Last Updated on April 22, 2025 by Deepanshu Sharma

Group Policy Objects (GPOs) are valuable tools for system administrators, allowing them to manage applications, software operations, and user settings across an organization. GPOs help improve the safety and efficiency of an organization’s IT infrastructure and user base. This article provides an introduction to GPOs, explains their functionality, offers configuration and maintenance tips, and discusses their role in maintaining cybersecurity.
What Is a Group Policy Object?
A group policy object (GPO) is a preconfigured command or template that controls the settings and policies of multiple Windows operating systems. It is managed through Microsoft Active Directory, allowing system administrators to apply GPOs to users, machines, or software across an entire organization. GPOs can be used to adjust settings in areas such as security, software installation, scripts, and folder redirection. This enables administrators to remotely manage many systems and software from Active Directory.
What are the Advantages Of Group Policy Objects (GPOs)?
Using Group Policy Objects (GPOs) can be an effective security strategy for organizations as it allows administrators to quickly and conveniently implement security measures across the entire organization from the Active Directory. GPOs work best when properly installed and configured, offering benefits such as stronger password policies, improved folder protection, and ease of security management.
In addition to the above, GPOs provide several benefits for organizations, which include:
- Centralized Management: GPOs allow for the centralized administration of computer and user settings, ensuring consistency across the network.
- Robust Security: GPOs enable IT administrators to enforce strong security measures, such as password policies and regular password changes, reducing the risk of compromise.
- Improved Accessibility: GPOs offer features like folder redirection and offline files, allowing users to access files even with poor network connectivity, facilitating seamless collaboration.
- Consistent Computing Environment: GPOs ensure that users have a consistent computing experience, regardless of the workstation they use, promoting efficiency and familiarity.
- Data Protection: By redirecting user files to a server location, GPOs help safeguard data by preventing loss due to workstation failures. Regular backups mitigate the risk of data loss, preserving vital information.
What are the Disadvantages Of Group Policy Objects (GPOs)?
GPOs are not a foolproof network security solution. They can be vulnerable to cyberattacks, especially if a hacker exploits local GPOs to gain unauthorized access. Detecting such activity without advanced monitoring software is challenging. Furthermore, the GPO editor is not user-friendly and requires administrators to have a deep understanding of PowerShell to ensure proper updates. Neglecting to update GPOs regularly can also lead to cybersecurity vulnerabilities. Additionally, there is no built-in search or filter option in the GPO editor, making it difficult to locate and address specific settings.
In addition to the above, GPOs have several disadvantages that should be considered:
- GPOs restrict network flexibility: GPOs are only applicable to users or computers. They are not adaptable for broader settings or for reacting to dynamic environmental changes.
- Maintenance of GPOs can be complex: There is no built-in filter option for locating specific settings, which makes it challenging to identify and resolve issues within existing configurations.
- GPOs may lead to slower logon processes: Sequential processing of GPOs can slow down user logon processes if configurations take a long time to implement.
- GPOs lack a comprehensive audit system: This makes it difficult for IT administrators to track changes or determine who initiated them. The lack of transparency and accountability is also problematic.
It is important to consider these drawbacks alongside the advantages of using GPOs to make informed decisions when implementing them in your organization.
What are the common type Types of GPOs?
Group Policy Objects (GPOs) represent core components of IT management because they enable organizations to implement security policies, manage permissions and control system functions throughout Active Directory (AD) environments. Group Policy Objects exist in different organizational types which enable specific control parameters along with unique flexibility degrees. Three significant types of GPOs which operate within IT environments are as follows:

1. Local Group Policy Objects
Local Group Policy Objects allow direct configuration and storage on individual computers to control device operations. The configuration of a particular device remains controlled by Local Group Policy Objects through security settings, application behavior and user interface elements. Users can handle Local GPOs by using the Local Group Policy Editor (gpedit.msc) which operates independently from network connections. The scope of Local Group Policy Objects stays within one machine because they exist solely on the devices where they were created. Thus they suit standalone computers yet offer permission control for isolated exceptions.
