Last Updated on December 17, 2024 by Satyendra

Having data open to everyone is a surefire way of leaving yourself exposed to potential data breaches or privilege abuse. Unfortunately, many organizations seem to be making the same mistake when it comes to open shares. Fixing open shares can help improve data security, and in this blog, we will find out how.
What Are Open Shares?
An “open share” is a resource that is accessible to most, or all users on a given network, including guest users. However, files and folders that are accessible to all authenticated users, or all users who belong to an ‘Open Access Group’, may still be referred to as “open shares”. These types of groups can include:
- Everyone – all users and accounts that have authenticated to the system.
- Authenticated Users – everyone except build-in, non-password protected groups.
- Anonymous Logon – a built-in group that enables users to access resources from an anonymous account.
- Domain Users – a default group within Active Directory to which users’ accounts are automatically added.
Organizations will often allow open shares to make it easy for end-users to easily access a given resource, however, if these open shares are not managed correctly, they can create security risks with potentially catastrophic consequences.
The Effect Open Shares Have on Data Security
Open shares are especially problematic when dealing with resources that contain sensitive data, such as Personally Identifiable Information (PII), Protected Health Information (PHI), and Payment Card Information (PCI), as it makes it a lot easier for hackers to gain access to this data.
According to a 2014 study carried out by the Ponemon Institute, “71 percent of end users say they have too much access to confidential corporate data”, which is the consequence of inappropriate access privileges.
There are times when it is necessary to have resources that are accessible to all users on a network. Such resources might include calendars, press releases, job descriptions, and marketing materials.
Whilst allowing all users read access to these resources is unlikely to present any major problems, it only takes one employee who has been wrongly granted write access to a resource to result in a serious security incident.
A lot of malware and viruses are designed to spread using open shares. A hacker may obtain a legitimate set of credentials and use those credentials to infect a given resource with malware – assuming they have been granted full write access to the resource in question.
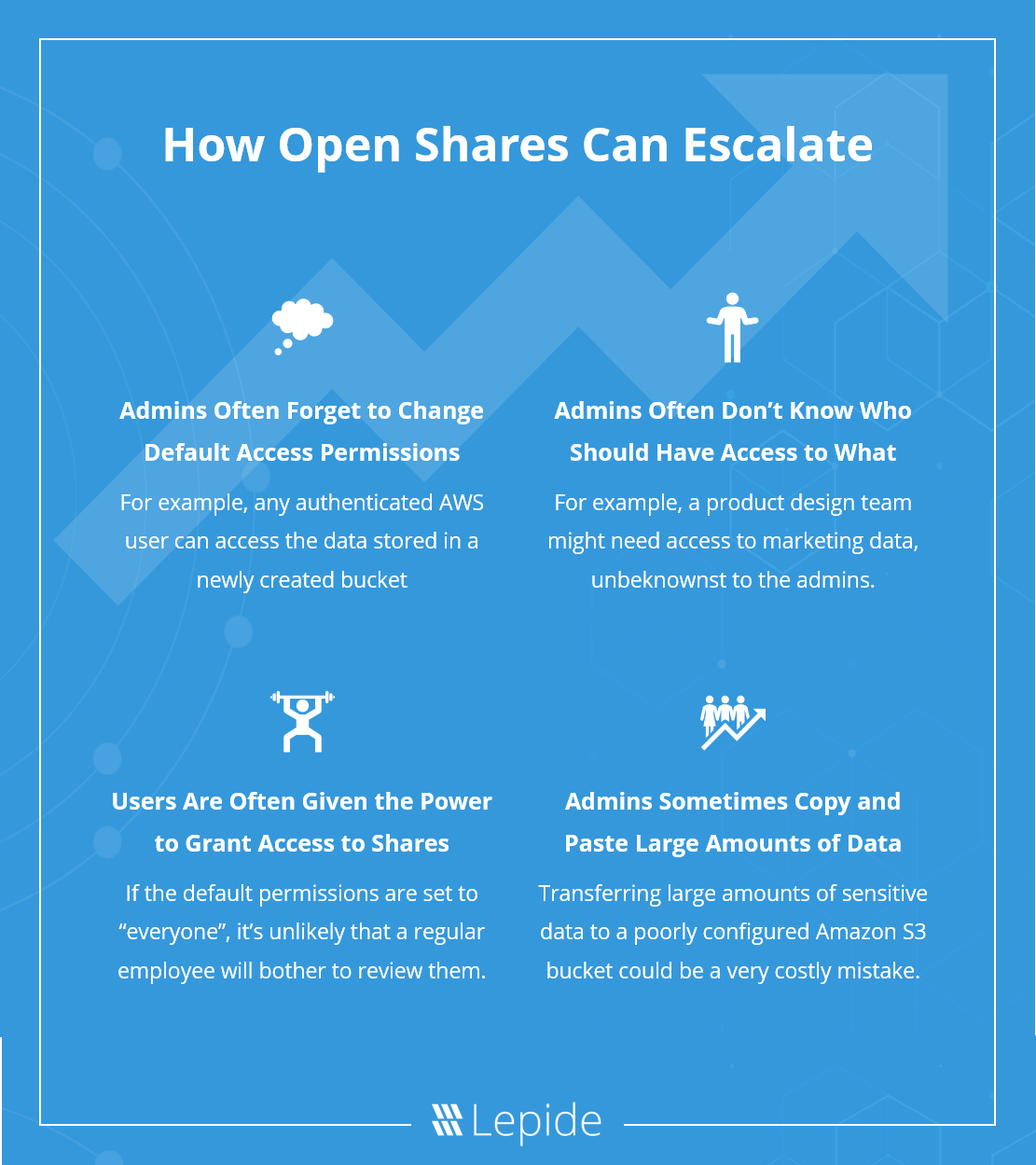
How Open Shares Can Escalate
There are numerous reasons why organizations might end up with an almost unmanageable number of open shares. However, we can usually boil it down to one of the following four reasons:
1. Admins often forget to change the default access permissions
It is often the case where admins simply fail to change the default access permissions for a shared resource. For example, in Windows, the default permission for a new share is “everyone”.
Likewise, in recent times we’ve seen a number of data breaches caused by poorly configured Amazon S3 buckets. By default, any authenticated AWS user can access the data stored in a newly created bucket, and many admins are simply not aware of this, or at least, they fail to carefully review the configuration settings before uploading sensitive data to them.
2. Admins often don’t know who should have access to what data
It is sometimes tricky to accurately determine who should and shouldn’t have access to a given resource, which is one of the main reasons why administrators tend to resort to open shares.
