Managing an enterprise IT environment involves managing hundreds or thousands of devices spread throughout multiple locations. Without centralized enforcement of security policies, configuration of system settings, and permissions management organizations face security uncertainties and operational inefficiencies.
Group Policy is the main management and control mechanism behind Active Directory. System administrators use it to create rules which determine the network behavior of users and computers whilst upholding security standards and standardization throughout connected systems.
This blog explores the basics of Group Policy and goes over essential features, categories and uses that allow organizations to implement it successfully for security protection and operational efficiency.
What is Group Policy in Active Directory?
Group Policy serves as the central point of Windows network administration through which IT can manage standardized policies across multiple computers and users simultaneously. Administrators establish policy templates which distribute standardized computer configurations across digital environments. The automated deployment system powered by this capability eliminates thousands of manual configuration tasks by implementing standardized security requirements for minimal human involvement.
Group Policy implements its technical framework as a hierarchy that reflects organizational arrangements with policies distributing from domain control to target Organizational Units (OUs). User machines access the Windows operating system through Active Directory to obtain a list of relevant policies that match both the user identity and machine hardware after which system configurations are handled automatically. Group Policy governs the entire system range from minor visual aspects to fundamental security parameters along with password policies and software control functions and network resource permissions and application execution settings.
Organizations achieve two primary benefits from Group Policy: it establishes both elevated security defenses and improved operational performance. Security teams depend on Group Policy to execute regulations and internal protection standards, thus providing standardized endpoint defense. Solution administrators use automated processes from Group Policy to implement software deployments and system service setups and user interface control without interrupting workflow operation. By using centralized management administrators can decrease operational costs while achieving better endpoint stability through predictable configuration and easier system debugging as workers maintain consistent digital experiences across their devices.
Types of Group Policies
Below are the types of Group Policies.
Local Group Policy
Local Group Policy works as an independent configuration tool which functions at each computer level without needing Active Directory infrastructure. Such configurations exist directly on the machine thus they function well for standalone computers and domains without central administration. Each machine equips administrators with the Local Group Policy Editor (gpedit.msc) for accessing and modifying these settings individually.
The standalone configuration tool provides significant value during configuration tests before network-wide implementation and computer management for machines not connected to domains. The lack of financial resources for Active Directory implementation leads small businesses to use Local Group Policy as their main tool for basic security enforcement. Local Group Policies create an important foundation for system management that remains relevant to large organizations although their scalability is restricted since domain policies cannot always be implemented.
Domain Group Policy
A Windows network domain depends on Domain Group Policy as its core management system to control all domain-integrated machines. Active Directory distributes management policies which store and propagate updates to all computers and users who are members of domain networks. Through this centralized management all potential thousands of devices receive identical configurations automatically without needing support from human operators for each device.
The basic computing standards for an organization get set through Domain-level policies which apply to every computer and user. Such policies handle universal implementation of basic security settings and operational configurations and system restrictions. Through the Group Policy Management Console administrators establish domain-level policies which they create or modify and then bind to their designated domains.
Domain Group Policy delivers its power through its inheritance mechanism which enables settings to move down the Active Directory structure in a way that establishes organizational standards while allowing department-level customization options.
Organizational Unit (OU) Group Policy
The Organizational Unit (OU) Group Policies enable administrators to achieve detailed control of individual departments or operational functions in an organization. Administrators can make specific customized settings that match different user or machine requirements when they apply policies to organizational units at the OU level. Different teams can receive tailored configurations through this approach which preserves the integrity of the entire domain environment.
OU policies maintain both overall domain administration control and individual department autonomy very well. Organization units assign marketing teams the freedom to use creative programs and social media services and issue financial departments secure security rules. OU structures use hierarchical policies that permit inheritance from superior OUs until individual modifications occur at lower levels. Enterprises prefer Group Policy within Organizational Units because its detailed settings complement their organizational structures while no other policy type offers this level of alignment.
Site Group Policy
Site Group Policy directs its settings to Active Directory sites that serve as collections of IP subnets which mirror organizational physical locations. Organization-wide policies help manage location-specific configuration through specific Active Directory sites which target particular parts of the domain network. Site Group Policy enables administrators to modify replication parameters and network bandwidth settings together with multiple configuration options that depend on the network infrastructure.
