Last Updated on December 20, 2024 by Satyendra

Real-time data monitoring is more than just a routine security exercise; if done correctly, it can help you to stop security threats altogether.
Tracking data in real-time is essential to ensure security, as it gives security professionals the capability to watch over and manage organizational data access. In this article, I will discuss why real-time data monitoring is essential and how Lepide Data Security Platform can help you achieve it.
Why real-time data monitoring is important
As per the 12th annual Cost of Data Breach Study, conducted by the Ponemon Institute, data breaches on average have been bigger this year than last. The average size of a data breach increased by 1.8 percent to more than 24,000 records. Each breach on average costs around $3.62 million. Given the magnitude of these losses, it’s more imperative than before to secure your network from cyber-attacks.
So, what are the benefits of data monitoring towards that end? Real-time monitoring gives you complete visibility into network systems and a good understanding of your security stance. You should identify and focus on the most critical factors first.
Monitor data continuously in real-time
To keep your data safe, near-real-time monitoring of systems and system forensics is essential. To design a fail-safe threat response, you will have to start with advanced security monitoring, including user activities and system access tracking.
Your security threat response system should start with near-real-time monitoring, detection and analysis of system event logs where data is stored. The system log analysis should be able to tell you who is doing what, when, from where, and what business resources they are accessing.
However, security professionals are facing an information overload too. To avoid information overload, make your auditing more intelligent through prioritization.
Real-time data monitoring with Lepide Data Security Platform
Lepide Data Security Platform ensures that you can instantly find out answers to the ‘who, what, where and when’ questions related to file and folder auditing. You can also track and compare permissions of the files and folders. With this solution, you can also address insider-threat challenges and common regulatory compliance requirements.
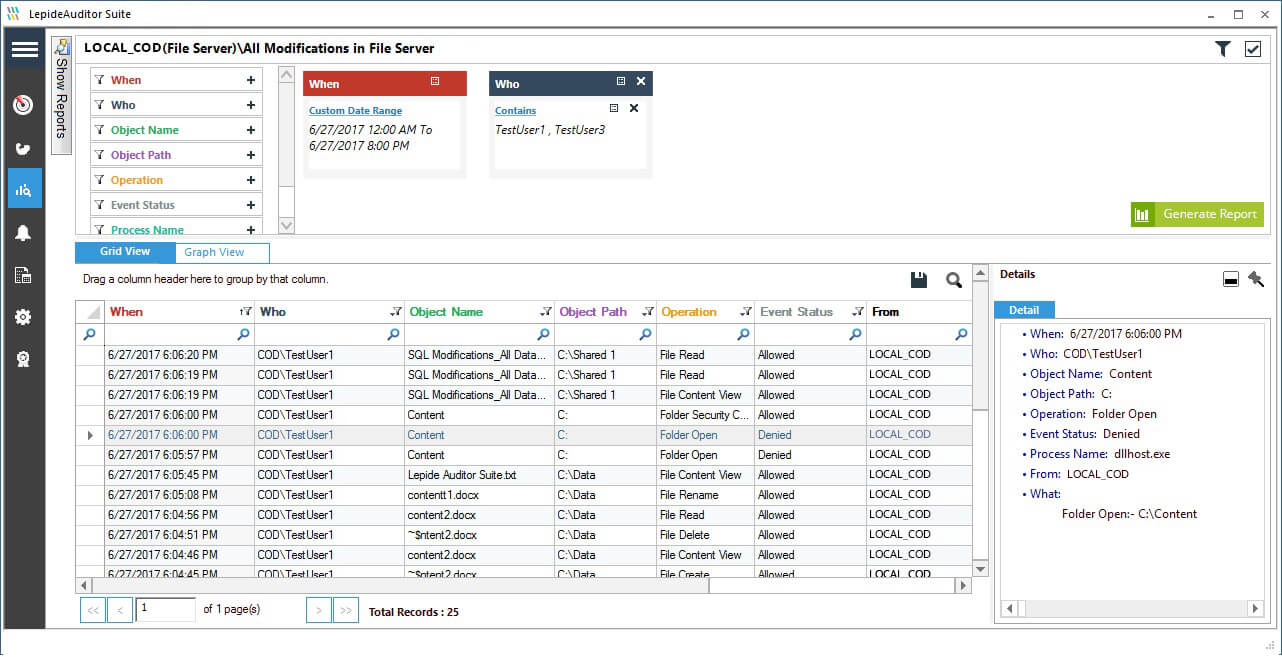
For an example, Lepide Data Security Platform have these reports are to monitor data on file servers: all modifications in File Server, shared files and folders, successful read and write, files and folders creation, deletion and modifications. It also gives you file and folder permission change reports. The following screenshot shows Lepide File Server Auditor’s “All Modifications in File Server” report.
Figure 1: All modifications in File Server
Lepide Data Security Platform lets you track all accesses made to data stored on Windows File System, NetApp Filer, and Exchange Server. It also allows you auditing configuration changes being made in Active Directory, Group Policy Objects, Exchange Server, SharePoint, SQL Server, Windows File System, NetApp Filer, and Office 365 (Exchange Online and SharePoint Online). You can audit the permission changes made across all of these server components.
Preventing security attacks with Lepide Data Security Platform
Currently, we’ve only really discussed the real-time data monitoring aspect of Lepide Data Security Platform. The solution also offers real-time alerts and threshold alerts, which notify you about suspicious activities in your IT environment that have the potential to be insider threats. You can also configure the solution to execute user-created custom scripts on the alerts to take certain actions. For example, you can configure our solution to run your own customized script to disable a user account if admin privileges are given to the user.
It also has a feature to roll back the unwanted changes made in Active Directory Objects and Group Policies. You can perform health monitoring of Active Directory, Exchange Server, and SQL Server and get real-time alerts also. book a demo with one of our engineers today.


 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
