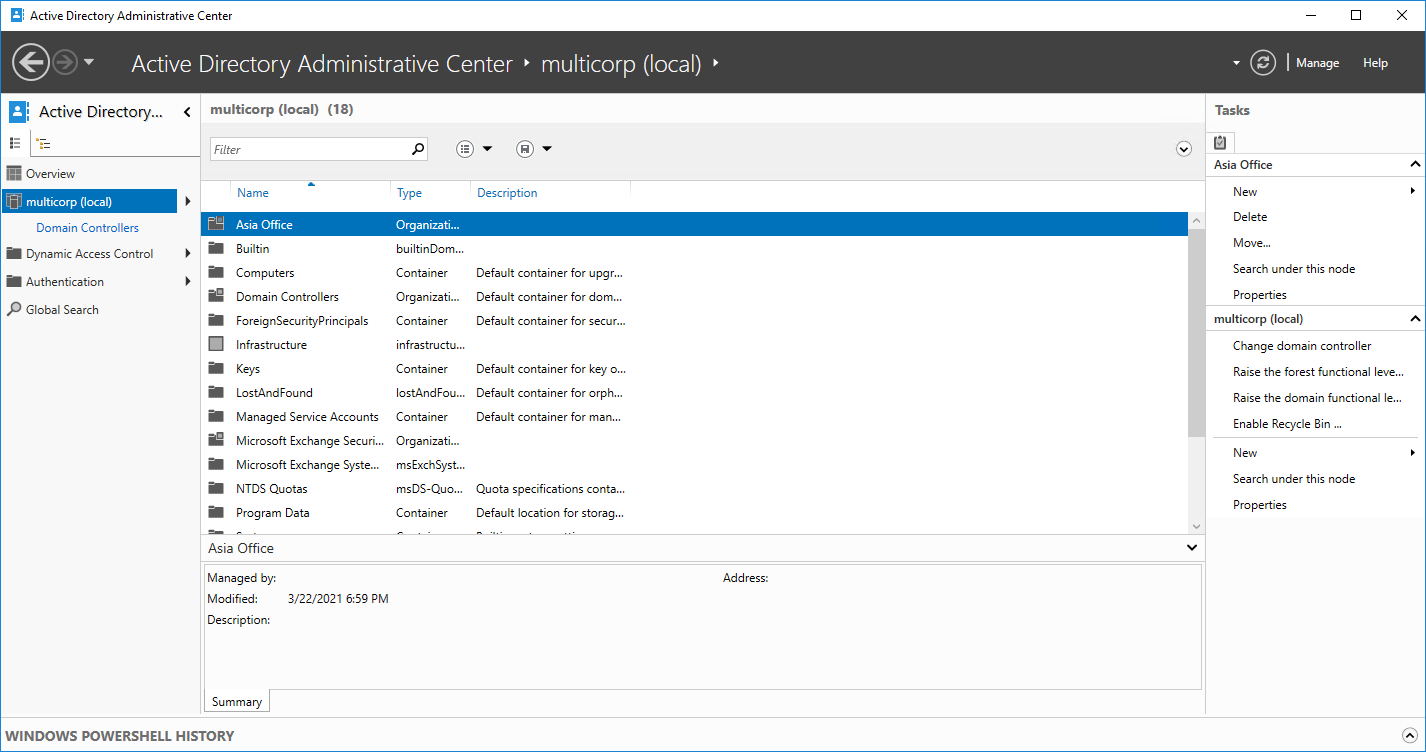
- In ADAC click on your domain
-
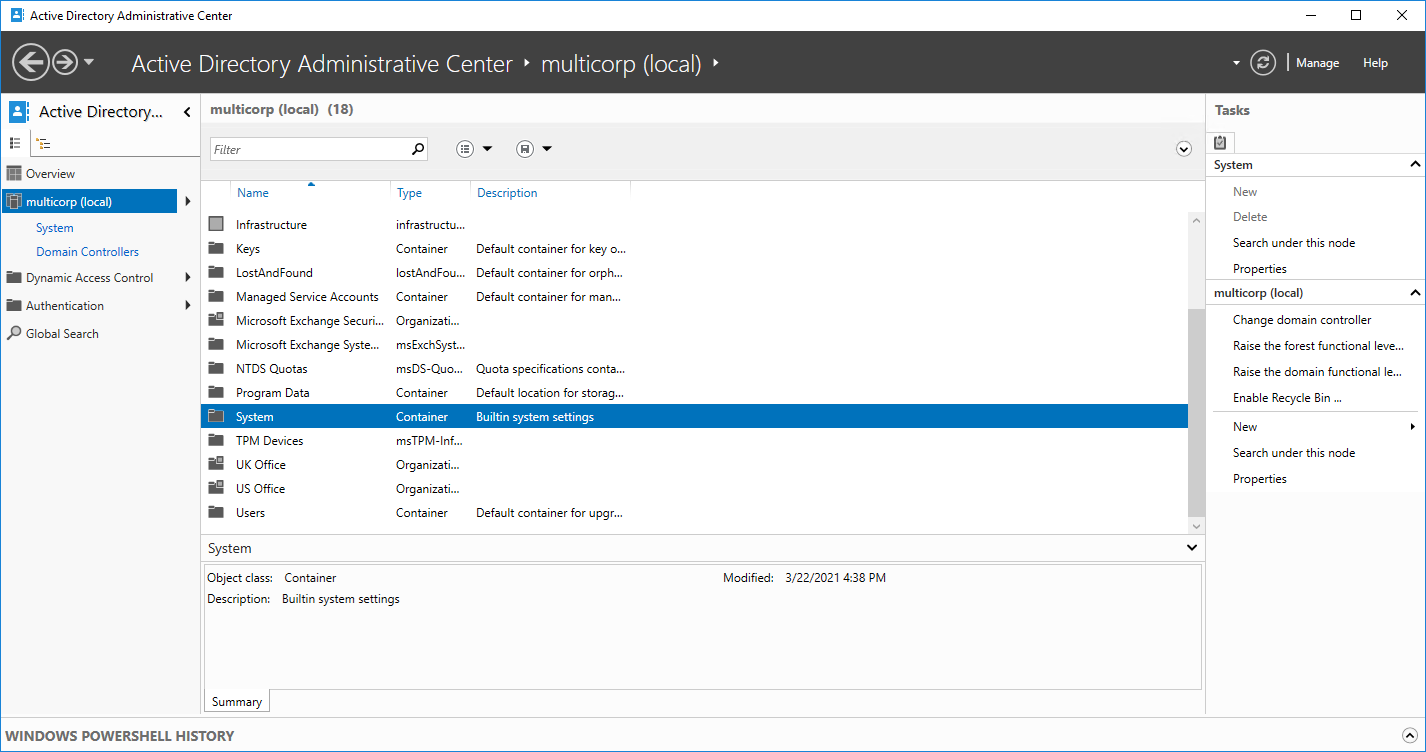
- Click on the System folder
-
- Double click the System Folder
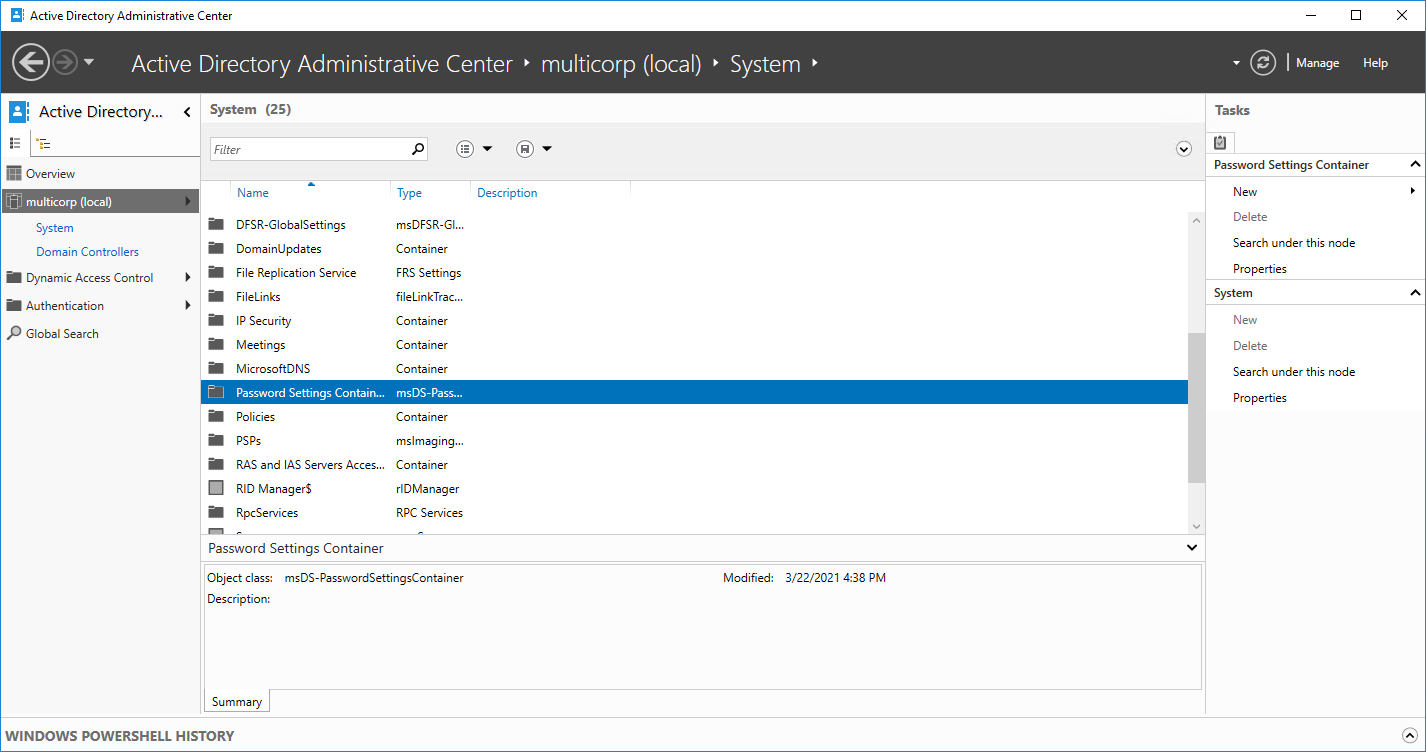
-
