What is Ransomware?
Ransomware is a type of malicious software that encrypts the victim’s files, rendering them inaccessible until a ransom is paid to the attackers. The rise of ransomware has made it one of the most disruptive forms of cybercrime. Unlike other forms of malware, ransomware is particularly dangerous because it not only infiltrates into your system but also holds your sensitive data hostage, putting both your operations and reputation at risk.
Cybercriminals often demand payment in cryptocurrencies like Bitcoin, which provides them with a level of anonymity. The ransom amount can vary, but the impact of the attack is typically severe, leading to significant downtime, financial loss, and, in some cases, permanent data loss.
History of Ransomware Attacks
The concept of ransomware dates back to the late 1980s. The first known ransomware attack occurred in 1989, known as the “AIDS Trojan” or “PC Cyborg” ransomware. It was distributed via floppy disks and demanded a payment of $189 to be sent to a P.O. box in Panama to unlock the infected files. This rudimentary form of ransomware laid the groundwork for more sophisticated attacks that would emerge in the following decades.
Ransomware started gaining significant traction in the early 2010s with the rise of crypto-ransomware, where files are encrypted and only a decryption key can unlock them. The infamous “CryptoLocker” ransomware, which surfaced in 2013, marked a turning point in the evolution of ransomware. It spread through phishing emails and encrypted a wide range of file types, demanding payment in Bitcoin. This attack introduced the now-common practice of demanding cryptocurrency as ransom, making it harder to trace the cybercriminals involved.
Since then, ransomware attacks have become increasingly frequent and more sophisticated. High-profile incidents like the WannaCry attack in 2017, which affected over 200,000 computers across 150 countries, and the NotPetya attack, which caused widespread disruption in Ukraine before spreading globally, have highlighted the significant threat ransomware poses.
Types of Ransomware
The different forms of ransomware use distinct techniques to harm victims through their attack operations. All ransomware tries to force monetary payments though their goals are achieved by unique tactics among different strains. The various ransomware types demand knowledge to develop efficient defense systems for organizations. The following are the key ransomware versions available today.
1. Encrypting Ransomware (Crypto-Ransomware)
Encrypting Ransomware stands out as the most destructive of all ransomware forms. The crypto-ransomware encrypts files through sophisticated encryption algorithms to make data inaccessible unless the attacker receives payment through ransom.
The malware inflicts a system by identifying important documents and images and databases before using encryption to block their access. When holding files hostage attackers direct victims to pay cryptocurrency through ransom notes.
Notable Examples:
- WannaCry became a major ransomware success story by leveraging a Windows operating system vulnerability to activate fast network expansion.
- Locky ransomware spread through phishing emails that forced users into macro activation until finally it encrypted files to request payment.
- Ryuk exploits big organizations for ransom payments which reach amounts exceeding millions of dollars.
A business seeking to retrieve data from ransomware attacks requires backups or cybersecurity solutions since decryption of encrypted files without the decryption key proves to be practically impossible.
2. Non-Encrypting Ransomware (Locker Ransomware)
Locker ransomware stops users from accessing their devices by employing a lock feature which serves as an alternative to file encryption before demanding payment.
After an infection occurs the victim’s display shows a ransom notice that pretends to be sent by law enforcement agencies falsely charging illegal behavior. The ransom message requires payment from victims to overcome the device lock.
Notable Examples:
- One of the first locker ransomware types WinLock displayed an image that asked victims to pay a ransom which covered the system screen replacement ability.
- The malware Reveton showed users bogus Federal Bureau of Investigation warnings that conformed victims into paying so-called legal penalties.
This type of ransomware disrupts infected systems because it does not perform file encryption but remains a major problem for businesses.
3. Mobile Ransomware
Modern ransomware hackers specifically choose mobile devices as their targets which they reach through deceptive application downloads and manipulated hyperlinks. A mobile ransomware attack works identically to locker or crypto-ransomware because it either binds the device with a lock or encrypts data files.
The attackers spread their malware by publishing incorrect info about apps or websites that host harmful code. When installed the ransomware deploys a lockdown function besides showing a ransom notification to the user. A few versions of this malicious software utilize security weaknesses to encrypt data stored on mobile phones.
Notable Examples:
- The banking malware Svpeng became ransomware to exploit Android operating system users.
- LockerPin stands as a severe threat that modifies the device security PIN to such an extent that users face immense struggles when attempting to restore access.
The frequency of mobile ransomware has grown because smartphones have replaced computer devices in both personal and business sectors.
4. Leakware (Doxware)
Leakware functions as doxware by both encrypting data along endangering to expose private information to the public unless the victim pays a ransom.
