
According to the mid-year data breach report, published by the Identify Theft Resource center, the number of data breaches in the US have hit a 6 month record high of 791. Compared with figures from 2016, this represents a 29% jump in the number of reported breaches. Should this trend continue, it is estimated that the total number of breaches in 2017 could rise to a staggering 1,500.
The ITRC analyses data breaches from five industry sectors: finance, healthcare, government, education and business. The report claims that the business sector is currently experiencing the highest number of data breaches, and has accounted for 54.7% of the breaches so far in 2017. This is followed by healthcare, education, finance and then government. The healthcare industry has experienced the biggest increase, accounting for 30.7% of the total breaches, up from 22.6% in 2016.
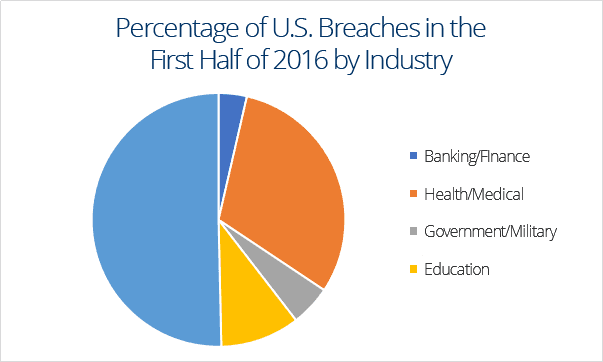
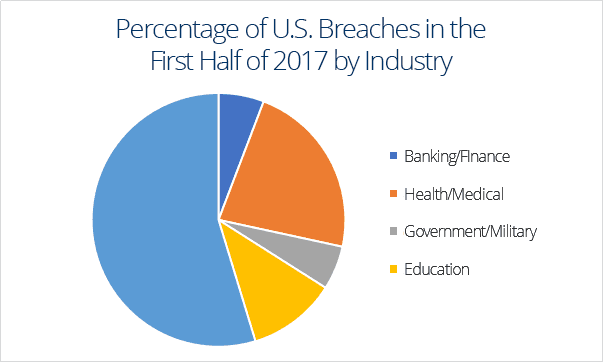
Source: mid-year data breach report
The leading causes of data breaches include phishing, ransomware/malware and skimming (for credit card information), which accounted for 63% of total breaches. The rest of the causes were down to human error and negligence. The report also found that 67% of breach notices failed to include information about how many records had been compromised – a figure which was also a record high.
Pam Dixon, executive director of the World Privacy Forum, referred to this lack of transparency as being “dangerous”, and said that “Breach notifications need to help, not hinder, solving the problems that data breaches can bring.”
So what do organisations need to do to bring these numbers down?
As stated in the report, phishing attacks are the most common cause of data breach. Such attacks present cyber-security experts with an impossible task, since, with the exception of SPAM filters and various email configuration settings, the only real way for organisations to protect themselves from phishing is to ensure that all staff members are well trained and vigilant in spotting suspicious emails. As you can imagine, this is far from a concrete security strategy. While the same is true for ransomware attacks, there are at least some things that organisations can do in order to limit the damage caused by such attacks.
For example, organisations should keep a backup of their most important files, use the latest anti-virus tools, ensure that they have a well configured Firewall, use Software Restriction Policies to ensure that executables are not able to run in certain locations, and block known-malicious IP addresses.
Additionally, using tools such as Lepide Data Security Platform, it’s possible to spot bulk changes that match a given threshold. For example, if 5 or more files have been deleted from a single folder within 5 minutes, then the Administrator will receive an alert through email and a user-created script will be executed that could allow you to restore these files from backup.
The script may disable a user account, change firewall settings, stop a specific process, shut down the server, or anything else that might help prevent the attack from spreading.
Conclusion
When dealing with human error and negligence, the most effective strategy, other than educating staff members about security “best practices”, is to ensure that you are able to know exactly where your sensitive data is located, who is accessing this data, and when. Lepide Data Security Platform can collect information about such changes and present it via a single dashboard. On top of which, the solution can provide detailed reports and real-time alerts about changes to important files, folders and permissions. It can alert you when accounts are created/modified/deleted, track logon activity, automate the removal of inactive user accounts, track privileged mailbox access, automate the process of reminding users to reset passwords, and much more.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
