Last Updated on December 5, 2024 by Deepanshu Sharma

Well, given that the threats in the digital realm are continuing to change, sometimes, the best way to defeat them is to trick them. Think about the fact that you can set a trigger that instantly goes off when a bad actor comes into contact with it, an unseen wire that just informs you that there are issues. That is the concept behind honey tokens-The cheapest way to access large amounts of honey. However, despite the rather romantic sounding name, honey tokens are one of the powerful strategies in cybersecurity as it allows detecting the problematic activity without an actual violation of security. In the following article, we are going to explain what honey tokens are, how they can be used and the steps to implement them in the organization’s cybersecurity strategy.
What Are Honey Tokens?
In its simplest form, a honey token is a kind of decoy. It’s a piece of fake information or trickiness which makes sense only to hook someone who shouldn’t be seeing it. For instance, a honey token might appear as a password file or a sensitive document or an API key; however, it is not real. It notifies an administrator when anyone tries to open it. It means that security teams can sit there and say at least somebody is doing something they should not be doing and it just leads the way to an insider threat or a bad guy from outside.
In contrast to honey pots, which are entire system or server designed specially to attract the attacker, honey tokens are often small and present in numerous points of an organization’s IT infrastructure. They are easy to implement and do very well to warn organizations of any malicious activities, without much intermeddling with operations.
How Do Honey Tokens Work?
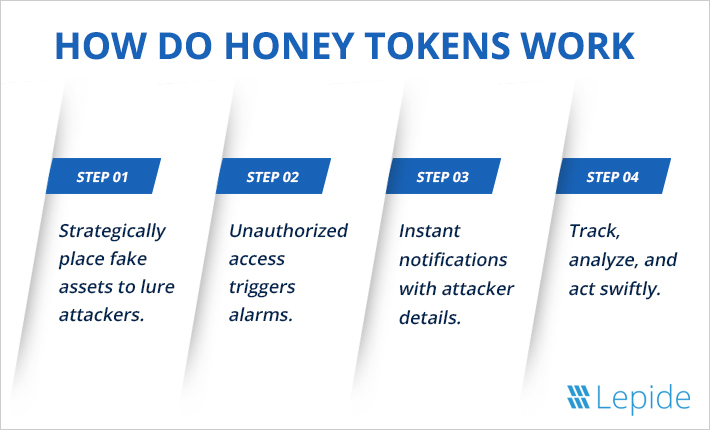
The beauty of honey tokens lies in their simplicity. Here’s how they work:
Deployment of Decoys: For a security team, honey tokens are placed in the areas that the team expects people with malicious intentions to be interested in. These tokens may resemble such things as sensitive documents, privileged passwords, or secret API keys and are deliberately located where insiders or attackers may navigate.
Waiting for Access: Since the honey token is a fake one, genuine users will have no use for the token. Whenever there is an attempt to unlock, spend or transfer a honey token, the systems automatically signal that something is wrong.
Triggering Alerts: As soon as a holder accesses a honey token, it triggers an alert to the security team on duty. If the token has been configured in a certain manner, it may even store information as to the identity of the intruder, the IP address used and time of violation, and any other information the intruder may have entered.
Response and Investigation: When the security team is informed, the team can probe into the situation, follow the actions of the menace, and even determines the possible reasons and goals of the attacker.
These decoys are hugely important for the organization, as they provide an early warning – a kind of silent alarm – that lets you know when something is wrong as soon as something begins to go wrong. Pre-vendorised honey tokens act as strong security instrument in foreseeing breach and the security teams may get the edge over the attackers before they initiate their malicious activities.
Benefits of Implementing Honey Tokens
Implementing honey tokens in your security strategy brings several advantages that make them worth considering. Let’s look at the main benefits:
Early Threat Detection: Basically, honey tokens can be compared to the emitting of a silent alarm. These give you a warning sign to an intruder almost instantly, sometimes perhaps before they gain a significant foothold, in terms of encountering really valuable information.
Easy and Cost-Effective: Compared to other security measures, honey tokens are cheap and easy to setup and can be implemented effectively in a system. They do not demand another structure for their implementation or excessive care.
Minimal Impact on Regular Operations: The fact that honey tokens are fake means they do not alter functional work or expose confidential data. This makes them quite invisible to the actual good users of the site/services and employees don’t have to ‘adjust’ their work processes anymore.
Effective Insider Threat Detection: One of the significant benefits of honey tokens is that the honey tokens can detect insiders. Like the hot token, if an employee or contractor accesses honey token, then is a suspicious sign that they have ill intentions.
