Last Updated on December 23, 2024 by Satyendra

As the acronym would suggest, the Payment Card Industry Data Security Standard (PCI DSS) is a set of global security standards for the payment card industry, which is maintained by the PCI Security Standards Council (PCI SSC). There are 12 core requirements for any complete PCI checklist, and these are explained below.
What is PCI DSS Compliance?
The Payment Card Industry Data Security Standard, or PCI DSS for short, is a set of security standards aimed at ensuring companies are adequately protecting payment card information whilst it’s being stored, transmitted, or processed. The PCI was developed by the Payment Card Industry Security Standards Council (PCI SSC), which was founded and made up of several major players in the payment industry; including Visa, MasterCard, American Express, Discover, and JCB.
PCI compliance aims to ensure that companies protect the cardholder data of their customers from theft, breaches, misuse, and fraud. It aims to do this by providing a framework that companies can use that covers various aspects of security, including firewalls, data encryption, antivirus, and implementation of data governance practices. PCI also provides guidance for security testing and monitoring and the implementation of proper security policies.
PCI is not a one-time event, it’s an ongoing process that involves regular assessments and audits. Depending on the volume of card payments that your company handles, you may be required to submit to a specific level of compliance validation, of which there are several. Lager organizations might need on-site assessments conducted on an annual basis by Qualified Security Assessors (QSAs), whereas smaller companies might be able to get away with a self-assessment questionnaire.
Non-compliance with PCI can be devastating to companies. Large fines or increased transaction fees can be crippling to everyday business. In some cases, non-compliance could even lead to the loss of the ability to process credit card payments altogether.
Why is PCI Compliance Necessary?
PCI compliance is important for entities that handle electronic payments to reduce costs, increase efficiency, and improve the accuracy of transactions. Being PCI compliant protects cardholder data, helps prevent attacks, and increases confidence in using card payments. Non-compliance can lead to penalties, service suspension, and financial losses for the non-compliant
What level of PCI applies to you?
PCI Compliance comes in four different levels based on the number of credit card transactions you have per year.
| Merchant Level | Applicable to |
|---|---|
| PCI Compliance Level 1 | Sellers that process over 6 million Visa or MasterCard transactions per year |
| PCI Compliance Level 2 | Sellers that process 1 million to 6 million Visa or MasterCard transactions per year |
| PCI Compliance Level 3 | Sellers that process 20,000 to 1 million Visa or MasterCard transactions per year |
| PCI Compliance Level 4 | Sellers that process lesser than 20,000 Visa or MasterCard transactions per year |
Consequences of Failing a PCI Audit
- Lost confidence which forces customers to go to other merchants
- Diminished sales
- Fraud losses
- Fines and penalties
- Lost jobs
- Going out of business
- Legal costs, settlements, and judgments
12 Requirements for PCI Compliance
The PCI framework is built around 12 core requirements. Each requirement is critical in ensuring that businesses securely handle and protect sensitive cardholder information. Here’s a closer look:
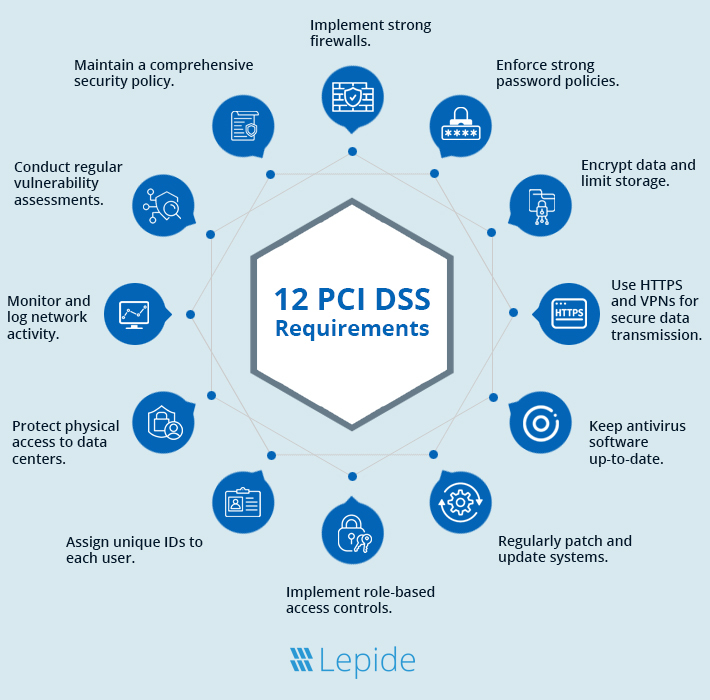
1. Install and Maintain a Secure Network
One of the major compliance requirements of implementing PCI revolves around network security. Firewalls and their proper settings must be properly implemented in organizations to shield cardholder data from such individuals. Maintenance of a network is as important as its construction, and it plays the crucial role of protecting a network from threats of cyber attacks. Another benefit of the firewall is that you can set a time to go through your configuration regularly, ensuring that none has been breached and fixing them before they become a problem.
