AI Security Solution
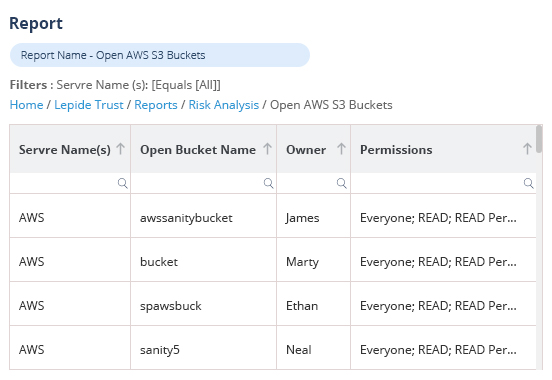
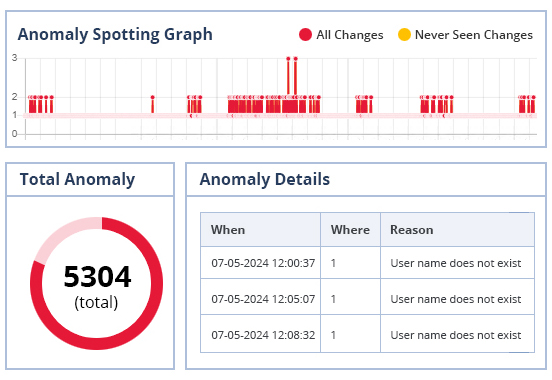
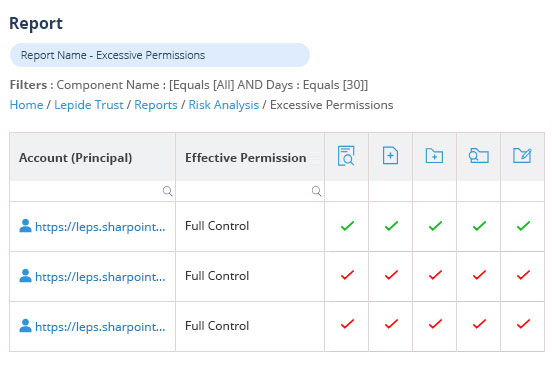
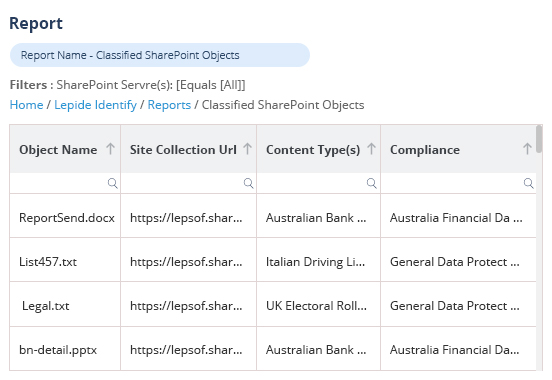
Copilot and other AI tools can help improve productivity by enabling better use of data and additional methods of content creation. However, many companies simply aren’t ready to adopt AI due to major concerns about security and privacy. This is where Lepide comes in.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x