
What is Database Security?
Database security refers to the tools, technologies, and processes involved in protecting databases from internal and external security threats. However, it also applies to the data itself, which may find itself in various unsanctioned locations, making it hard to secure. Database security also involves protecting the database management system, and the various apps that connect to it.
Common Threats to Database Security
In reality, any kind of vulnerability, whether a software vulnerability or human error, will pose a threat to your database. However, since a complete guide to data security is beyond the scope of this article, below are some of the most common database security threats organizations should watch out for.
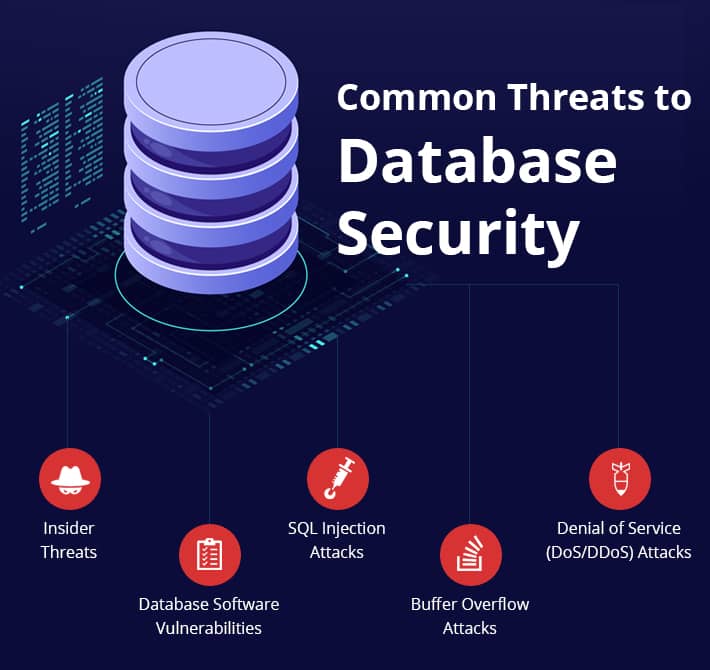
1. Insider Threats
Insider threats are not typically motivated by malice but are generally caused by negligence. Employees have a tendency to accidentally expose, corrupt, or delete sensitive data. To make matters worse, employees are frequently granted too much access to sensitive data, and they often use weak passwords, as well as re-use and share passwords, which attackers can exploit.
2. Database Software Vulnerabilities
Database management software, as with other types of software, will contain bugs that attackers will try to exploit. Database management software vendors frequently issue security patches, which need to be installed as soon as they become available in order to keep your data secure.
3. SQL Injection Attacks
SQL injection attacks are when an attacker is able to extract data from a database by inserting malicious SQL code into query strings that are used to query the data. They are usually caused by improper validation of web form fields, in addition to poor server-side coding practices. Organizations must carry out regular vulnerability testing on their database and applications.
4. Buffer Overflow Attacks
A buffer overflow attack is where a program overruns a buffer’s boundary and overwrites adjacent memory locations. Buffers are frequently used by operating systems, including database applications, to hold data, sometimes executable code. Attackers can overwrite these buffers with malicious code, which can help them elevate their privileges in order to gain full access to the computer’s resources.
5. Denial of Service (DoS/DDoS) Attacks
A denial of service (DoS) attack is where the attackers overwhelm a target with traffic in an attempt to make it unavailable. DoS attacks usually target servers, although they are also sometimes used to target databases. Distributed Denial of Service (DDoS) attacks are even harder to defend against as they use a botnet (a distributed network of compromised devices) to launch the attack.
Database Security Best Practices
A database cannot be considered secure unless it is in a secure environment, has its own security, and is accessible by secure individuals. These are some recommended best practices for safeguarding databases and associated data.
1. Test your Database Security
A test against an actual attack ought to be conducted when the database infrastructure is established. For this, you can isolate any vulnerabilities that were being missed by putting yourself in the shoes of a cybercriminal by conducting audits or penetration tests on your own database. Security testing must include ethical hackers or certified penetration testers. Penetration testing, which is regarded as a crucial test that guarantees prompt investigation and treatment of these vulnerabilities, assists in producing comprehensive reports that detail all database flaws.
2. Use Database and Web Application Firewall
The first layer of defense comes from database-specific firewalls that deny access by default. A firewall must be used to protect the database server from database security threats. This needs to be stopped from starting outbound connections unless there is a specific reason for doing so. While safeguarding the database with a firewall, one must deploy a web application firewall (WAF). The reason behind this is attacks aimed at web applications can be used to gain unauthorized access to the database.
3. Manage and Secure Separate Database Servers
To enhance security by preserving isolation and avoiding lateral movement, keep your web server and database server apart. Even if an attacker manages to compromise your web server admin account, they will still be unable to access the database because the servers are different. Your database server and any non-essential servers or applications should be kept apart. For certain functions, these servers may need to communicate, but database operation does not require them. Make sure you restrict the permissions when you enable communication to the bare minimum needed for processes to succeed. The least privilege concept helps in limiting the potential harm that an attacker could do to your database.
4. Secure Database User Accounts
For smaller businesses, comprehensive access control may not be feasible; however, it is still crucial to manage permissions through roles or groups rather than giving them to specific individuals directly. If your company is greater in size, you might want to use an automated access management system. Because temporary passwords with restricted access can be generated by access management software, authorized users must authenticate each time they browse the database. By using this method, all sessions and actions are correctly tracked and password sharing is avoided. Limit the amount of users who can access the database. Limit access to the times when your users need it and only grant the administrative rights necessary to finish a task. Protect user accounts by following these common practices – Create a strong password policy and follow it, hash tags for passwords that are encrypted and saved, turn on automatic account locking after many unsuccessful tries to log in, have a procedure in place for deactivating accounts when workers change positions or depart the organization.