2. Implement Strong Password Protocols
Booting with the default password that comes together with the hardware or software by its vendors is an open invitation to hackers. Updating these credentials with strong and unique passwords is a fundamental but effective process. Password policies should also have direction on developing passwords that would be lengthy, compounded, and hard to come by. This also guards your systems against brute-force attacks and unauthorized access.
3. Secure Stored Cardholder Data
Even though cardholder data is stored and processed within the environment, inadequate security measures result in disastrous breaches. The secure storage of card data remains a core goal of implementing data protection strategies in the company, with data encryption being the main strategy among the available methods. This ensures that even if the attackers infiltrate the system they cannot decipher the information due to strong cryptography algorithms. It is also essential to validate if it is necessary to store certain cardholder data—removing it if not, reduces exposures.
4. Encrypt Transmission of Cardholder Data
There are cases where the information transmitted is sensitive and passage through open or public networks exposes it to interception. Under PCI DSS, all transfers of cardholder data have to be encrypted. Web address bars accompanied by HTTPS or VPN guarantee that the information does not fall into the wrong hands. As such, prioritizing secure communication perpetuates customer trust and minimizes several risks at once.
5. Use and Update Anti-Virus Software
Anti-virus software is your shield that helps you protect yourself from Malware and other dangerous threats. This software should always be up to date if the system is to be used to process or store cardholder data. It is true that cyber threats are ever changing and having weak mechanisms places your systems in a vulnerable position. Both updating and scanning are beneficial in a way that they prevent probable risks from looming in.
6. Develop and Maintain Secure Systems
Your systems or applications can be predisposed to hackers if they have certain weaknesses. These risks have to be contained by applying patches and updates the instant they turn out available. There are also periodic security audits and vulnerability assessments which assist in determining what needs urgent attention so that the systems remain safe.
7. Restrict Access to Data
Some of the users in your organization do not require access to these sensitive cardholder details. PCI DSS principle of least privilege is about providing access to information or systems only to individuals who need it for performing certain tasks. Indeed, if you adopt role-based access controls, you eliminate the risk level of internal breaches and simplify tracking of data access significantly.
8. Assign Unique User IDs
The use of shared login is an absolute security vice and people should avoid it like stale bread. This is especially possible if you have a unique identification number for every user who is in your system, then those you find guilty of any wrongdoing you can easily point a finger at them. It is significant for security and to meet compliance requirements. Transparency is critical here. Moreover, they imply a more unproblematic audit or investigation when irregularities are identified due to the IDs given to each employee.
9. Restrict Physical Access to Data
While speaking about security, people tend to focus on the digital side of it, but physical security is simply as important. Some of the risks that might affect cardholder data include any unauthorized physical contact with the servers, data storage devices, or systems that can be detrimental to the security of the cardholder’s data. These areas require the application of access control, the use of surveillance cameras, and logs to make certain that only approved individuals can access these systems.
10. Monitor and Log Access to Data
Another important aspect is that the monitoring of the systems should be constant. Access to the cardholder data must be monitored and this requires the enabling of logs in order to capture all activity. It is also important to reference these logs often to check for signs of foul play, such as break-in attempts or higher-than-normal levels of use.
11. Test Security Systems Regularly
Cybersecurity is not a ‘set and forget’ concept. Security needs to be tested regularly, using vulnerability scanning and penetration testing. There is no external entity that threatens to exert force over you; these assessments expose latent vulnerabilities and guarantee sufficient security. External tests assess the organization at the entry point such as the firewall while internal tests determine how secure the network is once attackers get in.
12. Maintain a Policy for Information Security
The essence of PCI DSS compliance is underpinned by a sound security policy. Such a policy should clearly define with regards to your organization on the protection of sensitive data. It is also essential to maintain the relevance of this document about changes in technology, new laws, and new risks. This helps to keep the employees of your team informed and to guarantee they follow the implemented policy.