- Click on the password settings container then from the right-hand side of the screen, choose New, Password Settings
- You should now be at the Create Password Settings screen
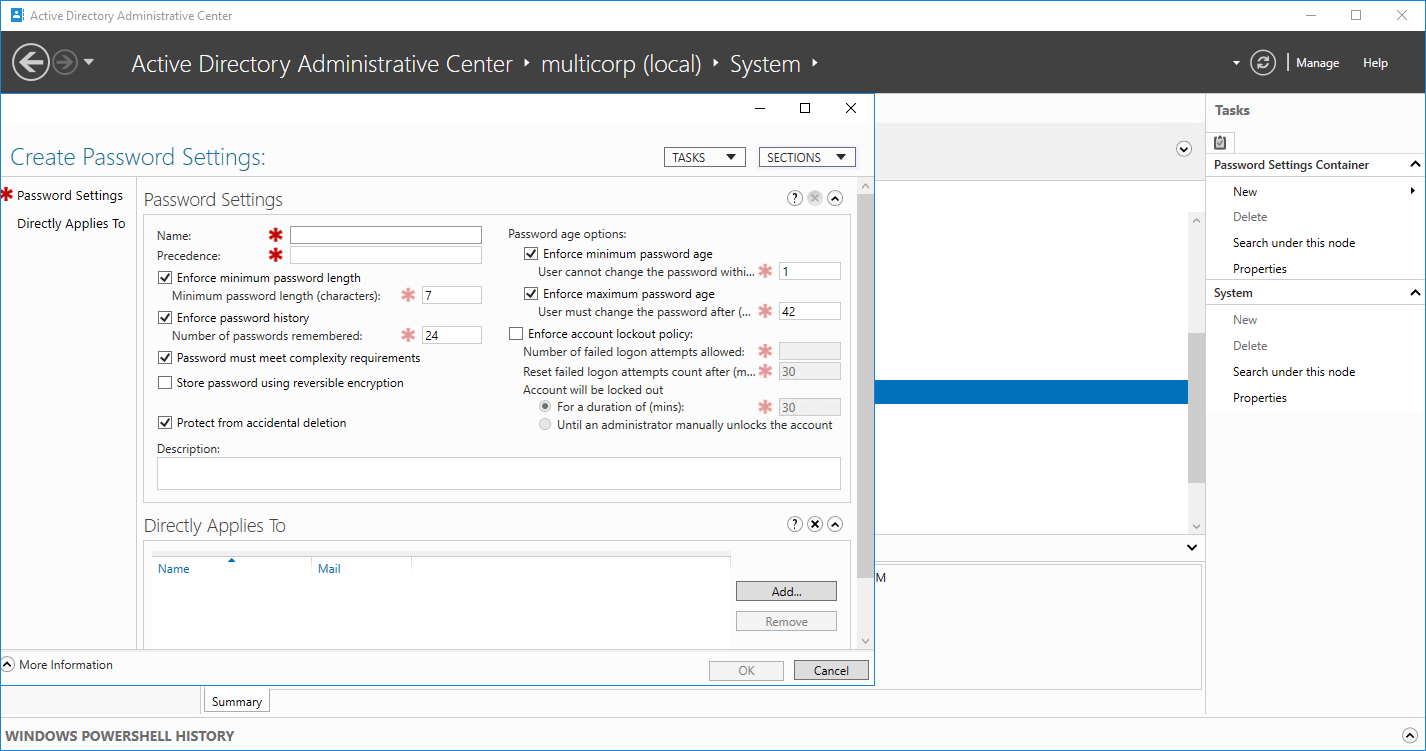
-