The Site policy provides essential functionality for global businesses which require maximum connection optimization between networks of different capabilities. The company can modify replication timetable settings through Site Group Policy so headquarters operates independently from remote offices which use different bandwidth capabilities at different times.
Site Group Policies recognize the physical characteristics of network infrastructure to create a bridge connecting logical Active Directory structure with physical network topology which preserves organizational standards and local appropriate configurations.
Security Group Policy
Security Group Policies deliver specialized security standards for system and network maintenance throughout an organization. The specialized policies established under Security Group Policies mandate password restrictions and authentication protocols together with account lockout parameters to safeguard organizational resources against external attacks as well as internal mishandling. The technical security posture of any organization relies on security group policies which convert security needs into operational technical enforcement mechanisms.
Advanced Group Policy Management (AGPM)
Advanced Group Policy Management operates as a complex management platform to implement version control with change tracking features and approval workflows for Group Policy management. Through AGPM, administrators create a managed system which requires policy modifications to undergo checkout editing review approval processes before becoming operational in a pattern similar to current software development methods. The systematic design structure blocks unintentional modifications from unauthorized users which would target numerous thousands of system users.
AGPM enables administrators to trace down policy-induced issues through its track records which prove vital for problem resolution. Administrators obtain immediate access to understand all changes in policy including dates and users who performed them so they can restore previous versions if needed. AGPM facilitates testing and deployment of policies through offline work which minimizes potential risks to production environment policies. The Active Group Policy Management platform acts as an organizational framework instead of functioning as a policy type and it drives organizations to enhance management of their policy infrastructure across complex environments.
What are Group Policy Preferences?
Group Policy Preferences enhance Group Policy functionality by providing adjustable configuration abilities that recommend settings instead of enforcing strict rules. Preferences function differently than restrictive standard policies because they enable conditional configuration rules which users may tweak if required. Group Policy Preferences enable administrative assignments that match many tasks which previously needed scripting or manual interventions.
The preferences system provides administrators tools for effortless setup and management of mapped drives along with printers and shortcuts and registry settings. Applications which use targeting capabilities make preferences powerful because administrators can specify settings by computer name or IP address or through time-based conditions. The conditional application method allows organizations to deal with unique situations by bypassing standard rules without constructing brand new policies. The evolution of policy management allows Group Policy Preferences to apply settings through an intelligent system based on specific needs and contexts rather than strict enforcement rules.
What is a Group Policy Object (GPO)?
The Group Policy Object (GPO) functions as an organized assortment of settings that establishes rules for Active Directory user and computer behaviors. GPOs include specific configurations which enforce organizational standards by guiding security policies along with desktop environments for every system.
Computer Configuration: Any changes on Computer Configuration inside a GPO directly affect all machines apart from who uses them. Security elements as well as network protocols together with system patches make up these settings. Organizations use Computer Configuration to implement security rules and encrypt policies along with VPN configurations which ensure all devices follow established security standards.
User Configuration: User Configuration settings become active only during the time a particular user authenticates to the system. User Access Controls together with Desktop Restrictions and Application Permissions constitute the scope of definitions implemented through these settings. Administrators who manage IT systems use User Configuration to enforce control over Control Panel access as well as set password requirements and run login scripts. Organizations achieve data protection together with unauthorized activity control through policy implementations.
Group Policy Object (GPO) Examples
Below are the examples of Group Policy Objects (GPO):
- Security Policies: Group Policy utilizes security policies which stand as its most crucial implementation. Organizations apply their security settings through GPOs that force users to follow password expiration requirements together with multi-factor authentication and account lockout parameters. Through Group Policy administrators define security protection measures which help prevent illegal access to systems and stop unwanted security breaches.
- System and Software Management: Through Group Policy IT teams can successfully deploy software packages and conduct system update management tasks efficiently. Through Group Policy Objects (GPOs) organizations can manage their Windows updates automatically as well as deploy enterprise software applications and block unapproved software installation. The updated system management helps decrease administrator work while guaranteeing security for every system.
- User Experience Control: Through GPOs organizations can control user interface settings by designing desktop parameters and Start Menu personalization as well as taskbar modification. Through policy implementation administrators enforce restrictions on system features and they can conceal specific storage units and they block users from accessing command prompt. The implementation of these security measures produces both security maintenance and a steady user experience across all interfaces.
