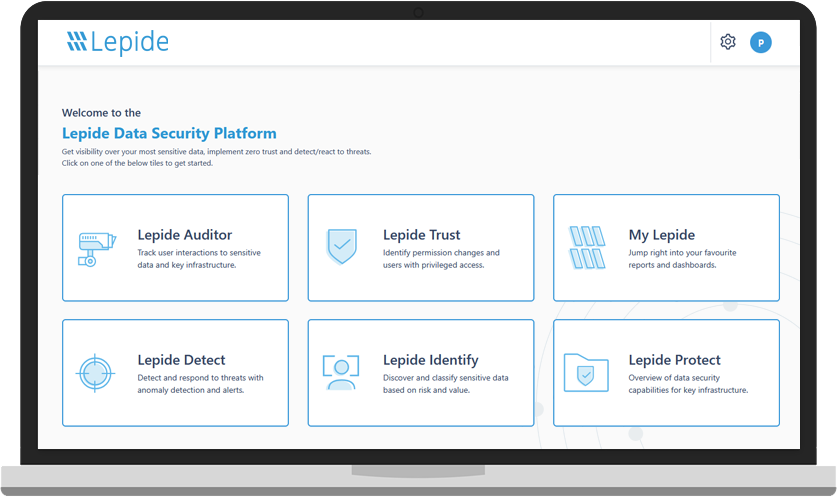
Data Security Posture Management (DSPM)
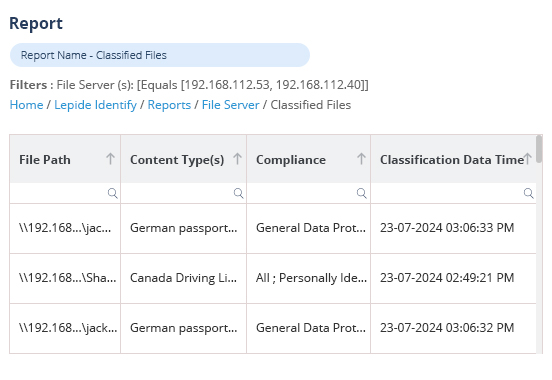
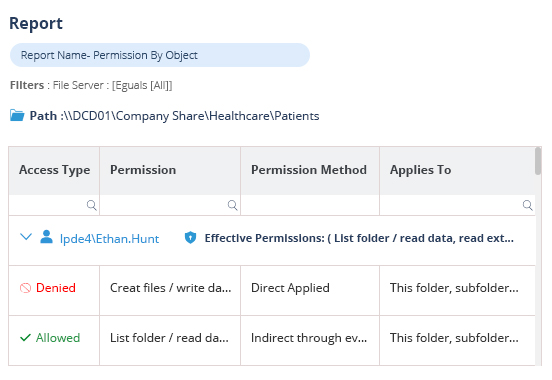
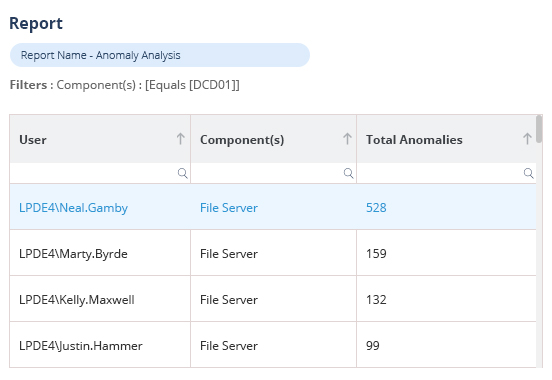
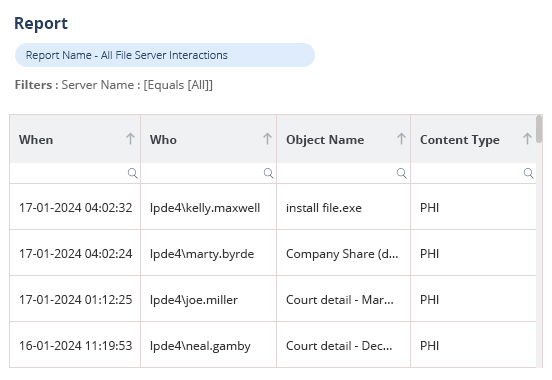
DSPM provides visibility as to where your sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is. With Lepide, you have a comprehensive solution for DSPM at your fingertips.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x