- Here you can configure the policy settings and apply it to a user or group. The same password policy settings are available as in the default domain policy.
- In this example, we could set a stronger password for the administrators.
- Here the password policy name is ‘Admin Password Policy’ and the precedence set as 1.
- The minimum password length has been set to 15 and the account lockout policy options have been set.
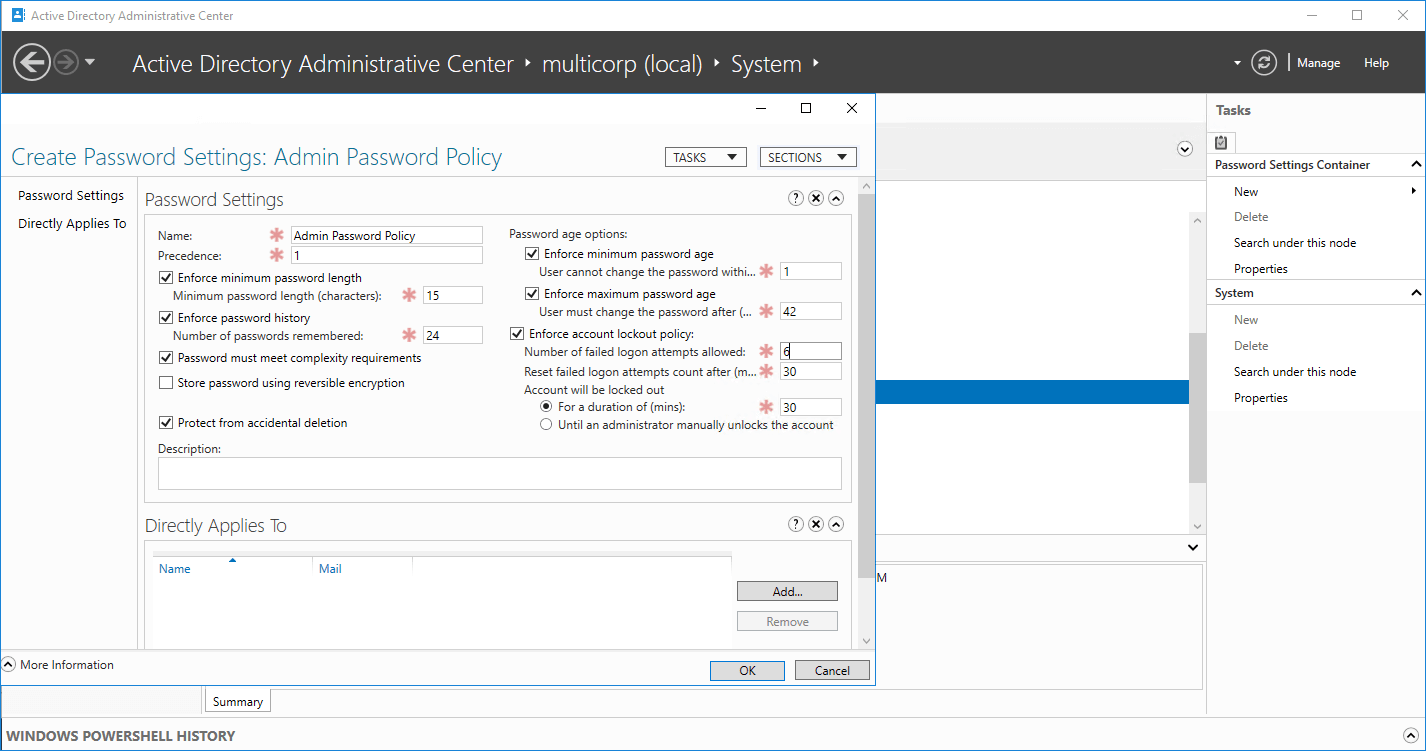
-
- Click on Add to apply it to a user or group. The Select Users or Groups dialog box is displayed
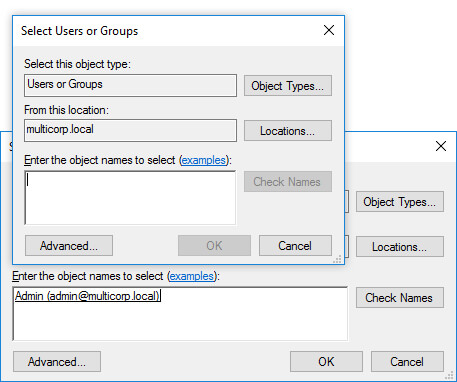
-
- In this example, it has been applied to the Admin Group
- Click OK. The new policy is shown at the bottom of the dialog box.
