Last Updated on December 24, 2024 by Deepanshu Sharma

Have you ever pondered over the intricacies of digital security in a world where data breaches lurk around every digital corner? Picture this: you’re safeguarding your organization’s network, but are you certain that every user accessing it is who they claim to be? Enter Kerberos, the guardian angel of network authentication. But here’s the catch: how do you ensure Kerberos itself isn’t compromised? The answer lies within Event ID 4768, the gateway to deciphering Kerberos authentication tickets.
Event ID 4768 Components
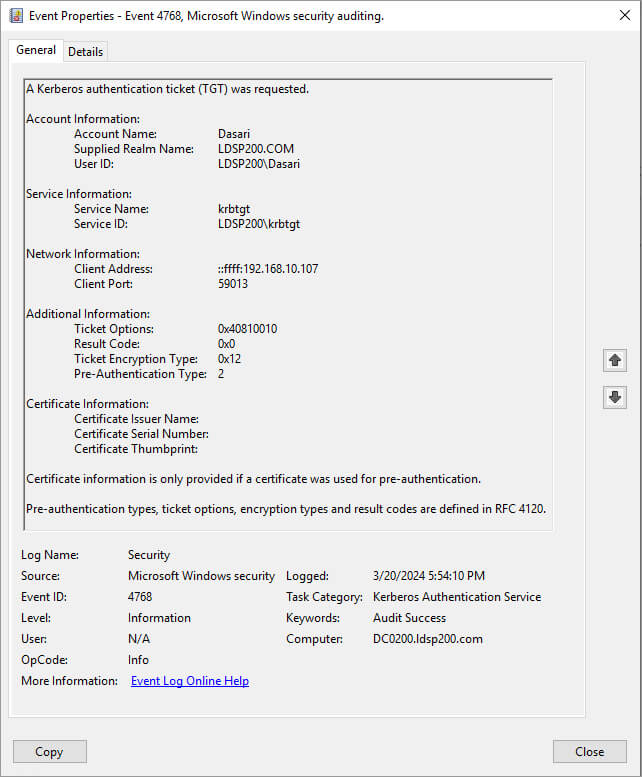
Account Information
Account Name: Specifies the name of the account for which a Ticket Granting Ticket (TGT) was requested. Notably, computer account names end with a $ symbol.
Supplied Realm Name: Identifies the Kerberos Realm to which the Account Name belongs.
User ID: Represents the Security Identifier (SID) of the account that requested a TGT. If the SID cannot be resolved, the source data appears in the event.
Service Information
Service Name: Indicates the name of the service in the Kerberos Realm to which the TGT request was sent.
Service ID: Denotes the SID of the service account in the Kerberos Realm to which the TGT request was sent.
Network Information
Client Address: Specifies the IP address of the computer from which the TGT request was received.
Client Port: Indicates the source port number of the client network connection. It’s typically “0” for local (localhost) requests.
Additional Information
Ticket Options: Represents a set of different ticket flags in hexadecimal format, including values like Forwardable, Renewable, Canonicalize, and Renewable-ok.
Result Code: Displays a set of different failure codes in hexadecimal format, providing insights into the outcome of the authentication attempt. Possible causes are varied, including issues like expired passwords, invalid credentials, or unsupported encryption types.
Ticket Encryption Type: Specifies the cryptographic suite used for issuing the TGT, such as DES, AES, or RC4.
Pre-Authentication Type: Indicates the code number of the pre-authentication type used for the TGT request, offering details about the authentication method employed.
Certificate Issuer Name: Identifies the name of the Certificate Authority (CA) that issued the smart card certificate.
Certificate Serial Number: Represents the serial number of the smart card certificate used during logon.
Certificate Thumbprint: Denotes the thumbprint of the smart card certificate, providing a unique identifier for authentication purposes.
Event 4768 Result Codes
0x18Pre-authentication information was invalidUsually means bad password0x1FIntegrity check on decrypted field failed
0x21Ticket not yet valid
0x23The ticket isn’t for us
| Result code | Kerberos RFC description | Notes on common failure codes |
|---|---|---|
| 0x1 | Client’s entry in database has expired | |
| 0x2 | Server’s entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client’s key encrypted in old master key | |
| 0x5 | Server’s key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | Administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction, or Authentication Policy Silo (look for event ID 4820) |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid – try again later | |
| 0x17 | Password has expired | The user’s password has expired. |
| 0x19 | Additional pre-authentication required* | |
| 0x20 | Ticket expired | Frequently logged by computer accounts |
| 0x22 | Request is a replay | |
| 0x24 | Ticket and authenticator don’t match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28/td> | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | May be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
How Does Kerberos Authentication Align with Event ID 4768?
Within the intricate maze of network security, Kerberos emerges as a steadfast guardian, meticulously validating the identities of users as they navigate the digital landscape. Fundamentally, Kerberos functions as a robust network authentication protocol, meticulously crafted to facilitate secure communication over inherently non-secure networks. Yet, amid the tumultuous skirmishes of the digital realm, one event shines with unparalleled importance – Event ID 4768. Like a beacon piercing through the darkness, Event ID 4768 serves as a guiding light, illuminating the intricate path of Kerberos authentication and unraveling its mysteries within the labyrinth of network security.