5. Real-Time Monitoring
Observe every login attempt and login to your operating system and database. Examine the logs frequently in order to spot unusual behavior. An alerting system could be put in place to inform teams or pertinent persons about questionable activities. In the event that an employee completes an activity that seems suspicious or careless, or if an attacker compromises your databases, continuous monitoring enables you to promptly detect compromised accounts. Monitoring also assists you in spotting instances where users share accounts or when unauthorized accounts are created—that is when a hacker makes an account without your consent. To provide independent monitoring and assist in tracking administrative activity, a database activity monitoring (DAM) solution is used. To provide records for investigative purposes, maintain database activity logs, and carry out routine audits.
6. Audit Sensitive Data
Certain rules and compliance guidelines have particular data discovery needs, particularly in sectors like telecom, financial services, and healthcare. Ensure that you adhere to the compliance rules that apply to both general and specific database workloads in your organization. Sensitive and non-sensitive information can be found in many databases. If this is the case, you should regularly audit your data to determine which database tables or columns need extra protection since they are sensitive. Without knowing where sensitive data is stored, it is impossible to protect it effectively, which can lead to data breaches and noncompliance with regulations.
7. Strong Authentication
It is imperative that all databases have strong authentication enabled since they are nearly always mission-critical systems. Use two-factor authentication if you can, for instance, by pairing a password or PIN with a personal item the user owns, such as a security token or cell phone. Database authentication involves verifying that service accounts or users trying to access the database are who they claim to be. Another related step is authorization, which establishes what database permissions the account should have depending on the verified identification.
8. Follow 3-2-1 Backup Rule
System and data backups guard against malicious behavior or total system failure. Regular backups that are well-protected are essential. The 3-2-1 backup rule is followed by best practices, which include having three backup copies, two different kinds of storage, and at least one offline and offshore copy. Backups should be encrypted and kept apart from encryption keys; they should also be completely inaccessible to the general public. To facilitate quick system recovery, backups should contain not just data but also the configurations, software programs, and settings of the underlying infrastructure. Mission-critical infrastructure backups should be checked often to confirm the efficacy of the backup procedures and to establish standards for recovery expectations.
If you’d like to see how the Lepide Data Security Platform can help secure your databases, schedule a demo with one of our engineers.
FAQs
How can I identify and assess the specific security risks to my organization’s databases?
Identifying and assessing your organization’s database security risks involves a multi-pronged approach:
- Vulnerability assessment: Run automated scans and manual tests to pinpoint weaknesses like unpatched software, outdated configurations, and weak passwords. Look for common vulnerabilities like SQL injection and buffer overflows.
- Penetration testing: Simulate an attack by ethical hackers to discover exploitable weaknesses that automated scans might miss. This helps validate your defenses and expose blind spots.
- Access control review: Analyze user access privileges to ensure only authorized personnel have access to specific databases and data within them. Review the “principle of least privilege” and implement it strictly.
- Audit and monitoring: Enable database auditing features to track user activity and identify suspicious behavior. Implement real-time monitoring systems to detect and respond to potential threats promptly.
- Employee training: Educate your employees on cybersecurity best practices, including phishing awareness, password hygiene, and reporting suspicious activity. This reduces the risk of human error and social engineering attacks.
What are the costs and benefits of implementing different database security measures?
Implementing database security requires careful balancing of costs and benefits. While initial investments exist in tools, training, and specialists, long-term benefits outweigh them for most organizations. Initially, integrating security might impact workflows and resource allocation, demanding time and effort. Maintaining robust security adds complexity, requiring ongoing management.
However, the benefits are substantial. Strong security significantly reduces the risk of data breaches, which can be financially devastating due to penalties, legal fees, and reputational damage. It also ensures compliance with industry regulations, avoiding legal consequences. Protecting customer data builds trust and loyalty, improving brand reputation and potentially boosting business. Additionally, while adding initial complexity, security can ultimately enhance operational efficiency by minimizing disruptions and streamlining data management.
Finding the right balance involves analyzing your organization’s risk profile, data sensitivity, and budget to determine cost-effective solutions. Free or open-source options exist, and security measures can be scaled based on your needs. Remember, neglecting data security is far more costly than the initial investment. By understanding both costs and benefits, you can make informed decisions to protect your valuable data.
How can I stay up-to-date on the latest database security threats and best practices?
Staying abreast of the ever-changing landscape of database security threats and best practices requires a multi-pronged approach.
Firstly, actively seek reliable information sources. Subscribe to reputable cybersecurity publications or follow security vendors’ blogs for insights on emerging threats and best practices. Additionally, national cybersecurity agencies often publish valuable alerts and advisories on critical vulnerabilities and ongoing threats.
Secondly, participate in online communities. Engaging in online forums and following security professionals on social media allows you to connect with others, share experiences, and gain valuable insights from ongoing discussions about emerging threats and solutions.
Thirdly, consider attending industry events and conferences. These events provide opportunities to learn from experts, network with professionals, and gain valuable knowledge about the latest security trends and best practices. Additionally, many organizations offer webinars and online training sessions focused on database security, keeping you updated on the latest threats and mitigation strategies.
Fourthly, stay vigilant by continually monitoring and testing. Regularly scan your databases for vulnerabilities using available tools and services. Additionally, consider periodic penetration testing to identify exploitable weaknesses in your defenses by simulating real-world attacks.
Finally, staying informed about regulations is crucial, especially if your organization operates in a regulated industry. Understanding relevant data security regulations ensures you implement appropriate security measures to comply and avoid legal consequences.
By actively engaging with these resources and practices, you can build a comprehensive understanding of evolving database security threats and stay informed about the best practices to safeguard your organization’s valuable data.