For example, the product design team might need access to marketing data, but the administrator wouldn’t necessarily assume this to be the case. As such, they may choose to assign access controls to shares that are not as restricted as they should be.
3. Users are often given the power to grant access to shares
Regular employees are not security experts and don’t really understand the importance of controlling access to certain types of data.
Granting a regular employee the power to grant access to shares is not a wise move. Let’s face it, people are lazy. If the default permissions are set to “everyone”, it’s unlikely that a regular employee will bother to look at them, let alone change them to something more suitable.
4. Admins sometimes copy and paste large amounts of data
It is often the case where organizations need to migrate large amounts of data to a new server or platform. However, in doing so they might lose most or all of the access permission that has been assigned to the data, thus potentially leaving sensitive data open for everyone to see.
While there are tools available that can migrate large sets of data, whilst preserving access rights, many admins are either unaware that these solutions exist, or are simply too complacent to use them. Transferring large amounts of sensitive data to a poorly configured Amazon S3 bucket (as mentioned above) could be a very costly mistake.
How to Track and Manage Open Shares
Given the complex nature of assigning access controls to shares, it is a good idea to use automation to help to minimize the number of unnecessary open shares on our network. While it is possible to use a PowerShell script to list all open shares on a network, there are more advanced tools available that can automatically scan for open shares on a network.
Most sophisticated solutions use Machine Learning (ML) to learn the typical usage patterns of each user account and assign access controls according to the resources they access, including when, and how often they are accessed.
Of course, we mustn’t rely solely on automation to ensure that open shares are kept under control. Automation can be very useful for identifying open shares and reporting them to the administrator, but the administrator must review all open shares manually to prevent their misuse.
Auditing and Monitoring Open Shares
As mentioned, hackers who have gained access to a legitimate set of credentials, regardless of how privileged the hijacked user account is, can leverage open shares that have full write access, or even create and share resources that are infected with malware.
It is thus important to know when files and folders have been created and shared, as well as who is creating, sharing, and accessing them.
Using a open share auditing solution, administrators will be alerted, in real-time, when files and folders are created, shared, accessed and modified, and by who. The administrator can then manually review the events to ensure that they are being performed by a legitimate user and that they are not creating a security risk. Given that open shares are particularly problematic when using cloud platforms, you will need an auditing solution that can aggregate and correlate event data from multiple cloud platforms, such as Amazon S3, Office365, Dropbox, and so on.
How Lepide Helps Clean Up Open Shares
The Lepide Data Security Platform comes with a live Risk Analysis Dashboard that will enable you to see exactly how many open shares you have in your environment so that you can take steps to clean them up. If you would like to see this dashboard in action, schedule a demo with one of our engineers today.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