PCI Compliance Checklist
Now that we’ve covered the requirements, let’s translate them into a practical checklist you can follow to achieve and maintain compliance:
1. Secure Network Setup
- Implement firewalls on systems to protect cardholder data against any unauthorized access.
- Do not use standard credentials and passwords for these network equipment, instead use a secure, unique one.
2. Cardholder Data Protection
- Protect cardholder data during transmission over public networks using standard protocols appropriate in industries.
- Stored cardholder data must also be encrypted or truncated to prevent other unauthorized persons from sighting the information.
3. Vulnerability Management
- Update anti-virus software on all systems; with special consideration on systems most likely to be infected by malware at frequent intervals.
- Scan sources of vulnerability regularly and fix all discovered security vulnerabilities as soon as possible.
4. Access Control Measures
- Limit the availability of documents to employees who need them, which means that access is carried out on the principle of necessity.
- Implement two-factor authentication (2FA) or two out of three-factor authentication (3FA) for high-risk systems.
5. Monitoring and Testing of the network
- Control all access to network resources and cardholder data through mechanisms for automated logging and reporting.
- Invest in Penetration testing and vulnerability scanning since they will help identify security gaps within the company’s IT system.
6. Security Awareness and Policies
- Establish non-compromisable specific security policies that are to be followed by all employees and vendors as well as prepare detailed records of them.
- Invest in staff training and holding seminars to update the organization’s employees on protocol and risk factors.
7. Incident Response Plan
- Organize and implement an incident response plan so data breaches can be handled properly in optimum time.
- Practice breach situations from time to time to ensure that the given response plan is not a mere classic.
8. Continuous Compliance
- Approximately, make certain changes to security policies periodically based on these new developments in the PCI DSS framework.
- Conduct annual or bi-annual audits and Self-Assessment Questionnaires (SAQs) to pinpoint the grievance of non-compliance.
How Can Lepide Help You with PCI Compliance?
The Lepide Data Security Platform provides in-depth auditing of your cardholder data, as well as detailed reports that are customized to meet the requirements of PCI. The Lepide Data Security Platform will aggregate event data from multiple platforms, including the most popular cloud platforms, and display a summary of important events via a centralized dashboard.
This will help you determine who is accessing your data, as well as determine who should have access to your data.
The Lepide Data Security Platform can deliver real-time alerts on changes made to any data that falls under PCI DSS, which might include access/changes to payments data, as well as changes to permissions of user accounts that have access to payments data. You can also audit computers that store payment data, to ensure that any changes are authorized and the data is secure.
If you’d like to see how the Lepide Data Security Platform can help you achieve PCI compliance audit, schedule a demo with one of our engineers.
FAQs
What does it mean to be PCI compliant?
Being PCI Compliant indicates that your business is adhering to the data security regulations of the Payment Card Industry (PCI) and has met all the requirements for keeping customer information secure.
Does my e-commerce site need to be PCI compliant?
It is mandatory for e-commerce stores that store credit card information, conduct financial transactions, or accept payments using credit, debit, prepaid cards, or other forms of payment to comply with the PCI regulations. Failure to comply could result in penalties and the loss of customer trust and harm to your business’s reputation.
Am I required by law to become PCI compliant?
While being compliant with the PCI standards is not mandatory under federal law, certain states mandate that e-commerce websites comply with it. It is advisable to gather information about the requirements of your local or regional government to understand how the laws relate to your business. Failing to comply with the PCI standards jeopardizes the ability of merchants to provide payment processor services from their acquirers or acquiring banks.
Is it difficult to become PCI compliant?
PCI DSS holds merchants accountable for maintaining secure networks and systems, safeguarding cardholder data, and enforcing strong access controls. As such, achieving full compliance can be very demanding, and requires a high level of attention to detail.
Which version of PCI should I use?
The current version of PCI DSS is 4.0. Version 3.2.1 will remain operative until 31 March 2024, beyond which it will be phased out. Subsequently, PCI DSS v4.0 will be the only version in use. Any queries regarding compliance, including whether a PCI v3.2.1 report can be submitted after its termination date, must be directed to the entities in charge of the compliance procedures, such as payment brands and acquirers.
Who do I contact about specific PCI reporting requirements?
Each PCI SSC Participating Payment Brand member (American Express, Discover, JCB International, Mastercard, UnionPay, and Visa) has its own programs to ensure the safety of affiliated payment card data. If you require information about compliance programs and reporting requirements, you should contact the payment brands directly. You can find a list of contact details on the official PCI Security Standards website. PCI SSC advises entities to be mindful of any local laws and regulations that could impact the applicability of PCI standards.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
