Account lockouts are a common problem experienced by Active Directory users. They arise because of Account Lockout Policies configured in the default domain policy for the Active Directory domain. In this article, we will go through some of the root causes of account lockouts and the way to simplify the troubleshooting process.
Why Accounts Keep Getting Locked Out Frequently in Active Directory? 9 Common Reasons
Account lockouts occur when incorrect login credentials are used, resulting in a user account becoming locked. Active Directory has a threshold in place for logon attempts and when that threshold has been met, the user is locked out by Active Directory.
The threshold can have a duration limit, where it can lock the user account for a specified time period. Attacks such as brute force password guessing, password spraying, and Denial of Service (DoS) can all cause lockouts. This then affects the user’s ability to access resources, resulting in more help desk tickets and decreased productivity for the entire organization.
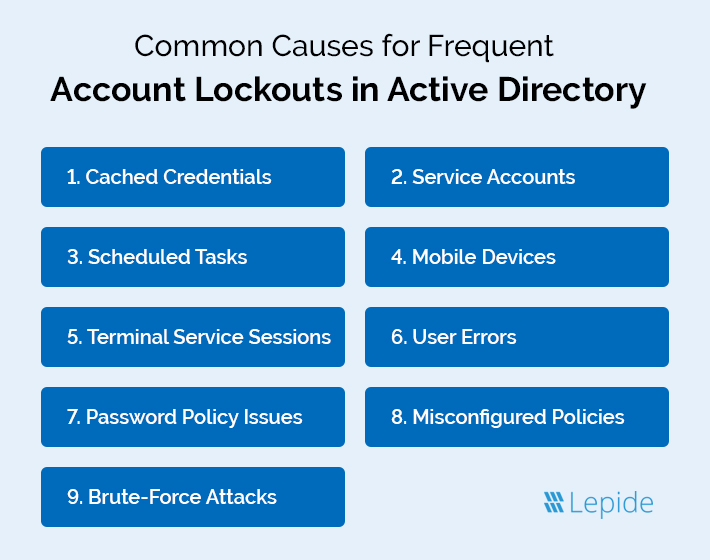
There are various other reasons why account lockouts may occur, and identifying the root cause is an essential first step in resolving the issue. Here are some of the common causes for Active Directory account lockouts:
- Cached Credentials
- Service Accounts
- Scheduled Tasks
- Mobile Devices
- Terminal Service Sessions
- User Errors
- Password Policy Issues
- Misconfigured Policies
- Brute-Force Attacks
1. Cached Credentials
Login tokens stored by authentication systems often cause unintended authentication problems because they hold information different from current security standards across multiple devices. The system automatically locks accounts when users fail repeated authentication attempts because their credentials do not match the active security policies. This becomes more of a problem when devices and networks increase in complexity.
2. Service Accounts
Service accounts designed for system-level background operations have unique operational risks that increase the probability of account lockouts. Multiple authentication bottlenecks occur when systems deploy expired passwords that are hard-coded, along with insufficient monitoring practices and complicated system integrations between various platforms. Security-relevant password rotation protocols might disrupt essential systems because they do not support safe credential transition during automatic rotations.
3. Scheduled Tasks
Enterprise automation heavily relies on scheduled tasks, which present challenging authentication procedures that generate unexpected account lockouts. System-level operations managed by automated processes require precise user credentials for functioning yet these credentials develop potential system breakdowns if they become invalid or expire. Scheduled tasks that run unsuccessfully after authentication tokens become invalid could lead to repeated login failures, which activate security protection systems. The automated processes designed to enhance efficiency generate severe system interruptions due to their automated nature.
4. Mobile Devices
The constant movement of mobile computing systems that rely on unreliable networks and extensive user account management sets the conditions for frequent account lockouts. Back-end authentication protocols among various platforms create plan inefficiencies because they use incompatible authentication schemes, and automatic password attempts lead to security shutdowns. Multiple email and application accounts, along with the portable network environment between cellular and Wi-Fi, cause additional hurdles in authentication management.
