Active Directory is a directory service, developed by Microsoft, which operates as a core component of Windows Server, making it one of the most widely adopted on-premise directory services available. AD uses groups to streamline the management of user accounts and computers across multiple AD domains by organizing them together and granting universal access privileges.
What are Active Directory Groups?
An Active Directory Group represents a collection of objects which may include users, devices, and even other groups encompassing various entities. Groups can be perceived as containers that not only accommodate users but also hold supplementary objects as members. Users are strategically grouped according to a specific criteria, granting them access to designated resources. AD groups help to streamline network maintenance and administration by allowing the management of the group as a cohesive unit. This means that rather than individually configuring settings for each user or object, adjustments can be applied to the entire group, simplifying the overall process and optimizing efficiency.
Types of Active Directory Groups
There are two types of Active Directory groups: Security groups and Distribution groups. Each type of group has a different group scope. The group type determines the task to be performed, while the group scope determines the group’s membership eligibility.
- Security groups– Security groups grant users access to shared resources. By adding a user as a member of a security group, they will inherit all the permissions associated with that security group. For instance, you may create a group called “Marketing” and grant it permissions to read and edit files within designated folders, as well as execute specific applications. Any user who is a member of that group will have the ability to perform those actions. Please note that security groups can also function as distribution groups in Exchange. These are referred to as security-enabled distribution groups or mail-enabled security groups.
- Distribution groups– Distribution groups enable AD administrators to create a user pool for sending common messages or emails using Microsoft Exchange and similar applications. Admins can broadcast messages to all mail-enabled members of these groups. However, it is important to note that these groups are not suitable for granting access rights to network resources due to inadequate security measures.
Active Directory Group Scopes
Each group within Active Directory has a specific scope that determines the type of objects it can contain and the types of groups it can be a member of. There are three main scopes available:
- universal groups
- global groups
- domain local groups
Universal groups
Universal groups are used to consolidate groups across domains. Members of different domains in the forest, including global and universal AD users and groups, can join universal groups. Multiple universal groups can be nested in the same forest, and a universal group can apply for membership in a domain local or local group within the forest. Users in universal groups can access network resources in any domain within the forest. It is recommended to create universal groups when working with multiple domains. To effectively consolidate groups, it is recommended to add user accounts to groups with global scope and then nest those groups under a group with universal scope. This approach ensures that changes in membership within global groups do not affect groups with universal scope. Additionally, it helps control replication by triggering forest-wide replication for universal groups and domain-level replication for global groups.
Global groups
Global groups are commonly used to assign permissions to users with similar job responsibilities, such as a group for all members of the Human Resources department. Global groups are also useful for managing objects that require daily maintenance. Changes made to accounts within global groups are not replicated to the global catalog, making them suitable for such purposes. Nesting of global groups within the same domain is possible, and a global group can also be part of a domain local or universal group from another domain.
Domain local groups
Domain local groups are well-suited for managing permissions to domain-specific resources. For example, you can create an AD group called MarketingPrinter with domain local scope and grant it access to a specific printer which is accessible to the Marketing team. Multiple global groups can be added to this domain local group, allowing members of those global groups to access the printer. Network administrators create local groups using the Microsoft Management Console (MMC) and local Security Account Manager database. Members of these groups can only access resources on the local computer. Local groups can include domain local groups from the same domain and global and universal groups from other domains within the forest. They operate independently of domain controllers, distinguishing them from domain local groups in AD.
Other Groups
Dynamic groups– Dynamic groups simplify group management by automatically adding or removing users based on a specific criteria. For example, a dynamic group can include users from all domains who belong to a particular department. PowerShell scripts and third-party tools are used to create dynamic groups since there are no built-in tools available.
Special identity groups– Special identity groups are similar to security groups but with automatic membership management. Once a user accesses a resource or logs into a system, they become part of these groups. Group scope, membership view, and modifications are not available for these groups. Examples of special identity groups include Anonymous Logon, Authenticated Users, Creator Owner, and Local Service.
How Lepide Change Reporter (Free Tool) Helps
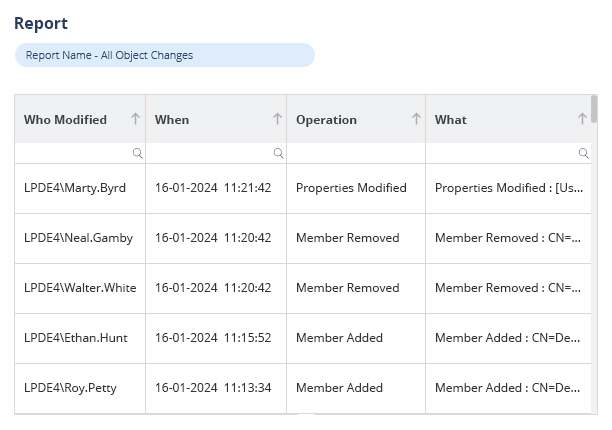
Lepide Change Reporter for Active Directory (Free Tool) tracks and audits changes to group membership. It can show you who added or removed members from a group, when it was done, and from where. This helps to ensure that only authorized changes are made to groups, and that any unauthorized changes can be quickly identified and investigated.
Additionally, Lepide’s Free Tool can help to secure Active Directory groups by providing reports on group membership changes. These reports can be used to track trends in group membership changes over time, and to identify any patterns that may indicate suspicious activity.