The malicious software enters systems to search for valuable data consisting of personal records and business documents together with financial details. Attackers who possess encrypted files choose public disclosure of stolen information as an alternative to payment demands. Customers whose businesses have sensitive customer data feel they must pay ransoms to stop their secret files from public exposure.
Notable Examples:
- Maze Ransomware served as the first ransomware family to adopt the double extortion technique through which it revealed stolen data from victims who did not make payment.
- Ransomware variant REvil (Sodinokibi) followed the same extortion technique by demanding huge ransoms of millions.
Organizations that keep confidential customer data face double dangers from leakware because it leads to both regulatory fines and legal action.
5. Scareware
The deception method known as Scareware depends on frightening victims into paying ransoms through fake security pop-ups while posing as official law enforcement personnel.
A fake popup message displays to inform users their system contains numerous viruses together with illegal activity participation. The program pursues two options from the victim: either download a fake antivirus application or face possible legal consequences. Scareware presents itself in two variations: some force users to endure repeated pop-ups and others function the same as locker ransomware by locking the system.
Notable Examples:
- The application named FakeAV presented itself as a genuine security program that declared system viruses and required payment to eliminate them.
- The Police Ransomware would show bogus law enforcement alerts that accused users of criminal activities before requiring financial payments.
Limited cybersecurity understanding makes users vulnerable to scareware because the program presents false threats that require ransom payments for non-existent fixes.
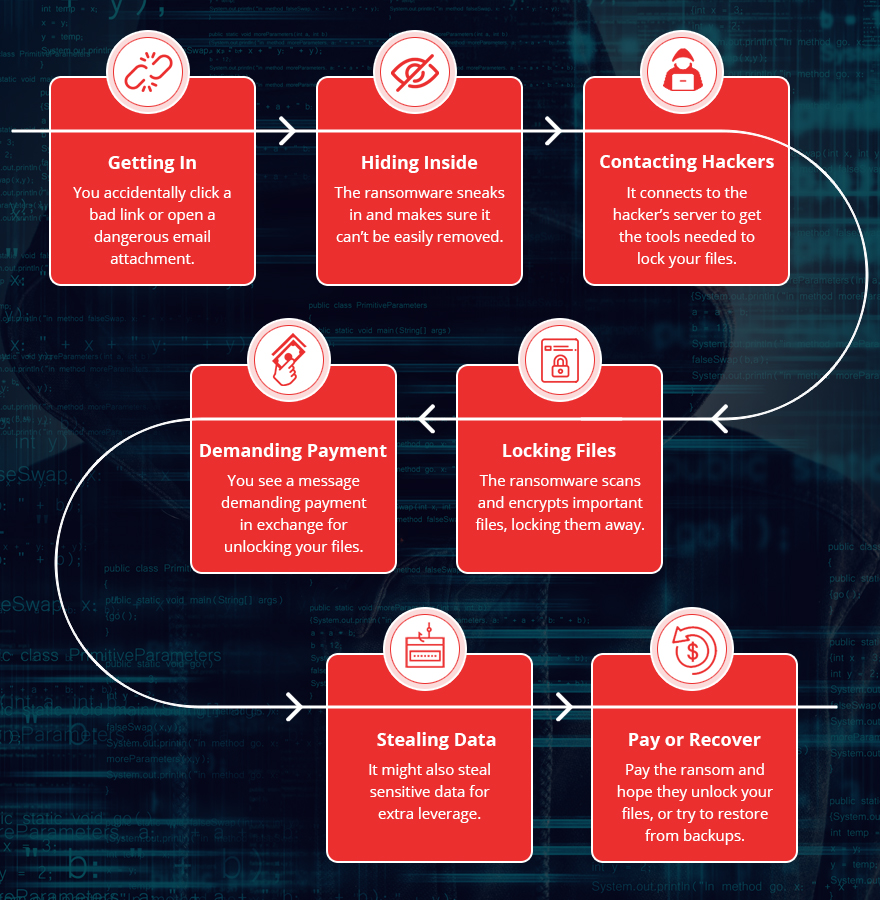
How Does Ransomware Work
Ransomware typically follows a series of steps from initial infection to encryption of files, ultimately demanding payment from the victim. Here’s a more detailed breakdown of the process:
How to Detect Ransomware
Detecting ransomware early is crucial to minimizing its impact. Several methods can help detect ransomware before it causes significant damage:
Behavioral Analysis: Monitoring the behavior of files and applications for signs of ransomware activity, such as rapid file encryption or unusual network communication, can help detect new or unknown ransomware variants.
