Last Updated on February 11, 2025 by Satyendra
Both NTFS and Share permissions serve the same purpose within Windows environments; namely, to help you prevent unauthorized access to your critical folders. However, there are some critical differences between the two that will determine which one you use.
In this blog, we will learn about what NTFS permissions and share permissions are, what the differences between the two are, and the best practices for using them.
What Are NTFS Permissions?
New Technology File System (NTFS) is used to manage data stored on NTFS file systems and is the de facto file system for Windows NT and later operating systems. Unlike share permissions, NTFS permissions affect both network and local users. The types of NTFS permissions available are similar to share permissions but go into a bit more detail.
The basic types of access permissions for NTFS are Full Control, Modify, Read & Execute, Read and Write. Most of these are self-explanatory, and similar to share permissions. Read & Execute rights allow users to run executables, including scripts. The basic types of access permissions are described in more detail below.
NTFS Permission Types
- Full Control: Allows users to create, read, write, edit and delete files, folders and sub-folders. Users can also change the permissions for all files and folders in a directory.
- Modify: Allows users to modify and delete the files, file properties and folders in a directory.
- Read & execute: Allows users to read files and run executables, including scripts.
- List folder contents: Allows users to view a list of all files, folders and sub-folders in a directory. They can also view folder attributes and permissions, and even execute files, but they cannot view file contents.
- Read: Allows users to read files, file properties and folders in a directory.
- Write: Allows users to write to a file and add files to directories.
What Are Share Permissions?
Simply put, share permissions allow you to control who accesses folders over the network (they will not apply to those users who are accessing locally). In share permissions, you cannot control access to individual subfolders or objects on a share. Instead, share permissions apply to all of the files and folders within the share. Share permissions can be used with NTFS, FAT, and FAT32 file systems and allow you to determine the number of users who can access the shared folder.
Share Permission Types
- Full Control: Allows users to create, read, update and delete files and folders in a directory, as well as NTFS files and folders. By default, the “Administrators” group is granted “Full Control” permissions.
- Change: Allows users to read files, as well as add, edit and delete files and folders. “Change” permissions are not assigned by default.
- Read: Allows users to read content in files and folders, as well as execute programs. The “Everyone” group is assigned “Read” permissions by default.
Differences Between NTFS and Share Permissions
The type of permissions you choose to use will depend on what you’re looking to achieve and the resources you have available to you. Before deciding which permissions to use, there are a number of important differences between NTFS and Share permissions that you should be aware of. These differences are described below;
- NTFS permissions provide more granular control over shared folders and their contents than Share permissions
- When Share and NTFS permissions are used together, the most restrictive permissions are chosen by default. For example, if NTFS permissions are set to “Everyone Modify Allow”, and Share permissions are set to “Everyone Read Allow”, the Share permissions will override the NTFS permissions as they are more restrictive.
- Unlike NTFS permissions, Share permissions can be applied to FAT and FAT32 file systems.
- Unlike Share permissions, NTFS permissions apply to users who are logged on to the server locally.
- Unlike NTFS permissions, share permissions allow you to restrict the number of concurrent connections to a shared folder.
- Share and NTFS permissions are configured in different locations. Share permissions are configured in the “Advanced Sharing” properties in the “Permissions” settings, while NTFS permissions are configured on the Security tab in the file or folder properties.
Best Practices for Using Permissions
Your entire objective when using permissions should be to operate on a policy of least privilege, where users only have access to the files and folders they need to do their job. To help achieve this, there are a number of things you can do:
- Don’t assign permissions to user accounts: Permissions should be assigned only to groups in order to simplify the management of access to shared resources. If an employee in your organization changes roles and requires a new set of permissions, you can simply remove them and add them to the most appropriate groups.
- Use the Administrators group wisely: Users in this group will be able to do anything with your files and folders, including changing permissions. There are very few users who warrant this kind of control, and those that do need to be audited and monitored closely. You should use a third-party File Server audit solution to audit, monitor, and alert on changes administrators are making to your files and folders.
- Group objects together depending on security requirements: If there is a load of folders that apply to one particular department in the organization, group them into a parent folder and share that parent folder. This will save you from having to go through and share each folder individually.