Uses of Group Policy in Active Directory Environments
1. Security Policy Enforcement
Group Policy functions as the security prevention layer for organizations by deploying uniform security standards across their managed systems. Network administrators should use password rules which determine length requirements and complexity measures and session expiration limits to prevent weak passwords from threatening system security. Group Policy establishes multiple security practices which include password requirements along with account lockout thresholds and user access permissions while simultaneously obstructing dangerous system actions such as software installations and registry modifications
Through one integrated location administrators can set up Windows Defender configurations and manage firewall rules together with USB device control policies. Security policies transform into technical controls which the organizational users cannot bypass through this single coordinated management system. Businesses with compliance obligations including HIPAA, PCI-DSS and SOC2 achieve complete auditable technical security implementations through the translation of their written policies by Group Policy tools.
2. Standardized Desktop Environment
Group Policy enables organizations to deliver a consistent user experience which stands out as its most notable benefit. Group Policy enables IT departments to establish organization-wide standards pertaining to desktop wallpapers, screen savers, and Start menu configurations and taskbar settings. Standardization through Group Policy provides users with a single operational experience which streamlines training and establishes a professional business identity for every workstation.
Group Policy standards shape how users view their desktops by specifying visible icons and pinned applications and the methods users employ to navigate the Windows interface. The access to security-sensitive areas like Registry Editor and Control Panel should be disabled by organizations to minimize confusion and ensure system safety. Employees who transition between workstations encounter familiar interface arrangements no matter their office location thus they maximize productivity and experience fewer support calls regarding navigation systems
3. Automated Software Deployment
The installation process which requires technicians or users to visit each computer becomes a waste of time because it creates inconsistent software environments which affects productivity. Group Policy achieves this process through its capability to perform simultaneous application deployment across large numbers of computers which enables necessary software to reach the appropriate users at specific times.
Group Policy provides administrators with the power to control software installation through role-based or department-based limits and organization-wide requirements. Group Policy allows administrators to deploy applications automatically in the background and also provides restricted scheduling options and Software Center access for user-directed installations. The IT staff benefits from automatic updates and removals of applications which helps maintain system security and prevent unauthorized programs from remaining in place.
4. Windows Update Management
Unsecured systems function as the primary security threat for corporate networks despite being difficult to manage on a widespread scale. Through Group Policy, organizations create uniformities in software updates because it enables management of Windows Update throughout their entire managed PC infrastructure. Through Group Policy administrators can set up automatic update deployment as well as plan downtime during non-business hours and block users from delaying essential security fixes.
Administrators can determine update types (security, features, and drivers) that should be applied to systems while defining active maintenance sessions that match operational schedules. The deployment process divides into stages according to departmental needs so IT staff can verify updates on lower priority systems before rolling out to all systems. Through their well-planned method organizations maintain business operational continuity by safeguarding systems while avoiding system interruptions that occur during important working hours.
5. Network Resource Access
Users gain better productivity while support becomes easier to manage through automated network resource connectivity. Group Policy establishes automatic network drive mapping which gives users departmental shared folders and storage spaces and collaborative project directories for seamless access without IT help. Group policy allows administrators to create user-specific connection mappings because finance staff members immediately receive system financial access yet the marketing department gets media file access.
Group Policy ensures printer management through automatic printer installation and default-printer assignment based on user location as well as department affiliation. The physical network connection determines printer assignments for users traveling between offices so their documents print to close by devices instead of distant facilities. The system allocates resources intelligently to connect users with FTP sites and intranet portals and application servers so they can access everything regardless of the workstation they use.
6. Data Protection Through Folder Redirection
The distribution of organizational data across multiple workstations creates dangerous exposure risks because appropriate backup procedures might never run. Group Policy combats this vulnerability through folder redirection that automatically moves user profile containers including Documents, Desktop and Pictures to network storage points. The user interface remains the same but users access documents that exist on maintained servers that run scheduled backup protocols.
The redirection strategy of information storage improves data security while delivering numerous advantages to the organization. Workstation changes do not affect user file access because the system maintains a transparent connection to their files and folders. The management of corporate data through centralized control within IT departments results in easier compliance measures and standardized storage capabilities. The replacement of failed hardware systems becomes more efficient because replacement computers can instantly access the same redirected folders during hardware failures thus minimizing business disruptions and data loss.
