Last Updated on December 16, 2024 by Deepanshu Sharma

Currently, different organizations are gathering massive amounts of data on a daily basis in the wake of big data. Regardless if it is for individual customers or for a business, data provides the decision, operations, and drive for business. However, more data volume means more data-related threats and risks. Losing sensitive information, unauthorized access, and compliance violations are not something that can be lightly brushed off. This is where data risk assessment steps set in. But before we get carried away, let us understand what data risk assessment is all about.
What is Data Risk Assessment?
Data risk assessment is a structured approach that seeks to analyze an organization’s data environment in order to identify, analyze, and manage the risks that may be associated with data processing, storage, and sharing. It has to be an ongoing process that goes beyond just running data risk assessment or doing it now and then only when there appears to be a problem. It usually involves a series of assessments of the organization’s outside and inside environment to identify potential threats to data security and privacy, and then implement measures to address these threats.
In simple terms, data risk assessment focuses on “Things that can go wrong with an organization’s data and how to avoid them” Hence, by learning of the possible risks, organizations can ensure that their information is safe and avoid such mishaps.
Why Data Risk Assessment is Important
Data risk assessment plays a highly significant role and must be pointed out. Today there are lots of laws and regulations in the world such as GDPR, CCPA, and HIPAA that require many measures of data protection. If assessment and management of data risks are not done effectively it will result in severe penalties, compromise on reputation, and trust from the consumers will be lost. Apart from compliance advantages, data risk assessment has several more important advantages.
Protection Against Data Breaches: Security breaches are expensive and as a result can lead to a loss of reputation. Data risks should therefore be evaluated because they enable firms to identify weaknesses and strengthen their protection.
Improved Decision-Making: Data risk assessment is important as it gives an organization an indication of its state of readiness when it comes to data security. Such information enables leaders to decide on where best to invest by improving data protection.
Enhanced Customer Trust: There is a growing concern when it comes to customer privacy, and they also have higher anticipated expectations of organizations to protect their identities. Risk assessment of the data can lead to the generation of a lot of trust because it shows that a lot of importance is placed on the data set.
Compliance and Avoidance of Penalties: As the regulations are gradually tightening, companies must abide by set laws to avert expensive fines. Particularly, a structured data risk assessment prevents an organization from not meeting its legal requirements.
Risk Mitigation: Data risk assessment helps prevent problems from becoming actual concerns and outlines the process of risk management.
Benefits of Data Risk Assessment
Data risk assessment provides several tactical advantages, which may not seem obvious but would be crucial in the long run.
Enhanced Security Posture: Data risk evaluations develop the security structure of your organization when done faithfully. It helps you be aware of the areas you are weak at and prevent such areas from being exploited thus strengthening your security measures.
Informed Resource Allocation: As with any data risks, not all are the same. Some of them have significant implications for people’s lives, while others present a relatively low risk and can be easily avoided. Comparing the risk exposure and risk impact allows allocating resources in a more effective way to pay attention to the most dangerous threats.
Reduced Financial Losses: Without proper intervention, the data breaches could result in huge costs through fines, legal action, and revenue drops thanks to customer loss. To avoid such expensive effects, risk identification and management must be executed as soon as possible.
Better Incident Response: When an organization has an understanding of the data risk threats that are around them, it can combat such a situation much more easily and effectively. This readiness always helps to reduce the time losses, minimize the losses, and get back to normal productivity much faster.
Competitive Advantage: Businesses that pay attention to information security issues and risk management usually have a competitive advantage. A company can successfully mitigate customer information and adhere to regulations in order to improve customer trust in brands.
Components of Data Risk Assessment
An effective data risk assessment therefore comprises of the following components, each of which is aimed at achieving a specific goal relating to data security.
Data Inventory and Classification: The first piece in data risk assessment is identifying the type of data you have and classifying it according to its sensitivity. This aids in determining which data need more protection.
Risk Identification: This includes performing an analysis of all possible threats to your data within its entire life cycle, including interceptions, data leakage, and disasters. This sometimes necessitates an understanding of the risks that are involved in a certain procedure in order to be in a position to counter them effectively.
Conducting Vulnerability Assessment: This component defines certain vulnerabilities in the systems that may be implemented for its use. Common methods of vulnerability assessments include penetration testing and software audits of open Internet sites.
Implementing Necessary Controls: After threats are addressed in a risk assessment, the next step would be to apply measures that will minimize the effects of such threats. All of these controls can be as technical as firewalls and encryption programs or as manual as conducting employee awareness programs and controlling who has access to what information.
