Just as files inherit permissions from their parent folders, in Active Directory, user and group objects have their own access control lists (ACLs) that determine who can view or edit their properties. Instead of individually controlling administrative authority for each user or group object, it is more practical to collect them into an OU and grant the necessary authority to a subadministrator over that OU. The permissions defined in an OU’s ACL will affect all the users and groups within that OU, similar to how folder ACLs apply to all the files within a folder. It is worth noting that a user can be a member of multiple groups, but can only reside in one OU, just like a file can only be in one folder. The significance of OUs in efficiently managing users and computers within Active Directory cannot be overstated. In this guide, we will explore essential best practices for OUs, and explain how they differ from groups and default containers.
What are Active Directory Groups?
Active Directory (AD) groups are integral to Microsoft’s Active Directory service, a key component in Windows network environments. These groups serve pivotal roles in resource management and access control. Two primary types exist: Security Groups, managing user and computer access to shared resources, and Distribution Groups, facilitating email distribution without security-related permissions.
Groups can include both users and computers, enabling streamlined permission and access control. Nesting is supported, allowing groups to be members of other groups, fostering a hierarchical structure for efficient management. Organizational Units (OUs) further aid in organizing groups within the Active Directory’s hierarchy.
Group scopes define their reach: Domain Local is limited to a specific domain, Global extends across any domain in the Active Directory forest, and Universal covers any domain in the forest. Active Directory groups synergize with Group Policy Objects (GPOs) for policy enforcement across networks, applying policies based on group memberships.
In essence, Active Directory groups provide a flexible and efficient means of organizing and managing users, computers, and resources in networked environments, streamlining permission assignments and policy applications.
What are Active Directory Organizational Units (OUs)?
Active Directory consists of domains, which are governed by domain controllers. Domains can be organized into trees with trust relationships, and trees can form larger forests. Organizational units (OUs) are the smallest unit within Active Directory and allow admins to define specific group policy settings and delegated admin rights. OUs can contain users, computers, groups, and other OUs. They are used for delegated administration, allowing admins to restrict control to specific OUs, and managing group policy, applying settings to specific parts of Active Directory.
Organizational Units (OU) are helpful for applying group policy settings to specific users, groups, and computers in a domain. They are especially useful when different IT teams manage separate sub-organizations within a domain. Creating separate OUs allows each IT team to administer their own policies for the users and computers within their unit. OUs also allow for the delegation of administrative tasks to users or groups without giving them full administrator privileges.
There are various common administrative tasks that can be delegated through organizational units (OUs). These tasks include managing users by creating or deleting user accounts, managing groups, modifying group memberships, managing group policy links, and resetting passwords for user accounts. By assigning these tasks to specific OUs, administrative responsibilities can be efficiently distributed within an organization.
How Do I Create an Organizational Unit?
There are several ways to create a new organizational unit in Active Directory, including through the Active Directory Administrative Center, Windows Server Manager or Remote Server Administration Tools (RSAT). You can also use the PowerShell cmdlet New-ADOrganizationalUnit, however, it is generally easier to create and manage OUs through a visual interface to ensure proper structure.
The Difference Between OUs and Groups
Initially, organizational units and groups appear similar as they both provide structure to Active Directory by grouping similar objects like user accounts or device accounts. However, in practice, organizational units and AD groups have distinct purposes. Organizational units are used to delegate administrative rights and apply group policy settings, whereas groups are employed to manage permissions. For instance, NTFS permissions and share permissions on the file server or mailbox permissions in Exchange can be controlled by groups. Additionally, Active Directory group membership can determine access to third-party applications and resources.
Below are some of key differences between Active Directory groups and organizational units:
- Organizational units can encompass group policy objects (GPOs), while AD groups cannot.
- Organizational units can delegate admin rights, but AD groups cannot.
- AD groups can manage permissions, while organizational units cannot.
- AD groups possess their own security identifier (SID), whereas organizational units do not.
The Difference Between Organizational Units and Containers
When you set up Active Directory, Windows automatically generates default containers to store users, computers, and other objects. These containers serve a similar purpose as organizational units (OUs), which are actually a type of container. However, there is one crucial distinction: group policy objects can only be applied to OUs, not to containers. Because of this, it is generally advised to replace the default containers in AD with your own OUs for managing user and computer accounts. With these OUs, you can effectively manage global policies that should apply to all accounts or devices in your network. To ensure that new accounts are created in OUs rather than default containers, you can redirect account creation using the redirusr and redircmp commands.