5. Terminal Service Sessions
Remote access methods generate specific circumstances that allow multiple users to log in simultaneously, thus straining conventional password authentication structures. Security issues emerge from disconnected sessions, which hold authentication tokens that oppose current security measures, and from network delay, which results in multiple authentication attempts that trigger protective lockout functions. Desktop systems struggle to process contemporary authentication protocols effectively, thus making the authentication system more complicated.
6. User Errors
Users, quite simply, cause the majority of account lockout issues through human error. Users face authentication problems because they make common mistakes, including unintentional wrong password entries and typing blunders under stress, or they forget their updated passwords. Repeated entry of wrong credentials due to muscle memory of old credentials and hard password requirements results in increased authentication errors. Users who need to memorize complex password combinations for numerous platforms face an ideal situation for unintentionally violating their system security.
7. Password Policy Issues
Stringent password security measures, which aim to protect the system, create challenges for users in authenticating their accounts as well as increasing the potential for locked-out accounts. Active and stringent password policies containing complex rules and continuous change requirements represent a security problem that exceeds their security benefits. Policy inconsistencies between different system platforms create trouble when users attempt to achieve seamless access across networks. Poor password reset systems transform security operations into large-scale problems instead of simple password maintenance procedures.
8. Misconfigured Policies
Multiple security policies that have been incorrectly configured will lead to authentication issues created by inconsistent and overly complicated security rules that span across different systems. The misalignment of security policies leads to unexpected account lockouts, which produce major disruptions for user access and organizational work productivity. The challenge of keeping security configurations identical poses a major problem for organizations that operate across various distributed IT environments with multiple departments.
9. Brute-Force Attacks
Authentication systems can sometimes become overwhelmed through brute-force attacks, as attackers try and breach credentials with trial and error on a large scale. Attackers use malicious tactics to activate security lockouts, which lead to massive service disruptions that create enormous trouble for IT security teams. Attackers deploy advanced technological resources together with distributed systems to execute complex brute force attacks.
How to Troubleshoot AD Account Lockout Issues
1. Review Event Logs
The forensic record needed to investigate account lockout incidents exists in event logs. Through Windows Event Viewer users can obtain complete details about authentication failures that include information about the time and location of account lockout incidents with their root causes. Security professionals inspect security and system logs to detect authentication failure patterns and determine exact lockout times without losing the necessary diagnostic information that explains restricted account access events.
2. Check for Cached Credentials
Credentials that get stored in computer memory lead to extended authentication difficulties among multiple devices and applications. When login credentials remain stored on devices, they can lose their validity or abandon security requirements, which results in security dangers. People who handle cached credential stores need to check their status to maintain up-to-date configurations that match organizational authentication standards. Removing old credentials from cache storage frequently eliminates problems that prevent users from accessing their accounts.
3. Investigate Service Accounts
Service accounts serve as a sophisticated system for user authentication, which exists in most enterprise settings. Business operations and system-level tasks run through specialized accounts which make them vulnerable to authentication challenges. Administrators need to investigate service account setups while ensuring password security along with inspecting expiration dates of credentials and establishing the right access points for these accounts on all necessary systems and applications.
4. Examine Scheduled Tasks
While performing their scheduled tasks these controls can activate an account lockout by making too many authentication attempts. Automated system-level operations use specific user credentials, but such processes become ineffective when those credentials lose their validity. An investigation into scheduled tasks, along with their authentication protocols and possible execution conflicts, will help identify the root causes behind account lockouts.
5. Check Mobile Devices
Devices that connect to mobile networks contribute substantial levels of complexity in authentication management because users experience intermittent network connections along with multiple device synchronizations. Security lockouts occur due to different platforms, together with intermittent network connections and background synchronization processes, which trigger unexpected authentication attempts. Organizations should evaluate mobile device connection activity, together with synchronization methods and authentication protocols, to discover authentication breakdown.