As organizations strive to fortify their digital perimeters against ever-evolving cyber threats, understanding the nuances of Kerberos authentication and the role of Event ID 4768 becomes paramount. This introductory event marks the initiation of a complex authentication process, where users seek access to network resources through the procurement of Ticket Granting Tickets (TGTs) from the Key Distribution Center (KDC). However, beyond its surface significance lies a deeper layer of complexity. While Event ID 4768 heralds the commencement of the authentication exchange, it often conceals crucial details vital for effective security monitoring, such as the identity of the user initiating the request. Thus, amidst the intricate dance of network security, Event ID 4768 emerges as a focal point, compelling organizations to delve deeper into its implications and decipher its role in safeguarding digital assets against the relentless tide of cyber threats.
Understanding Event ID 4768
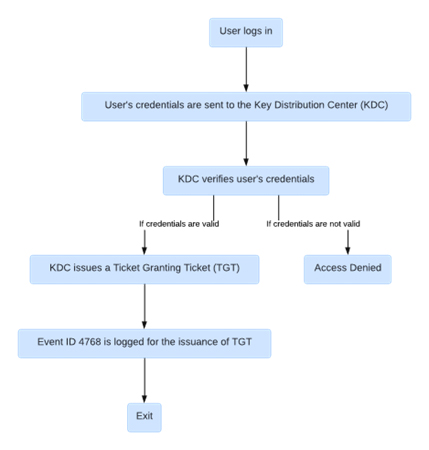
A. Ticket Granting Ticket (TGT)
At the core of Kerberos authentication lies the Ticket Granting Ticket (TGT), a digital key granting access to the network’s inner sanctum. Far beyond a mere credential, the TGT acts as the cornerstone of secure traversal across the digital landscape. It encapsulates the user’s authenticated identity, enabling seamless interaction with network resources while maintaining robust security protocols.
B. The Ritual of TGT Procurement
Event ID 4768 serves as the herald, signaling the commencement of the TGT procurement process. When a user seeks access to network resources, they embark on a journey orchestrated by the Key Distribution Center (KDC). This journey entails a series of cryptographic exchanges, culminating in the issuance of the coveted TGT. Event ID 4768 captures the essence of this ritual, offering insights into the intricate mechanisms governing user authentication within the Kerberos framework.
C. Unveiling the Veil of Secrecy
Despite its significance, Event ID 4768 operates within the confines of certain limitations. Notably, the event fails to disclose critical details, such as the identity of the user requesting the TGT. This omission poses challenges for security administrators, who must navigate the digital landscape armed with incomplete information. However, despite its limitations, Event ID 4768 remains a valuable tool in the arsenal of security professionals, offering glimpses into the inner workings of Kerberos authentication and guiding organizations towards enhanced network security practices.
In essence, understanding Event ID 4768 transcends mere technical proficiency; it necessitates a comprehensive grasp of the symbiotic relationship between Kerberos authentication and network security. By navigating the intricate nuances of this event, organizations can bolster their defenses against potential threats and navigate the digital landscape with confidence and resilience.
Why Monitor Event ID 4768?
In today’s dynamic cybersecurity landscape, vigilant monitoring of Event ID 4768 is essential for safeguarding digital environments. This event holds significant importance due to its various security benefits and compliance imperatives.
Security benefits associated with Event ID 4768 include the detection of potential privilege abuse. Monitoring helps identify unauthorized attempts to exploit elevated privileges, preventing potential breaches. It also aids in identifying suspicious activity, such as the Pass-the-Ticket technique, enabling prompt response measures. Additionally, organizations gain valuable insights into user interactions, aiding auditing processes and detecting anomalous behaviors indicating security risks.
Monitoring Event ID 4768 is crucial for meeting compliance requirements. Regulatory mandates necessitate Kerberos authentication event monitoring, including Event ID 4768, as a foundational element of compliance frameworks. Compliance obligations often demand specific security controls to protect sensitive data and ensure IT system integrity, with Event ID 4768 monitoring playing a vital role in demonstrating compliance. Compliance with industry standards builds trust among stakeholders, highlighting the strategic importance of monitoring Event ID 4768 in the ongoing fight against cyber threats.
Conclusion
In the ever-evolving landscape of digital security, Event ID 4768 emerges as a beacon, guiding the vigilant towards a realm of heightened awareness. By deciphering the cryptic messages embedded within this event, organizations can fortify their defenses against the machinations of digital adversaries. So, the next time Event ID 4768 graces your security logs, seize the opportunity to unveil its secrets and fortify the bastions of network security.
By understanding the nuances of Kerberos authentication and the significance of Event ID 4768, IT professionals can wield this knowledge as a potent weapon in the ongoing battle for digital sovereignty. So, as you traverse the digital frontier, remember – vigilance is the watchword, and Event ID 4768 is your compass guiding towards secure horizons.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