Signature-Based Detection: Antivirus and anti-malware solutions use signature-based detection to identify known ransomware variants. However, this method may struggle with new or modified strains.
Heuristic Analysis: Heuristic analysis examines the characteristics and behavior of files to identify possible threats. This approach can detect ransomware by analyzing patterns that resemble known malicious behavior.
Deception Technology: Deception techniques, such as deploying honeypots or decoy systems, can lure ransomware into attacking a controlled environment. This allows security teams to detect and analyze the ransomware without risking real data.
Endpoint Detection and Response (EDR): The EDR solution monitors endpoints for suspicious activities and provides real-time alerts, enabling rapid response to ransomware attacks.
How to Report a Ransomware Attack
Before reaching out to law enforcement or cybersecurity experts, gather critical details about the attack:
- The ransom note (take screenshots if possible).
- File extensions of encrypted files (e.g., .locky, .crypt, .odin).
- Any suspicious emails, links, or downloads that might have triggered the attack.
- Logs of unusual network activity before the attack.
Having detailed information will help authorities and security professionals assess the attack type and provide relevant guidance.
The involvement of law enforcement is an essential step when responding to ransomware attacks. Reporting the incident helps authorities find the culprits and contributes to preventing additional attacks. Local areas around the world maintain specialized cybercrime units that handle attacks of this nature. Victims who partner with law enforcement agencies will help review cyber crimes and get access to necessary support measures that reduce the impact of losses. Organizations should report compromised sensitive data to regulatory bodies because data protection laws require this notification for compliance purposes.
Ransom Payments: To Pay or Not to Pay?
Knowledge about ransomware payments becomes essential during an attack activation process. Vault operators analyze multiple factors to calculate their demands which they base on the value they assess for the target’s data and financial resources. The ransom costs depend on several essential influence factors.
Target’s Financial Standing
When conducting ransom demands attackers select their ransoms based on a deliberate calculation. Attackers spend time examining their targets through research so they can determine suitable amounts by assessing financial status annual revenue and industry sector. Ransom demands that large corporations and government entities receive usually surpass the millions while small businesses with individuals find themselves subject to ransom requests ranging between hundreds to thousands of dollars.
Data Sensitivity
Data has different value points based on its specific characteristics. The understanding of sensitive data value by cybercriminals leads them to increase their ransom requests for such information. Attackers exploit sensitive data storage by organizations because victims typically make higher ransom payments to regain access to intellectual property, trade secrets, healthcare records, and customer financial information.
The sensitivity of patient records has positioned healthcare organizations among the leading sectors that attackers target. The unintentional disclosure of stored data or its unauthorized sale generates devastating results because it results in legal repercussions together with damaged public trust.
Scope of the Attack
The ransom amount depends significantly on the number of affected systems and the severity of the caused damage. The monetary demands from cyber criminals escalate when the vulnerability affects multiple devices as opposed to single-machine infections.
Ransomware-as-a-service (RaaS) organizations which persist today choose to use between two and three extortion methods. The criminals behind such attacks both encrypt data and issue threats that extend to public disclosure of sensitive information or additional computer intrusions thus creating stronger pressure for victims to pay ransom demands.
Should You Pay the Ransom?
All ransom payments should be avoided. Attackers do not provide decryption keys to victims even after receiving money payments. Research indicates that numerous enterprises that pay ransoms continue to experience new cyber attacks in the following months. Organizations that pay ransom money to cybercriminals primarily support attacks of this type because hackers view ransomware payments as a profitable business system.
Organizations must stop paying ransoms because they should establish preventive measures such as offline backup systems enhanced cybersecurity strategies and law enforcement incident reporting.
How to Remove Ransomware
The removal of ransomware is a sensitive process. The removal of malicious files alone may fail to resolve the issue because some strains embed deep into systems and try to restore themselves after removal. The correct process to eradicate ransomware from corrupted systems involves these fundamental actions:
Step 1: Isolate the Affected Device
Safe removal of ransomware starts by cutting all device networking connections between Wi-Fi and Ethernet platforms and external storage devices. The ransomware becomes disabled because system isolation stops its transmission to additional connected devices.
The propagation mechanism of ransomware involves network share drives as well as cloud storage platforms. The failure to separate an infected computer from the network right away causes ransomware to spread throughout organizational devices.
Step 2: Identify the Ransomware Strain
The correct recovery plan requires identifying the particular ransomware strain. The encryption tools for decrypting particular families of ransomware including WannaCry and Ryuk already exist. Security researchers and law enforcement agencies maintain regular updates of their ransomware decryption key databases that include known variants free of charge.