7. Remote Desktop Services Optimization
Remote Desktop Services (RDS) delivery platforms rely on Group Policy to optimize both application delivery and desktop delivery sessions for high performance and security as well as improved user experience. Group Policy mechanisms enable administrators to control session durations and resources along with printer redirection while maintaining a good user experience through clipboard support in these remote-hosted environments.
Group Policy facilitates application compatibility and enhances session performance in RDS environments. The configuration of connection quality parameters along with bandwidth allocation and display settings enabled by administrators ensures that users get the same experience regardless of their devices or network conditions. The security controls applied only to remote sessions include file download limitations and resource access restrictions which protect data from theft without reducing productivity. Organizations deploying load balancing policies enable users to connect efficiently with correct session hosts which reduces overall performance bottlenecks affecting department operations.
8. Compliance Auditing and Reporting
Modern regulatory requirements force organizations to prove their policy enforcement practices along with recording security-related events. The security requirements of organizations can be satisfied with Group Policy tools which create extensive auditing functionalities that monitor security happenings and user interactions and system modifications and access attempts. Audit logs operated by Group Policy provide essential proof that shows policy concurrence with both organizational standards and regulatory requirements.
The systematic design of Group Policy provides great value to compliance initiatives by allowing users to match settings directly with essential NIST and ISO 27001 and industry-specific regulatory requirements. Group Policy reports enable auditors to show exactly how technical controls appear throughout the organization during requests for implementation evidence. The systematic method of compliance auditing using Group Policy first reduces audit stress for technical support staff and provides continuous policy violation monitoring to detect violations which would otherwise remain undetected until a security incident happens.
9. Power Management Optimization
Environmental initiatives and cost-reduction efforts both benefit from centralized power management capabilities in Group Policy. Enterprise-wide energy conservation functions become possible through organizational implementation of three monitors-related settings including display dimming and computer hibernation during unstaffed hours and processor efficiency optimization. Such policies allow for dual effectiveness between maximizing energy efficiency while maintaining user productivity by applying selected settings during daytime operations but different ones at night.
Larger firms experience significant financial consequences because of their power management procedures. Organizations that maintain 1,000 computers obtain annual power savings of tens of thousands of dollars through optimized power management which simultaneously decreases their environmental impact. Group Policy enables organizations to achieve financial power savings because it implements uniform configurations across all devices independently from user-related setup mistakes. These policies enable organizations that adopt environmental goals or sustainability objectives to track measurable outcomes which stakeholders can review for corporate social responsibility reporting.
10. Targeted Policy Application Through Filtering
Group Policy includes advanced filtering capabilities to prevent policies from reaching inappropriate system elements. Security filtering enhances Group Policy application by enabling administrators to set restrictions against specific security groups thus allowing better control of job role-based and departmental settings. Advanced WMI filters make decisions about policy application through an examination of system attributes which may include hardware details and installed software lists and network parameters.
The point-by-point precision of these targeting methods stops the conventional widespread policy implementation practices which generate conflicts or restrictions. The execution policies given to developers contain fewer restrictions that enable testing tools while accounting staff get policies which focus on data security measures. Mobile users who access their computers with laptops automatically receive different optimized policies through configurations made specifically for their portable devices to accomplish battery and network requirements. Through filters Group Policy transitions from being a general tool to a precise instrument which distributes exact settings to exact users and systems.