6. Verify Terminal Server Sessions
The authentication process of terminal server sessions contains various points of failure due to its distinct authentication conditions. Broken sessions, along with sessions that do not close properly continue to store authentication tokens that create security policy conflicts. The authentication process of terminal servers becomes difficult to manage when encountering problems with network speed, as well as when users try to log in at the same time, or when older systems restrict authentication methods. Account lockouts will occur due to improper workflow when active sessions remain unchecked together with inadequate logout methods and insufficient session management systems.
7. Review Password Policies
Security requirements continuously interact with user accessibility at the critical point of password policies. Varied and too complex password requirements from organizations create problems that hinder proper authentication procedures. System administrators need to thoroughly check current password rules because they should combine security objectives with the functional comfort of users. Managers should evaluate password rules that involve complexity standards, along with expiration periods and maximum lockout limits, and all platform compatibility considerations.
8. Use PowerShell for Diagnostics
Using PowerShell, administrators can access robust tools that help them investigate account lockout problems. Through specific cmdlets advanced administrators can collect thorough information about user accounts combined with authentication attempts as well as system-level security configurations. Through PowerShell scripting, users can automate diagnostic operations to collect data while analyzing authentication logs to find probable reasons behind account accessibility issues.
9. Enable Advanced Auditing
Comprehensive auditing provides the foundation for understanding and preventing account lockout incidents. By enabling advanced auditing features, organizations can capture detailed information about authentication attempts, system access, and potential security events. This proactive approach allows for real-time monitoring, detailed forensic analysis, and continuous improvement of authentication security mechanisms.
Troubleshoot Account Lockouts with Lepide Free Tool
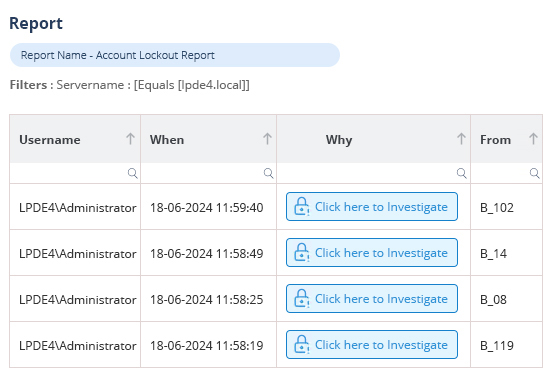
If you’re experiencing a high number of account lockouts in a secure environment it would indicate an imbalance between security and convenience. Every organization needs to determine an appropriate compromise between security and convenience. To do this, they will need to consider the sensitivity of the information in their settings, the risks they can bear, and their users’ interests.
The Lepide Account Lockout Examiner Free Tool simplifies the task of understanding and resolving account lockouts by providing real-time detection of account lockouts. It scans endpoints for multiple factors that could be causing lockout issues, such as mapped drives using old credentials, systems using old cached credentials, applications using old credentials, windows services using expired credentials, etc.
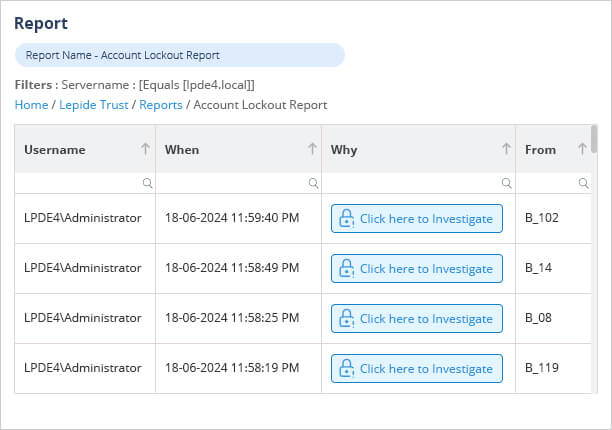
As you can see in the above screenshot, our tool can quickly generate the report of all locked accounts, you can investigate the reason for the lockout of each account individually and resolve it. To see how it works, download the Lepide Account Lockout Examiner Free Tool now.