Useful for Compliance and Security Audits: The honey tokens can also foster compliance and audit work. They give you that extra layer of protection in your security systems which can be helpful when trying to convince a regulator or an auditor that you are ready and prepared to identify threats.
Essentially, honey tokens are guarantees that you are protected and informed of potential issues before they deep-seed. They are useful in areas where other monitoring tools maybe ineffective, and are thus used as last line of defense in protecting information.
What is the Difference Between Honey Tokens and Honey Pots?
Honey tokens and honey pots share similar goals but serve different functions in cybersecurity.
Honey Tokens: These are small, digital decoys embedded within data or applications. They’re lightweight, often in the form of fake credentials, files, or database records. Honey tokens don’t need dedicated servers or infrastructure. They simply lie dormant until someone attempts to access them, at which point they trigger alerts.
Honey Pots: Honey pots are more complex setups. They’re full-fledged systems or servers designed to mimic an organization’s actual environment. They attract attackers by appearing as a vulnerable system that could contain valuable data. Honey pots are often set up to capture detailed information about the attacker’s tactics and tools, making them ideal for studying attacker behavior.
In short, honey pots are more comprehensive but also resource-intensive, while honey tokens are subtle, cost-effective, and highly efficient for spotting intruders with minimal setup. Honey tokens can also be sprinkled throughout various systems without needing a dedicated network, which makes them an appealing choice for many organizations.
Types of Honey Tokens
Honey tokens come in various forms, each with unique ways of tricking attackers. Here are some common types:
1. Fake Credentials: These tokens are presented as authentications that can be attempted by the attackers. When fake credential is being used it alarms the intruder and can expose information like IP address, location and so on, method of access.
2. Phantom Files: These are files which are named in such a way to be irresistible such as Sensitive Financial Data or Clients List. Once in a while, they are opened and this immediately triggers an alert to the security team.
3. Email Tokens: An email honey token appears like a real and genuine email ID but it is not used for any particular operation. If used it shows intrusion and usually means that the mail system has been breach or hacked.
4. Database Entries: This involves creating fake records in a database which only an illicit user is expected to try to pull. If attacked, these entries can be used to track the queries originating from the attacker and to collect information about the attacker’s activity.
5. API Keys: Tokens can be planted to false environment belonging to the developers. In the case if an attacker will try to use these keys the system will be able to trace the interaction noting the IP and other characteristics of the attacker.
6. Network Shares: Other Honey tokens can also include fake network shares created with the intention of raising alerts if activated. These tokens help watch out for such intruders that would be casing the network.
Thus, employing the honey tokens, an organisation would be able to safeguard different part of their infrastructure and at the same time would be able to get a broad view of the activity starting out as suspicious from different platforms.
How to Implement Honey Tokens
If you’re considering honey tokens, there are a few best practices that can help you maximize their effectiveness:
Strategic Placement: This implies that honey tokens should be placed at places where an attacker is likely to be fascinated with a sensitized data. Do not make your environment too filled with honey tokens, in case they stir suspicion.
Choose Varied Types: Having honey tokens such as fake files, fake credential, and fake API key ensure that the honey tokens covers different entry points in your environment.
Monitor Alerts Closely: The idea of honey tokens is that honey tokens are only as effective as the response to it. Ensure your security team is ready to act rapidly on any notification that is raised by honey tokens.
Log Access Attempts: Ensure that every access to a honey token is recorded through logging and tracking mechanisms that obtain comprehensive data. By doing this it is possible to gain important insights into the threats and the reasons behind them.
Regularly Update Tokens: To reduce the chances of getting detected, users should always update their honey tokens or change them occasionally. This stops the attacker from familiarizing with your security preventive measures.
Train Security Personnel: The best use of honey tokens is where the security team can understand how to interpret the alerts as well as how to manage them. Thus it is important to undergo through training and having response methods in place from time to time.
Integrate with SIEM: If possible, use honey token alerts with a Security Information and Event Management (SIEM) system. This enables real time monitoring and the general process of response is well facilitated.
Following these practices helps honey tokens become part of your organization’s security arsenal to help establish better security outcomes.
Conclusion
Honey tokens can be deployed tactfully to give an organization the competitive advantage they need to contain cyber criminals, this will also offer early signals of threat and crucial information at a relatively low cost compared to traditional security models. As cyber threats become increasingly diverse and devious, honey tokens show that a proactive and ingenious approach to protecting valuable information is something that can and should be used and practiced; after all, a little camouflage certainly doesn’t hurt when it comes to combating increasingly innovative virtual adversaries.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
