Separation of duties (SoD) – also referred to as “Segregation of duties” – is a critical, yet often overlooked area of IT security. Essentially, the purpose of SoD is to help organisations protect themselves from fraudulent behaviour by ensuring that no single individual can act alone to subvert a critical process for their own personal gain.
SoD is an area that comes under close scrutiny during compliance reviews, and will likely become even more relevant once the GDPR comes into effect. If an organisation’s key processes are not segregated in a manner that satisfies the regulatory bodies, those bodies will likely conduct a thorough investigation into the integrity of the organisations security strategy. In order to ensure compliance with SOX, PCI, GLBA, FISMA, HIPAA and GDPR etc., organisations must take the necessary steps to ensure that all critical processes are disseminated amongst multiple people.
To help you determine if your organisation needs to implement SoD, there are two basic questions that you will need to answer:
- Can any one person can alter or destroy sensitive data without being detected?
- Does any one person have influence over controls, design, implementation and reporting?
Of course, in an ideal world you would have answered “no” to both questions. However, since you’re reading this article, there’s a good chance you answered “yes” to both questions. In which case, you may want to continue reading…
When segregating duties, organisations must ensure that the individual who is responsible for developing the security strategy is not the same individual that is responsible for conducting audits, creating reports and testing the security implementation. Additionally, organisations must carefully consider who should be reporting to who. For example, the individual who is responsible for overseeing the security strategy should report to the chief security officer (CSO), and the chief security officer (CSO) should in turn report to either the CEO, board of directors, or chairman of the audit committee. Alternatively, organisations may choose to rely on a third-party to monitor security. A third-party can carry out surprise audits, and should also report to either the CEO, board of directors, or chairman of the audit committee.
Of course, in order for SoD to be effective, organisations will need a way to accurately and promptly identify “who, what, where and when”, important changes are being made. While it is theoretically possible to obtain such information from native server logs, they are usually cryptic and it may take time to extract meaningful results from them.
A better option would be to use specialised auditing solutions that can aggregate information from multiple sources and display this information via a single pane. For those using Active Directory, Lepide Data Security Platform provides is a scalable and cost-effective solution that can detect and respond to interactions with critical data and provide intuitive, real-time alerts and reports. It can also display current permissions, monitor changes to those permissions and provide information about how those permissions are granted.
Permissions are used to define different duties assigned to users. Managers may have full administrative privileges and executives may simply have normal user rights. Lepide Data Security Platform keeps a track of all permission changes across all platforms including Active Directory, Group Policy Objects, Exchange, SharePoint, SQL Server, Windows File Server and NetApp Filers.
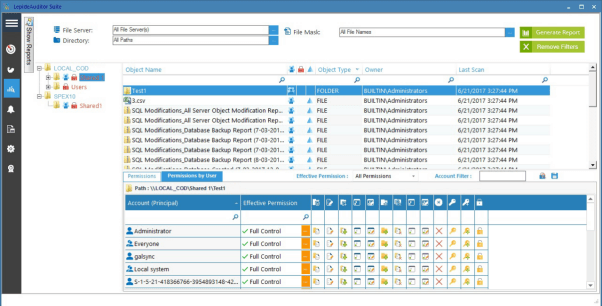
Similarly, on some critical files storing business data, administrators may have full control whereas users may have only rights to view the data. If a change occurs that leads to a normal user having excessive levels of privilege, you will be able to see this using Lepide’s current permission report:
Conclusion
In the event of a data breach, solutions like Lepide DSP will allow you to effortlessly carry out a forensic investigation into the cause. Lepide Data Security Platform also allows you to carry out this investigation in a number of ways. It comes with a password-protected Web Console that can be hostel on an SSL-layer connection and allows administrators to define which users have access to which reports. Reports can also be shared via email at scheduled intervals or saved at a shared location whilst notifying the recipients. This, combined with the other steps mentioned in this article should help you ensure that no one individual can subvert a critical process for their own personal gain.

