Last Updated on April 17, 2025 by Deepanshu Sharma

It is more important than ever to protect your company’s data in the modern digital world, where cyber threats are persistent and sophisticated. Imagine having a watchful security camera inside your IT infrastructure that records each system event, policy change, and access attempt with precision. This is exactly what Windows Audit Policy provides. It is a strong but frequently overlooked tool that acts as your company’s internal monitoring system. It can be used by IT managers to help ensure adherence to strict industry laws and identify illegal activity by properly setting up and monitoring these audit policies.
What is Windows Audit Policy?
Windows Audit Policy allows you to specify which security-related events are logged on a Windows system. By configuring this policy, you can monitor and record specific activities, such as remote access attempts, while choosing not to log other activities, such as local login attempts within your organization. This feature enables you to establish a security auditing system for individual computers or an entire Windows network. Technically, it consists of settings that define the types of security events a Windows computer or domain server should track. When these events occur, details are recorded in the system’s security logs for your review. By considering potential security risks, an audit policy efficiently provides information that helps in the early detection of security breaches.
Download 20-Day Free Trial

What are the different types of Windows audit policies?
Windows has two main audit policy configuration frameworks:
- Basic Audit Policy
- Advanced Audit Policy

Basic Audit Policy
Basic security audit policies, also known as local Windows security settings, enable you to configure auditing on a per-event-type basis. These settings allow you to define which categories of events—such as logon attempts, account management, or object access—are monitored and recorded in the security logs. Listed below are the categories available in basic audit policy:
- Audit Account Login Events: Monitoring user logon events is essential for detecting unauthorized access attempts within a domain. Auditing both successful and failed logon attempts enables the identification of potential unauthorized access attempts. It’s important to note that while logon events are recorded, logoff events are not tracked on domain controllers.
- Audit Account Management: Thoroughly tracking all user account modifications helps reduce the risk of business interruptions and ensures system availability.
- Audit Directory Service Access: Enable monitoring only when you need to track access to an Active Directory (AD) object that has a defined System Access Control List (SACL), such as an Organizational Unit (OU).
- Audit Logon Events: This policy would record both successful and unsuccessful attempts to turn on or off a local computer that is helpful for post-event forensics and intruder detection.
- Audit Object Access: This auditing policy would only track information to determine when someone accessed, copied, distributed, altered, or removed data from file servers using their privileges.
- Audit Policy Change: Unauthorized or incorrect modifications to Group Policy Objects (GPOs) can significantly compromise your organization’s security posture. Regularly monitoring all GPO changes is essential to mitigate the risk of data exposure and maintain a secure environment.
- Audit Privilege Use: To monitor each instance of user privilege utilization, enable the “Audit Sensitive Privilege Use” policy. It’s recommended to configure this setting granularly within the advanced audit policies under “Privilege Use” to ensure comprehensive visibility of sensitive operations.
- Audit Process Tracking: Auditing events related to processes—such as their creation, termination, duplication, and indirect object access—can enhance incident investigations by providing detailed tracking information.
- Audit System Events: Configuring your system’s audit policy to log events such as startups, shutdowns, restarts, and unauthorized process actions is crucial for maintaining security. For instance, if malicious software attempts to modify system settings without permission, system event auditing will capture and record that activity, enabling prompt detection and response.
Advanced Audit Policy
Advanced security audit policies in Windows address the same areas as basic audit policies but provide administrators with more detailed control over the specific events to be monitored within each category. This granularity enables organizations to focus on monitoring events that are most relevant to their security needs, thereby reducing unnecessary log entries and enhancing the efficiency of security event analysis. The Advanced Audit Policy settings are organized into the following categories:
-
- Account Logon: Enables administrators to track and document each instance of user logon and logoff activity on a domain controller or on a local Security Accounts Manager (SAM).
- Account Management: The “Audit Account Management” policy is crucial for monitoring and recording both successful and failed events related to account management activities. Key areas examined by this policy include:
- Audit Computer Account Management
- Audit Other Account Management Events
- Audit Security Group Management
- Audit User Account Management
- Detailed Tracking: The Detailed Tracking audit policy category in Windows enables monitoring of individual application and user activities on a computer, providing insights into how the system is utilized.This category includes the following four subcategories:
- Audit DPAPI activity
- Audit Process Creation
- Audit Process Termination
- Audit Directory Service Replication
- Logon/Logoff: Tracks all log on attempts to a computer interactively or over a network. These events are essential for identifying potential network attacks. This policy category includes several subcategories:
-
- Audit Account Lockout
- Audit/User /Device Claims
- Audit Group Membership
- Audit IPsec Extended Mode
- Audit IPsec Main Mode
- Audit IPsec Quick Mode
- Audit LogOn
- Audit LogOff
- Audit Network Policy Server
- Audit Special Logon
- Audit other Logon -Logoff Events
- Object Access: Monitors attempt to access specific objects or object types on a network or computer. Some important subcategories of this category includes:
-
- Audit Application Generated
- Audit File Share
- Audit Detailed File Share
- Audit File System
- Audit Filtering Platform Packet Drop