How to Create and Apply Group Policies
Preparation Steps
- Log in with Administrative Privileges
- Sign in to a domain-joined computer with an account that has domain administrator permissions
- Ensure you have proper network connectivity to your domain controllers
- Launch Group Policy Management Console
- Press Windows key + R to open the Run dialog
- Type gpmc.msc and press Enter
- Wait for the Group Policy Management Console window to open completely
Creating a New Group Policy Object
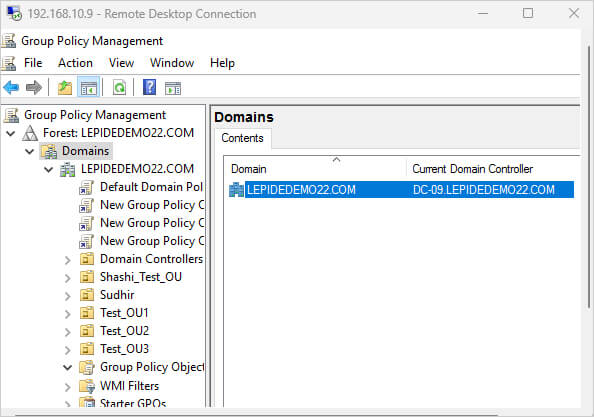
- Navigate to Your Domain Structure
- In the left navigation pane, expand the “Forest” node
- Expand the “Domains” node
- Locate and click on your domain name
- Create the GPO
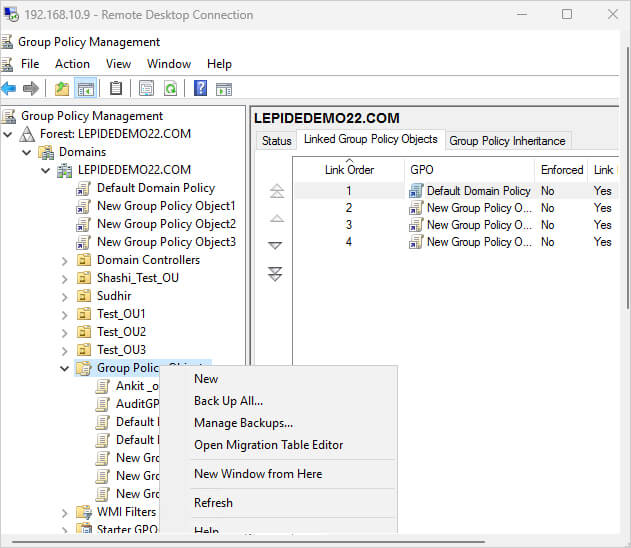
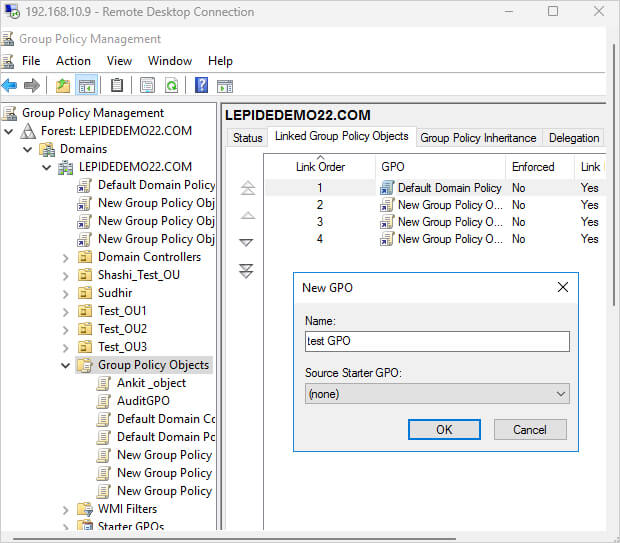
- Right-click on the “Group Policy Objects” container
- Select “New” from the context menu
- Enter a descriptive name for your new GPO (e.g., “Workstation Security Settings”)
- Optionally, add a comment to describe the purpose of this GPO
- Click “OK” to create the GPO
- Configure GPO Settings
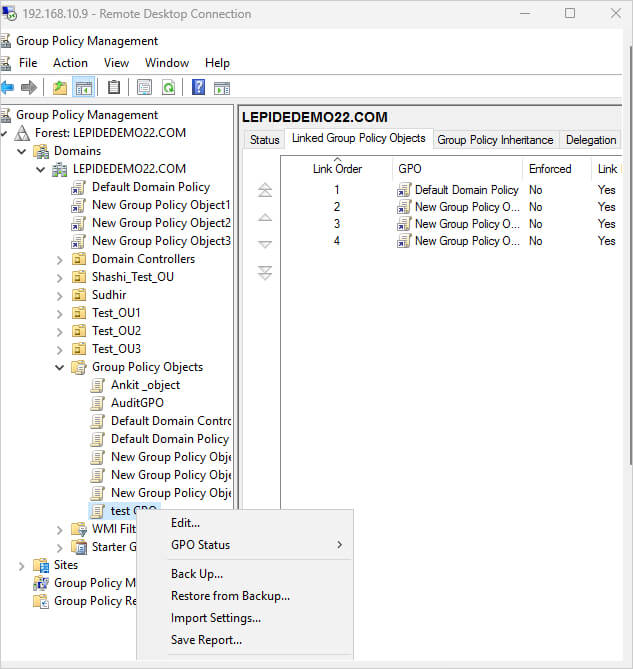
- Right-click on your newly created GPO in the “Group Policy Objects” container
- Select “Edit” from the context menu
- The Group Policy Management Editor will open in a new window
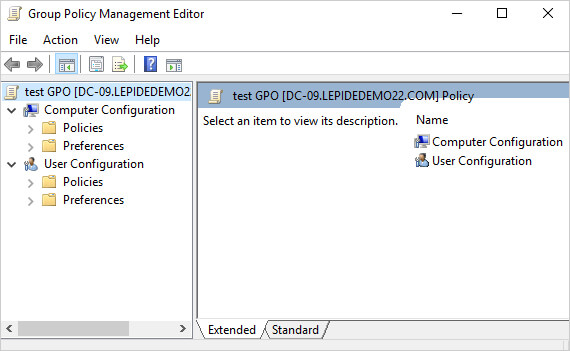
- Select and Configure Policy Settings
- Navigate through the folder structure to locate desired settings
- For computer settings: Expand “Computer Configuration”
- For user settings: Expand “User Configuration”
- Browse through the appropriate subcategories (Policies, Windows Settings, Administrative Templates, etc.)