How Lepide Helps in Analyzing NTFS and Share Permissions
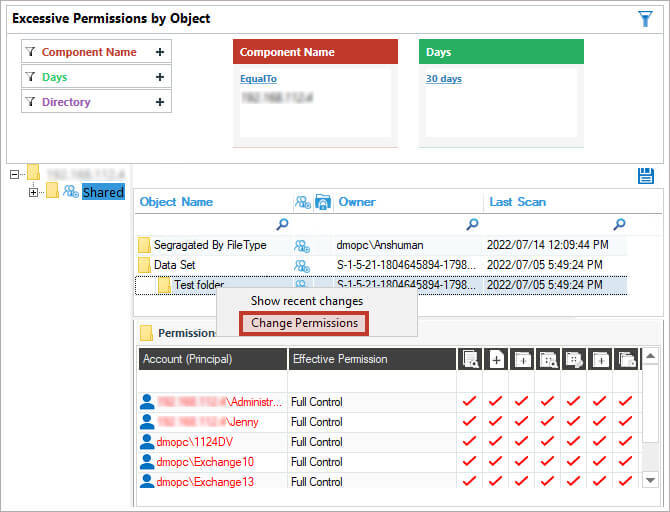
The NTFS permissions reporting tool from the Lepide Data Security Platform enables IT teams to analyze NTFS permissions applied to shared files and folders. It helps ensure that the right people have access to the right data, which minimizes the risk of security breaches. Using the Lepide Solution, you can instantly see who has received which permission, and from where, on a shared file or folder on your File Server. Pre-defined reports are included that clearly show the current permissions of Active Directory objects on the shared files and folders of a Windows File System.
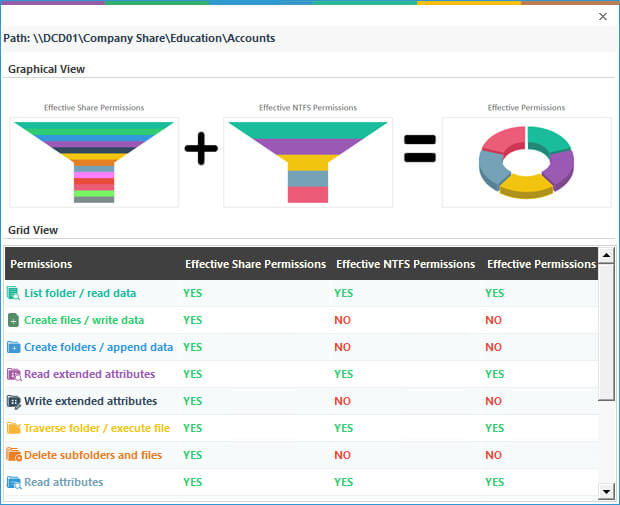
The example below shows the permissions status for the Accounts folder:
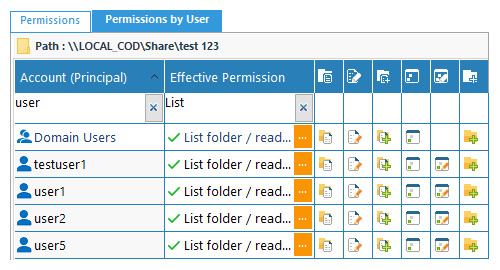
The following screenshot shows permissions by users:
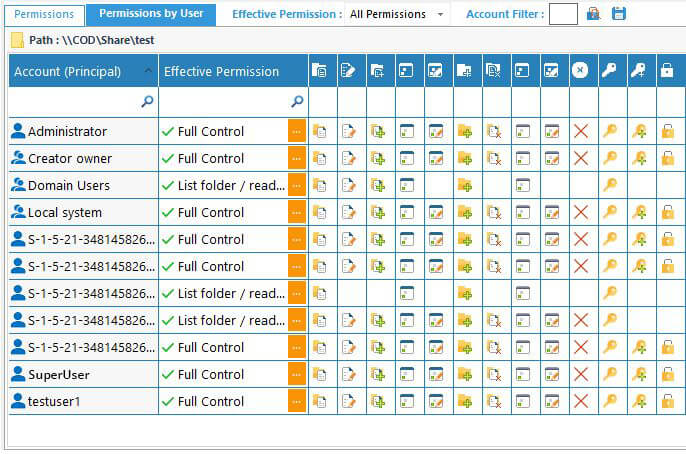
The below screenshot shows the user permissions on a particular folder:
In addition to the permissions reports, you can also reverse permissions for an object.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