- Audit Certification Services
- Audit Removable Storage
- Audit Registry
- Policy Change: The Policy Change audit category in Windows tracks modifications to critical security policies on a local system or network. This category comprises six subcategories, each focusing on specific policy changes:
-
- Audit Audit Policy Change
- Audit Authentication Policy Change
- Audit Authorization Policy Change
- Audit Filtering Platform Policy Change
- Audit MPSSVC Rule-Level Policy Change
- Audit Other Policy Change Events
- DS Access: The DS Access security audit policy settings offer a comprehensive audit trail of attempts to access and modify objects within Active Directory Domain Services (AD DS). These audit events are logged exclusively on domain controllers and encompass the following four subcategories:
- Audit Detailed Directory Service Replicatio
- Audit Directory Service Access
- Audit Directory Service Changes
- Audit Directory Service Replication
- Privilege Use: Enable these settings only if there is a specific need for the data to be logged, as they can generate a substantial number of entries in the security logs.
- Process Tracking: These settings allow the operating system to generate audit events whenever a process starts. It is recommended to activate them only when there is a specific need for security logs. Audit Process creation – Success.
What are the best practices for Windows Audit Policy?
Some of the Windows Audit Policy recommended practices that are covered in detail are listed below:
- Determine the Type of Event to audit: One best practice is to determine which events require auditing and set up the appropriate parameters for each before making any changes. The collection, storage, and analysis of audit data must be well planned because collecting a large amount of data without a plan may make it more difficult to draw insightful conclusions from it. A few of the events that can be audited in the Windows Server environment are process tracking, policy changes, object access, DS access, and account login.
- Advanced Audit Policy Configuration: It is crucial to remember that the advanced policies are meant to supplement the fundamental policies, not to replace them. However, using the advanced audit policy settings and the basic audit policy settings at the same time is not a good idea because this can lead to conflicts. More control is possible and excessive log volumes are avoided by configuring audit policies using the Advanced Audit Policy Configuration. Use can be made of Windows Server 2008’s Advanced Audit Policy settings, which offer more precise auditing control than the Basic Audit Policy. By eliminating pointless log entries and concentrating on important occurrences, this method enables you to define comprehensive audit criteria.
- Set Audit Log Size: In audit logs, security-related events are documented, such as policy changes and login attempts. Inadequate configuration of these logs to capture new events after they fill up their storage limit may lead to security blind spots. Maintaining system performance and preventing significant data loss are achieved by setting an appropriate maximum log size. The maximum size of the audit log must be configured in Windows Audit Policy administration. Security monitoring and compliance are made easier by appropriate configuration, which ensures an ongoing recording of security events.The Security log’s maximum size and other properties should be specified in the Event Logging policy settings. The storage space allocated for storing the audit data may quickly fill up, thus this is quite important.
- Conduct Performance Test: It is crucial to do performance tests when setting up Windows Audit Policies to make sure that auditing improves security without negatively impacting system performance. In order to balance security requirements with operational efficiency, audit settings can be optimized through performance testing, which also aids in locating possible bottlenecks. Enabling comprehensive auditing may result in a large number of log entries, which could raise storage, CPU, and disk I/O utilization. These elements have the potential to impair user experience and system performance in the absence of adequate testing. Performance testing should therefore be done prior to introducing new audit parameters in a production scenario.
- Regularly Review and Analyze Logs: Maintaining a safe and legal IT environment requires routinely going over and evaluating Windows audit logs. This procedure involves methodically going over log entries to find irregularities, making sure that rules are followed, and spotting possible security risks. To make sure that businesses follow set security guidelines and procedures, several regulatory frameworks require routine log assessments. Analysis on a regular basis improves compliance initiatives and shows due diligence.
- Identifying High-Risk Areas: To improve system security and guarantee compliance, Windows Audit Policy must concentrate on high-risk areas. By focusing auditing efforts on the most susceptible elements, organizations can better identify and address possible problems. Keeping track of both successful and unsuccessful logon attempts aids in the detection of unwanted access. By focusing auditing efforts on these high-risk areas, companies may improve their security posture and guarantee that industry standards are being followed.
How Lepide Helps?
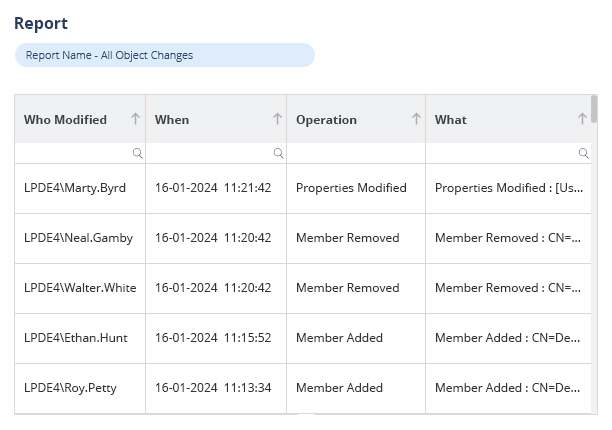
Lepide Auditor assists in creating and implementing a Windows audit policy by offering continuous monitoring, alerts, and reports on essential activities within your Windows environment. This enhances security, aids in meeting compliance standards, and boosts operational efficiency. The Lepide Solution has the ability to monitor both successful and unsuccessful user login attempts. In order to assist administrators in identifying potentially harmful login activity and resolving problems with locked accounts, it can also track account lockouts.
Our Solution offers comprehensive Active Directory auditing by monitoring and reporting on critical changes such as user account modifications, group adjustments, permission alterations, and organizational unit updates. It delivers real-time alerts for significant changes and enables the generation of customized reports with ease.
To learn more about how Lepide can help secure your Windows Server environment, download the Free Trial or schedule a demo with one of our engineers

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