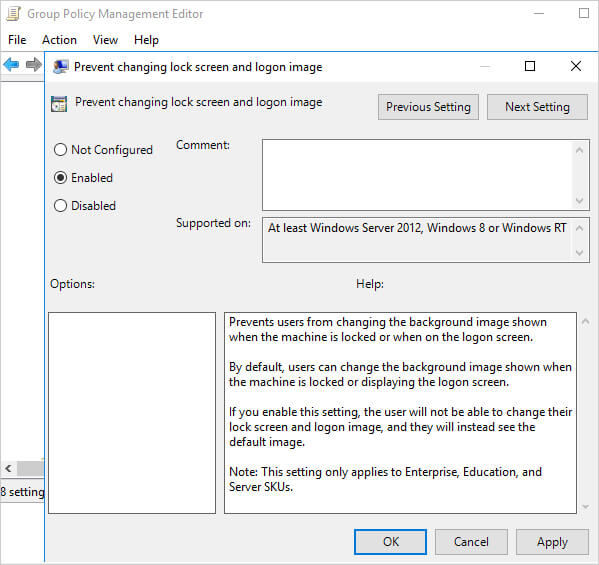
- Double-click on specific settings to configure them
- Set each option to “Enabled,” “Disabled,” or “Not Configured” as needed
- Configure any additional parameters required by the specific policy
- Click “Apply” and then “OK” for each setting
- Save Your Changes
- Close the Group Policy Management Editor when finished
- Your changes are saved automatically
Linking and Applying the GPO
- Link GPO to an Organizational Unit
- In the main Group Policy Management Console window, navigate to the OU where you want to apply the policy
- Right-click on the target OU
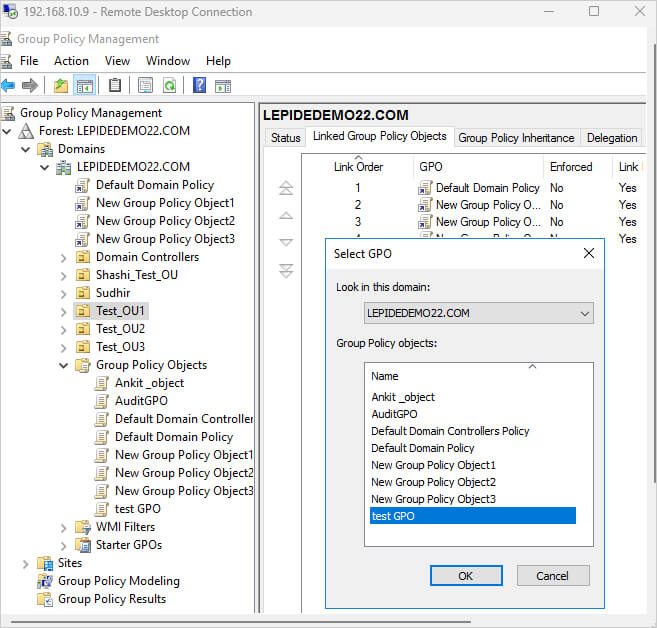
- Select “Link an Existing GPO”
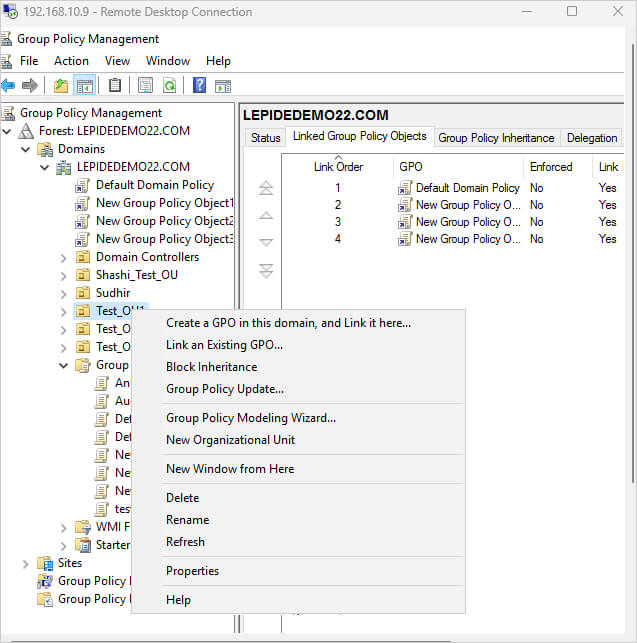
- Select your newly created GPO from the list
- Click “OK”
- Configure GPO Scope (Optional)
- Click on the linked GPO under your target OU
- In the right pane, click on the “Scope” tab
- Under “Security Filtering,” you can specify which users, computers, or groups the policy applies to
- By default, it applies to “Authenticated Users”
- Click “Add” to specify different security groups if needed
- Configure GPO Priority (If Multiple GPOs Exist)
- With your OU selected, view all linked GPOs in the right pane
- Use the “Link Order” column to determine processing priority (lower numbers process first)
- Right-click on your GPO and select “Move Link Up” or “Move Link Down” to adjust priority
Testing and Verification
- Force Policy Update (Optional)
- On a computer affected by the policy, open Command Prompt as administrator
- Type gpupdate /force and press Enter
- Wait for the update to complete
- Verify Policy Application
- On a test computer, open Command Prompt as administrator
- Type gpresult /r to see applied policies
- For a more detailed report, use gpresult /h c:\temp\report.html to generate an HTML report
- Review the report to confirm your policy settings are applied correctly
Improper Configurations of Group Policies