2. Non-Local GPOs
Non-local GPOs or Domain Group Policies exist as centrally managed configurations on domain controllers operating under Active Directory environments. Administrators distribute these policies to multiple organization computers through which they keep all network devices standardized using a uniform setting.
Non-local GPOs demonstrate superior power over local GPOs because they enable administrators to control specific user and computer groups as well as inherit policy changes across these groups automatically. Through the Group Policy Management Console (GPMC), administrators execute the management of enterprise-wide configuration requirements to establish centralized control in enterprise environments.
3. Starter GPOs
Starter GPOs establish basic templates to assist administrators in creating new group policies. These templates include predefined settings functioning as a foundation for administrators to modify them as needed. Starter GPOs serve three essential functions: they protect consistency across IT policy creation processes, speed up policy generation through standardized configurations, and minimize configuration errors. Starter GPOs serve enterprises who have many administrators needing standardization by providing templated policy settings for policymakers to begin. Starter GPOs enable the creation of equivalent baseline configurations that persist throughout various policy deployment environments.
How Are GPOs Processed and Worked?
GPOs follow a specific order of processing called LSDOU (Local, Site, Domain, and Organizational Unit). It starts with the local computer policy, followed by Active Directory policies from site to domain. Next, GPOs within organizational units apply, starting from the closest OU to the root and moving outward. If conflicts occur, the most recently applied policy takes precedence.
How Do GPOs Work?
Here is a brief overview of how GPOs work:
- Creation and Configuration: Administrators use the Group Policy Management Console (GPMC) to create and configure GPOs. Each GPO consists of policies and settings that define computer and user behavior, such as security protocols, software regulations, and access permissions.
- Scope Assignment: GPOs are linked to specific Active Directory containers, such as domains, organizational units (OUs), or sites, determining their impact. For example, an OU-linked GPO will affect users and computers within a particular department.
- Hierarchy and Inheritance: GPOs follow a hierarchical structure, where settings trickle down through inheritance. Multiple GPOs’ settings can combine to affect a single user or computer.
- Processing: GPOs linked to relevant containers are processed in sequence during logon or startup. This processing takes into account local, site, domain, and OU-based GPOs. Filters are applied to determine applicability.
- Policy Application: After processing, the policies within the GPOs influence user sessions or computer configurations. This affects various aspects, including security settings, appearance, software installations, and access permissions.
- Policy Refresh: GPOs refresh periodically to ensure that the configurations remain up to date and reflect any changes or updates. This ensures that the desired settings are consistently applied throughout the network.
- Group Policy Replication: GPOs are stored in Active Directory and synchronized across domain controllers, ensuring network-wide consistency. Any changes made to GPOs are replicated throughout the network.
- Feedback and Control: Administrators can monitor GPOs using tools like Event Viewer and Group Policy Results. These tools provide insights into the application of policies and allow administrators to enforce desired settings and configurations.
How To Configure and Maintain Group Policy Objects.
To configure group policy objects, you need to use the Group Policy Management Console (GPMC), which can be accessed on domain controllers or installed on servers using the Install-WindowsFeature command line. Once you have access to the GPMC interface, you can create, edit, or delete GPOs according to your requirements.
- Step 1: Connect the group policy to the domain by linking it to the appropriate OU in the GPMC tool.
- Step 2: Customize the GPO settings to your preferences and understand the distinction between the GPO itself and the GPO link.
- Step 3: Arrange the order of GPO application in the linked OUs, avoiding conflicting settings and prioritizing important GPOs.
To maintain group policy objects (GPOs), it is important to follow certain principles and practices. Firstly, give each GPO a descriptive name and add comments explaining its purpose and preferred settings. This helps administrators quickly understand and identify the GPOs. Additionally, it is crucial to regularly backup the GPOs in a recoverable format using GPMC (Group Policy Management Console). This ensures that in the event of a security breach or system hack, the GPOs and their settings can be easily restored. Overall, maintaining GPOs involves labeling them clearly and backing them up regularly in order to facilitate efficient management and recovery processes.
