Ongoing data protection made simple with Lepide.
Effective data protection doesn’t have to be difficult. With Lepide, you can focus on the data that matters most, and ensure your data is protected. Identify where your most sensitive data resides, understand user permissions, reduce your overall threat surface with AI-led remediation, and proactively detect and respond to threats. All from one, simple solution.
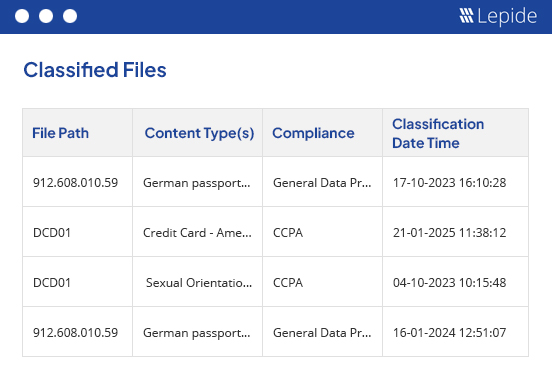
Identify your threat surface.
Implement hundreds of pre-defined criteria sets to locate sensitive data across your unstructured data stores and map to compliance mandates. Identify how your most privileged users are and discover exactly how permissions are being assigned. Spot risky configurations and security states, including inactive users, open shares, and users with non-compliant passwords.
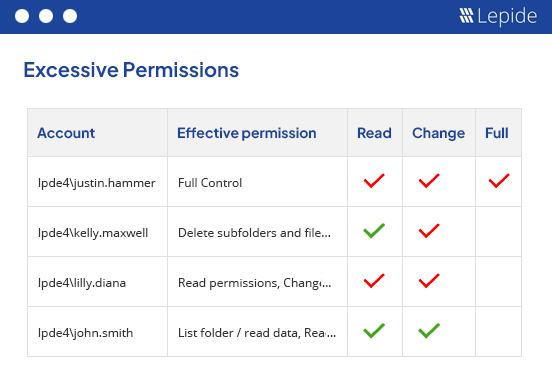
Implement zero trust.
Identify users with excessive permissions based on their data usage and use AI to automatically remediate permissions to implement zero trust. Remove inactive users to reduce your threat surface. Spot changes to permissions that could lead to users with elevated permissions and an increased risk of privilege abuse.
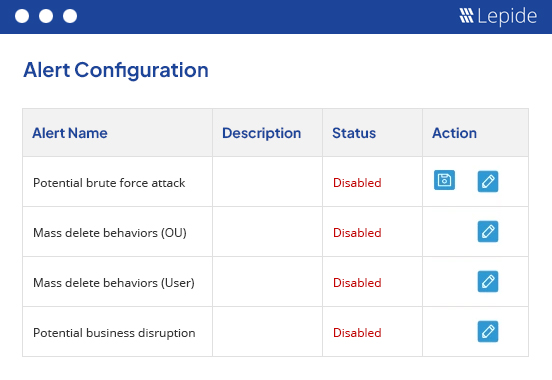
Detect and respond to threats.
Analyze user behavior and detect anomalies or unwanted activity with your sensitive data. Deploy pre-defined threat models to automatically detect and respond to threats like ransomware, brute force attacks, privilege escalation, and more. Receive real time alerts and use our mobile app to stay on top of your data protection efforts day and night.