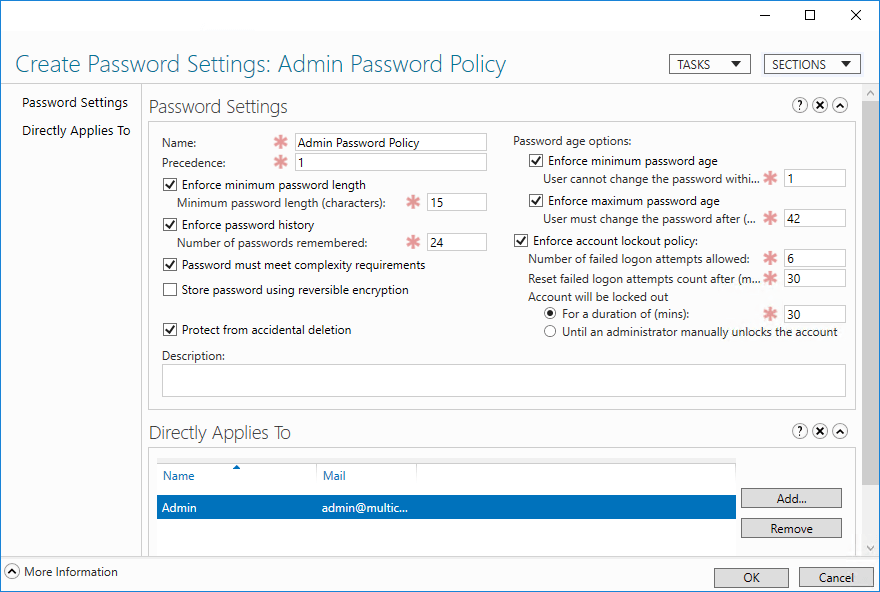
- Click OK
2. Using PowerShell
Use the New-ADFineGrainedPasswordPolicy PowerShell cmdlet to create a new PSO.
New-ADFineGrainedPasswordPolicy -Name administrators1 -DisplayName lepide_admins -Precedence 100 -ComplexityEnabled $true -ReversibleEncryptionEnabled $false -PasswordHistoryCount 10 -MinPasswordLength 8 -MinPasswordAge 3.00:00:00 -MaxPasswordAge 30.00:00:00 -LockoutThreshold 3 -LockoutObservationWindow 0.00:25:00 -LockoutDuration 0.00:30:00
And then apply the new PSO using Add-ADFineGrainedPasswordPolicySubject:
Add-ADFineGrainedPasswordPolicySubject -Identity lepide_admins -Subjects ‘Secure Admins’
Limitations of Fine-Grained Password Policy
The steps described above explain how to create a FGPP in Active Directory, but it’s important to also understand the limitations which include:
- You cannot create custom dictionary lists which then restrict options to block certain words and phrases applicable to your organization.
- FGPP lacks the ability to find and remove compromised passwords already in use, or to block passwords being used in current attacks taking place in real time.
- FGPPs are not applicable to Organizational Units.
- Managing multiple FGPPs can be a challenging task due to the complications involved in keeping track of the assigned policies.
- The limited password and account lockout settings mean that FGPPs cannot meet password compliance regulations such as the NIST password standards.
- FGPPs cannot prevent sophisticated, modern password attacks like dictionary and brute-force attacks.
Fine-Grained Password Policy Implementation Best Practices
When implementing Fine-Grained Password Policies in your organization, there are several things to think about before creating and applying Fine-Grained Password Policies.
- Each PSO must have a precedence index number. PSOs with a higher precedence index, like 1, take priority over those with a lower precedence index, like 10.
- PSOs can be applied to users and groups. When possible, apply PSOs to groups.
- Understand PSO precedence. While PSOs can be applied to multiple users and groups, only one PSO ever applies to a user account. The PSO with the highest precedence index, i.e. closest to 1, will apply. The msDS-ResultantPSO attribute in AD exposes the resultant PSO for a user object if you want to check it. PSOs linked to user accounts always take precedence over those linked to groups.
- Make sure that all PSOs have a unique precedence index number. If two PSOs have the same precedence index number, the PSO with the lowest GUID is applied.
- If you want to apply a PSO to all the users in an Organizational Unit (OU), you will need to create a group that contains all the members of the OU and applies the PSO to the group. If the users in the OU change, you must update the group membership.
- Use password and account lockout policy settings in the Default Domain Policy GPO for most users and create PSOs for smaller specific groups of users.
- Give PSOs meaningful names.
Lack of Visibility Over Password Resets & Lockouts
If you’re struggling to get visibility over password resets and the cause of account lockouts, it might be indicative of a wider problem with Active Directory visibility. You may need to consider deploying an Active Directory auditing solution like Lepide Active Directory Auditor to ensure you are continuously and proactively tracking changes to your AD. This will help you get to grips with whether your Active Directory is secure and compliant.



