Last Updated on January 17, 2025 by Satyendra

Monitoring file activity is not as straight forward as it sounds. After all, in order to detect and respond to suspicious or troublesome file activity, we need to know in advance what it is we are actually looking for.
Most Common File Activity Monitoring Use Cases
Below are some of the most common scenarios that can compromise either the security or integrity of our critical files, along with a brief summary describing how Lepide Auditor for File Server can help us resolve them.
1. An employee copies valuable business data onto a portable drive
An employee decides to leave the company. However, before leaving they decide to copy lots of valuable business data onto a portable drive, to sell, or share with a competitor.
Using Lepide Auditor we can view a summary of a specific employee’s activity within a given timeframe to see what files they may have copied. We can also set up a real-time alert if a certain number of files are copied in quick succession.
2. A privileged user accidentally modifies the permissions of a file
A privileged user accidentally modifies the permissions of a given file, thus preventing other users from accessing it.
Using the Lepide Solution we can receive real-time alerts when file permissions are changes, and/or view a summary of activity to see who modified the permissions, and when.
3. An employee accidentally deletes, renames or moves a file
An employee accidentally deletes, renames or moves a file to a different location, thus preventing other users from finding it.
Using Lepide Auditor we can view a summary of events to see why the file is no longer accessible.
4. An employee modifies a file’s content
An employee modifies the contents of a file such that it destroys the integrity of the data contained within it.
Using Lepide Auditor we can see who modified the contents of the file, and when.
5. A large number of files have been encrypted
A large number of files have been encrypted within a short period of time indicating that a ransomware attack may have been initiated.
Using Lepide Auditor we can automatically detect and respond to events that match a pre-defined threshold condition. If X number of files have been encrypted within a short period of time, a custom script can be executed to prevent the attack from spreading. Actions may include disabling a user account, stopping a specific process, changing the firewall settings, shutting down the affected server, and more.
6. An administrator wants to restrict file access
An administrator wants to restrict access to a file to ensure that access is only granted to those who need it. However, he/she doesn’t know who should or shouldn’t have access to that file.
Using Lepide Auditor we can see who has access to a specific file, why, and how often. This information can also be correlated with the reasons why they were granted access in the first place. Using this information, the administrator can make an informed choice about who should or shouldn’t have access to the file. Naturally, access rights can be granted or revoked on an ad-hoc basis.
7. A sensitive file accessed outside of typical work hours
A file containing sensitive data is accessed outside of typical work hours, indicating that something suspicious could be taking place.
In the event that someone is accessing sensitive data during hours that are unusual for that particular user, the Lepide DSP can send a real-time alert to the administrator’s inbox or mobile phone, enabling them to quickly investigate the situation.
8. An administrator wants to revoke file access
An employee leaves the company and the administrator wants to ensure that the employee can no longer access any of the files.
Lepide Auditor can automatically detect and manage inactive user accounts, and thus revoke access to the files their account had access to.
9. An administrator accesses files with sensitive data
An administrator misuses their admin rights and accesses files with sensitive data.
By setting real-time alerts, Lepide Auditor sends a notification regarding unauthorized access to sensitive data enabling you to investigate the situation and identify any account misuse.
10. Auditing of sensitive data
Regulations require organizations to record access events to files containing sensitive data.
Tracking and auditing file-read events on Windows File Servers and other changes occurring to sensitive data on file servers is a straightforward process using Lepide Auditor.
11. Ransomware Detection and Data Sabotage
Large numbers of files accessed and modified or deleted in a short period of time can be indicative of a ransomware attack or of data sabotage.
Typical ransomware attacks or data sabotage display characteristics which can be picked up by the Lepide threshold alerting capability. This ability to detect and alert on file activity which may be suspicious means that potential ransomware attacks or data sabotage can be identified in motion and immediate action taken which could be, for example, to shut down a server or revoke user access rights.
12. Stale File Clean-up
Tracking those files which are being actively accessed helps identify stale data for removal. This will increase storage space and reduce an organization’s risk surface.
The Lepide Stale Data Report gives you an overview as to how much data within your organization is deemed stale which is based upon a variable time frame you can specify.
13. Data Ownership
The ability to understand who accesses data, how often, and what actions they perform enables organizations to calculate data ownership, especially in the absence of quality file metadata.
Lepide Auditor provides administrators with the ability to analyze file activity, and user attributes to easily calculate data ownership.
14. Data Access Cleanup
Being aware of who is using their access privileges and the types of operations being performed helps reduce excessive access privileges that aren’t required.
Lepide Auditor provides excessive permissions reports which provide visibility as to who has access and what type of sensitive data they have access to. Once there is clarity as to exactly who requires access to do their job, it is a straightforward process to remove privileges for those who don’t need them.
Naturally, when monitoring file activity, it is important to prioritize. After all, we do not have unlimited resources, and thus we don’t want to be receiving real-time alerts every time a file is accessed, removed, modified, or deleted. However, providing that we are able to quickly answer questions pertaining to who, what, where and when, critical changes are made to our sensitive files, we will be in a much better position to keep them secure and accessible, as well as satisfy the relevant compliance requirements.
How Lepide Helps Audit and Monitor File Activity
Lepide File Server Auditor can be used to track all file and folder activities. Unlike native auditing, you do not have to manually enable the auditing for different files and folders. You just need to install the solution and configure the audit settings once and you are good to go.
Lepide Auditor has many different File Server auditing reports including the following example of the All Modifications in File Server report:
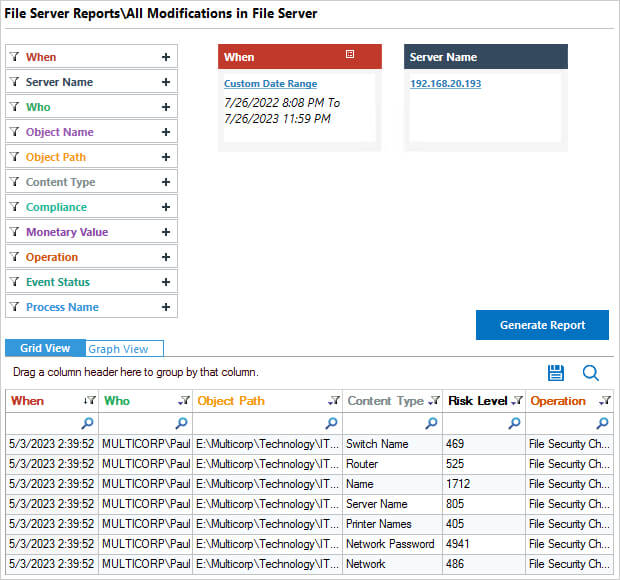
You can filter, sort and group the data as required and also save and export the report.
If you want to see for yourself how Lepide Auditor helps improve file activity monitoring, book a demo now.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