Monitoring Possible Risks: Data risk assessment is not a check in the box what needs to be understood about data risk assessment. It is effective in the sense that it checks for new emerging risks as well as makes sure all the implemented controls are still efficient all the time.
How to Perform Data Risk Assessment
A data risk assessment may be carried out systematically and this will make it possible to check on all the possible angles of data risk. Here’s a step-by-step guide:
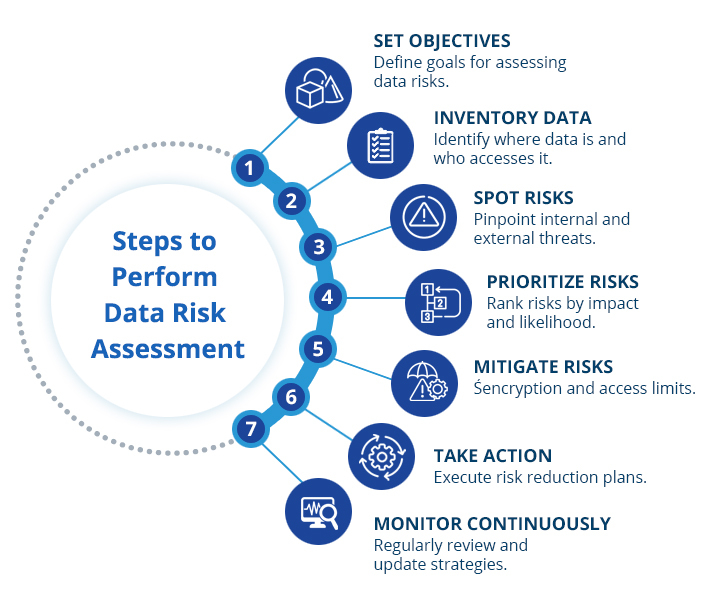
- Define Scope and Objectives: To be more specific, it is recommended to begin with the definition of the goals you are going to achieve. Are you dealing with a new system in the organization, or a new type of data in the organization? Clear objectives will be set therefore it will help to determine the primary agenda of the process.
- Allocate Data: Determine where data is located in your organization, how it is being used, and who can access that data. This involves data in all forms within all the devices, databases, and cloud structures.
- Analyze Potential Risks: Consider the likelihood and the severity of every found risk. Having learned the risks associated with online activities, this analysis will enable you to focus on the risks that can be dangerous to data.
- Develop Risk Mitigation Strategies: For every high risk on the high-risk list, it is necessary to come up with measures that can help in reducing the risk. These could be things like entering access rights, use of encryption, or training of the employees.
- Implement Controls: Activate your contingency plans. This is the phase where all the planning in terms of what activities should be done, what strategy to use, and when, as well as who should do what turns into action.
- Regular Review and Monitoring: Risk assessment should not be a one-time event. The strategies have to be reviewed and updated more often so that new threats and changes in the organization’s data environment are met head-on.
- Document Everything: Documentation is important to monitor and evaluate progress, and where necessary prepare reports that have to do with compliance. It also forms a reference for future evaluations.
- Automate Where Possible: Take advantage of automatic discovery, categorization or even monitoring tools. Automation makes things faster and even the mistakes are minimized.
How Lepide Helps
Lepide Data Security Platform offers a set of solutions for conducting thorough data risk assessments, providing tools to monitor, manage, and safeguard sensitive data. The data discovery and classification capabilities help organizations identify and prioritize high-risk data, while real-time monitoring and automated alerts allow for quick detection and response to unauthorized access or suspicious activity. Additionally, Lepide user behavior analytics proactively identifies potential insider threats, and its compliance management tools ensure organizations meet regulatory requirements, such as GDPR and HIPAA.
With these features, Lepide empowers organizations to strengthen their data security efforts, streamline compliance, and create a secure environment that protects sensitive information from emerging threats.
Conclusion
Considering that data has become one of the significant organizational resources, the presence of the data risk assessment strategy is crucial. It is the best way to avoid the high costs of data breaches, meet legal requirements and ultimately gain the trust of consumers. When implemented and managed properly along with the use of appropriate tools, for instance, data risk assessment should become a crucial and dependable security ingredient.
It can therefore be clearly stated that attending to data risks is no longer a luxury but a necessity when doing business. For a company of any size ranging from a small business to a large enterprise, data risk assessment allows for the necessary insight and control over the current data exposures that are possible in the modern digitally enhanced environment.
If you want to know more about how Lepide can help, check out Lepide Free Data Risk Assessment today.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