Common Mistakes and Security Risks: The incorrect setup of Group Policy entails multiple security holes alongside decreased operational effectiveness and non-conformance problems. System unpredictability occurs when administrators employ different GPOs that conflict with each other at various organizational levels. Several restrictive policies enforced simultaneously end up creating significant slowdowns in system performance and disruption of user work processes.
Best Practices for Avoiding Issues: System misconfigurations can be avoided through proper testing of GPOs performed by IT administrators before GPO deployment. Peeking into GPO modifications on a regular basis, along with monitoring activities helps to locate unexpected adjustments and protect system security. The risk of errors decreases through proper policy documentation and controlled access to essential Group Policy Objects that is limited to authorized personnel.
How Lepide Helps
Group Policy functions as a top-tier IT management solution because it enables businesses to implement security standards along with standardized configurations together with automated system administration procedures. Group Policy implementation with correct management leads to the development of safe IT environments while maintaining regulatory compliance and operational efficiency.
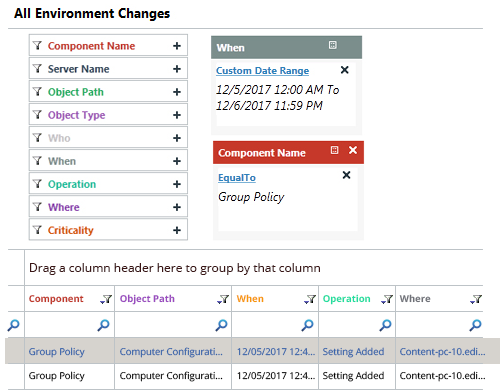
Lepide delivers advanced Group Policy auditing and monitoring capabilities that enable organizations to monitor changes and detect unauthorized modifications alongside security policy compliance violations. Real-time alert systems and reporting capabilities help IT staff enforce Group Policy control while preventing security threats.
Lepide helps businesses build stronger security positions while minimizing operational dangers and ensuring regulatory compliance. If you want to know more about how Lepide can help you create seamless GPOs, download the free trial today!