Last Updated on December 17, 2024 by Deepanshu Sharma

What is Kerberos?
Kerberos is an authentication protocol which is used to verify the identity of a host across an untrusted network, such as the internet. Kerberos support is built into all major computer operating systems, including Microsoft Windows.
Since Windows 2000, the Kerberos protocol has been used by Microsoft as the default authentication method, and it is a fundamental part of the Windows Active Directory (AD) service.
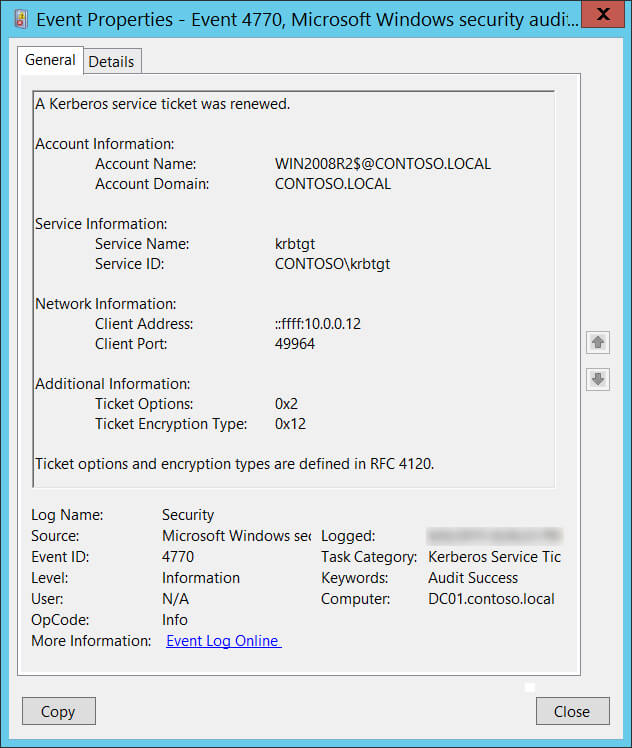
| Event ID | 4770 |
| Category | Account Logon |
| Sub category | Kerberos Service Ticket Operations |
| Description | A Kerberos service ticket was renewed |
Download Whitepaper

This event is logged when a Kerberos service ticket was renewed. Kerberos limits how long a ticket is valid. If a ticket expires when the user is still logged on, Windows automatically contacts the domain controller to renew the ticket which triggers this event.
Why Does Event ID 4770 Need to be Monitored?
Below are the reasons why you might see references to it:
- Detection of privilege abuse
- Discovering potential malicious activity
- Additional purposes for example getting information on user activity such as user attendance, peak logon times and so on
- Compliance regulations
Conclusion
Visibility over what is happening on their Active Directory is essential for an administrator. This ensures that any suspicious activity relating to potential security threats is identified and responded to immediately.
The Lepide Active Directory Auditing Tool enables effective monitoring, auditing, and reporting on all Active Directory states and changes including account logon events. The Lepide Solution includes pre-configured account logon reports to help identify malicious users attempting to logon to machines that require elevated privileges.
Related Blogs:
- Account Lockout Event ID 4740
- Event ID 4774 – An Account was Mapped for Logon
- Event ID 4773 – A Kerberos Service Ticket Request Failed
- Event ID 4769 – A Kerberos Service Ticket was Requested
- Event ID 4624 – For Successful Logons
- Event ID 4768 – For Kerberos Authentication
- Event ID 4660 – An Object Was Deleted
- How to View and Export Windows Event Logs

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