What is The Role of GPO in Data Security?
Organizations need Group Policy Objects to establish data protection measures against cybersecurity threats to guard their information systems. The establishment of well-configured GPOs allows organizations to protect their sensitive data and ensure security compliance while decreasing unauthorized system access and data breach vulnerability.
Restricting Unauthorized Access
User access to organizational data and internal systems is the main security mission which GPOs fulfill. The Group Policy settings allow administrators to set restrictive access policies that limit file access to only approved staff users. The configuration of GPOs through an organization handling confidential financial records enables administrators to define access standards based on user roles thus authorizing finance department employees to access sensitive files. The combination of guest account disabling and least privilege access rules increase security posture by blocking unauthorized users from system resources.
Enforcing Strong Password Policies
The accessibility through weak passwords functions as a main entry point that cybercriminals utilize. Through the implementation of authentication security standards, GPOs maintain strong password protection by applying multiple security requirements that regulate changing passwords periodically and appropriate account freeze protocols for defending against brute-force attacks. Organizations that set these configuration parameters at the domain level create standard password protection frameworks that protect all employees from credential-based threats.
Controlling Software Installation and Execution
Security risks from uncontrolled software installations create multiple threats. These include malware infiltration, unauthorized applications, and non-compliance with software licensing requirements. Administrators who implement GPOs establish the framework for software management. This is done by enforcing limitations on unapproved installations, an authorized whitelist of executable applications and preventing the execution of unverified files and scripts from unidentified sources. The implementation of GPOs to block executive file downloads from unreliable websites by IT teams results in a substantial reduction of malware threats in the network infrastructure.
Hardening Endpoint Security
Multiple cyber threats specifically target electronic devices which include laptops, desktops and mobile devices. Group Policy Objects enhance security on devices by implementing restrictions. These include USB port-blocking to prevent data theft and BitLocker encryption protection of lost or stolen data and Windows Firewall rule enforcement for blocked networks. Organizations can enhance endpoint defense security and reduce possible weak points through Group Policy standardization of security configurations.
Auditing and Monitoring Activities
GPOs help organizations retain user activity visibility through their enforcement of auditing and logging rules. Administrators can set up configuration directives to track user authentication attempts while determining unauthorized system access attempts. This can be alongside monitoring important system files and registry modifications which produce audit logs useful during investigation processes. Through GPO implementation financial institutions can enable auditing of critical financial records to keep track of unauthorized access attempts which become subject to review for security incident detection.
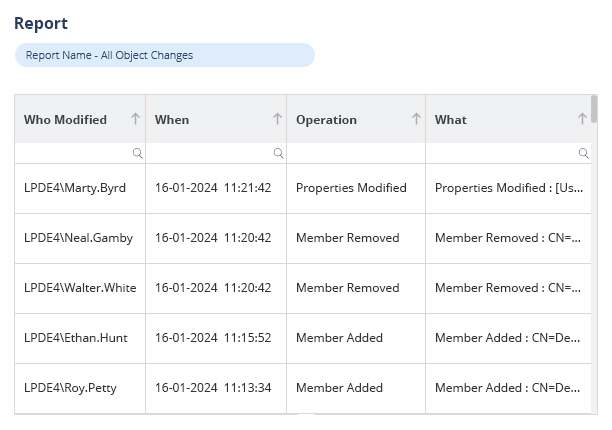
How Lepide Helps Secure Group Policy
GPOs form an integral part of a comprehensive security strategy; however, they can’t provide complete protection by themselves. You must also be able to track changes made to your GPOs and other AD objects.
The Lepide Auditor for Group Policy can help to secure your GPOs through real-time monitoring of your Active Directory environment. Lepide uses machine learning algorithms determine typical usage patterns, and real-time notifications can be sent to your inbox or mobile device when deviations from these patterns are detected.
If you’d like to see how the Lepide Data Security Platform can help you safeguard your GPOs from unauthorized manipulation, schedule a demo with one of our engineers or download free trial today.
 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