Organizational Units in Azure AD?
Instead of using organizational units, Azure Active Directory uses administrative units (AU). Like OUs, administrative units can hold users, devices, and groups, but cannot contain other administrative units. AUs allow for assigning specific administrative roles to users that are limited to objects within the administrative unit. Unlike organizational units, administrative units do not support group policy objects as Azure AD does not have GPOs.
Organizational Unit Best Practices
Below are some of the most notable best practices to follow when using organizational units:
Construct a Logical Framework
Admins can arrange a domain by grouping users and computers into organizational units (OUs). The number and structure of OUs needed depend on the specific IT landscape and requirements. There are various ways to build and nest OUs, but it is crucial to find a structure that works, and stick to it. Similar to role-based access control, many businesses design their OUs to align with their company structure, creating separate OUs for different offices and departments. However, it is not mandatory to follow this approach. The main consideration when planning OUs is to determine which parts of Active Directory require delegated administration or unique group policies. For instance, it may be beneficial to divide computer accounts based on device type (e.g., desktop vs. laptop) to apply different configurations to each.
Separate Users and Computers
Given that most organizations apply distinct group policy settings to user and computer accounts, it is logical to place these objects in separate OUs for easier administration. These OUs can establish global settings for all user/computer accounts, while nested OUs can define specific rules based on the planned OU structure.
Use a Consistent Naming Convention
To facilitate long-term maintenance and administration, OUs must have clear names (and possibly descriptions) that clearly indicate their purpose and scope. Furthermore, all administrators should follow the same naming approach. Inconsistencies, such as one admin naming OUs based on department and another based on job titles, can lead to confusion. Documenting a consistent naming convention is the simplest way to enforce uniformity.
Use Inheritance for Group Policy Assignment
While OUs allow admins to create distinct rules for different parts of Active Directory, most organizations have universal settings that should apply to all users and devices. Inheritance is an efficient method to ensure global configurations are applied to all accounts. By placing a group policy object with these core settings in a parent OU, nested OUs can govern specific settings for subsections of the Active Directory.
Use Nested OUs for Exceptions
Nested OUs not only extend inherited group policies but also allow for policy overwrites when necessary. For example, an organization may use a group policy to automatically lock screens after 10 minutes of inactivity for security reasons. However, doing so may cause issues during presentations and video calls in conference rooms. The solution is to create a new OU within the existing OU for conference room computers and apply a new group policy object with an extended time limit. These devices still inherit relevant settings from their parent OU, but the undesirable setting is overwritten by the new policy.
How Lepide Helps Secure AD Groups and OUs
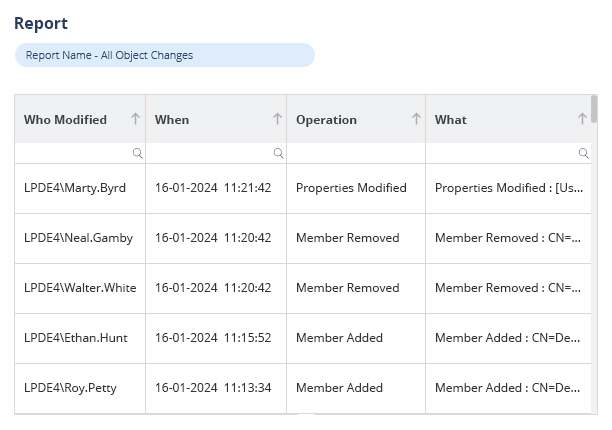
Lepide Auditor for Active Directory is a comprehensive AD auditing tool which tracks every change made to Organization Units (OUs) and Groups. It can track whenever any OU or Group is created, deleted or modified in real time.
Lepide Auditor examines every modification made to Active Directory to help find the answers to the four most crucial IT auditing questions: who, what, when, and where. Enhancing security and compliance efforts, the solution provides a thorough audit record of user activity, group policy changes, permission changes, etc.
To learn more about how Lepide Auditor can assist you in managing and safeguarding your OUs and Groups, download a free trial or arrange a demo with one of our engineers.