There are several encryption key decryption websites available on the internet that allow people to detect ransomware variations while identifying available decryption tools.
Step 3: Use Reputable Security Software
A trusted antivirus detection along with an anti-malware program enables users to detect and erase ransomware files. The use of this step fails to restore encrypted data without additional measures. Most contemporary ransomware strains destroy System Restore points and Shadow Copies which leads to complicated data return unless a backup exists.
Companies must deploy endpoint protection software containing real-time ransomware detection features because this stops new infections from occurring.
Step 4: Restore from Secure Backups
The current state of system backups enables operators to use them for recovering affected systems. Security backups need to be stored away from the network both online and in their own secure area because ransomware threats could impact backup files.
The process of restoring backups requires victims to check the security of their backup data prior to implementation. Complexe ransomware editions contain a stealth mode which stays inactive inside systems until backup restoration provides the opportunity for re-encryption.
Step 5: Update and Patch Systems
Ransomware takes advantage of system flaws present in out-of-date operating systems and software. Security against reinfection works best when all applications, firmware and security patch updates are kept current. The process of identifying weak IT infrastructure points begins with periodic security audits and vulnerability assessments.
Step 6: Monitor Systems for Residual Threats
Restoring a system from ransomware infection does not prevent a new attack from happening. Organizations must track their networks for any abnormal behavior and should create a readiness plan for future threats by developing incident response protocols.
Ransomware Attack Targets: Who’s at Risk?
The selection of ransomware targets happens through purposeful methods rather than arbitrary ones. The groups target industrial organizations along with corporate entities which represent likely ransom payment targets due to business operational values and data worth. Ransomware attackers predominantly strike these groups among others as their preferred targets.
Healthcare Organizations
Ransomware assaults routinely target healthcare facilities which include medical clinics alongside hospitals and medical research facilities. Healthcare facilities demonstrate urgency toward their services which triggers them to make ransom payments swiftly because prolonged downtimes are not feasible.
Medical records stand as a repository for extremely confidential information which includes Social Security numbers and both insurance data and complete health histories. Identity theft and dark web data sales are possible consequences of stolen information that force victims to pay ransom.
Educational Institutions
Ransomware attackers specifically target universities and schools because these institutions contain many sensitive user records along with inadequate security systems. Educational institutions that maintain obsolete IT infrastructure face threats to their security operations due to their lack of protection.
Shared networks among students and faculty continue to create conditions where malware easily spreads throughout the system. Schools have experienced multiple ransomware assaults during recent years which resulted in school closures and hampered research activities as well as representing large financial expenses.
Government Agencies
Government institutions at every level maintain broad archives of private data consisting of individual records in addition to financial details and classified message exchanges. The operations of these agencies make desirable targets since operational impairments will affect many members of the public.
Criminals target government institutions because they are aware that the time-related expense of downtime surpasses ransom payment amounts. Lack of payments emerges when governments choose to redirect their resources toward cybersecurity experts who aim to restore data instead of fulfilling the attacker’s demands.
Financial Institutions
Financial entities such as banks investment firms and credit unions fall under the highest risk category due to their access to monetary resources. The objective of cyber criminals who aim at financial institutions is to exploit ransomware either to disrupt banking operations or to steal monetary information.
Financial institutions operate under strict regulatory frameworks so ransomware attacks result in heavy penalties together with serious losses of customer confidence in the financial system. Financial institutions allocate extensive resources to build cybersecurity defenses because of the incidents that they face.
Small and Medium-Sized Businesses (SMBs)
SMBs have become the main target group for ransomware attacks instead of the typical big corporations which usually get media coverage. Smaller businesses remain at high risk because they lack the necessary budget to establish potent cybersecurity measures that attract attackers.
Hackers attack small businesses primarily due to their weak backup systems and inadequate IT support capacity when dealing with ransomware ransom demands. The attackers demand less expensive ransoms because they find smaller businesses easy targets leading victims to pay.
How Lepide Can Help
Lepide’s Data Security Platform offers a comprehensive ransomware protection solution designed to provide real-time visibility and automated responses to possible threats. By focusing on reducing your attack surface, Lepide helps identify and mitigate risks like inactive user accounts, excessive permissions, and open shares.
It detects the early signs of ransomware attacks, such as unusual file activity or behavioral changes, and responds instantly with automated actions, such as shutting down compromised accounts. With detailed audit logs, Lepide ensures you have the insights needed to investigate and recover swiftly.
If you want to know more about how Lepide’s Data Security Platform can help you protect against Ransomware, book a demo with one of our engineers today.


