How It Works
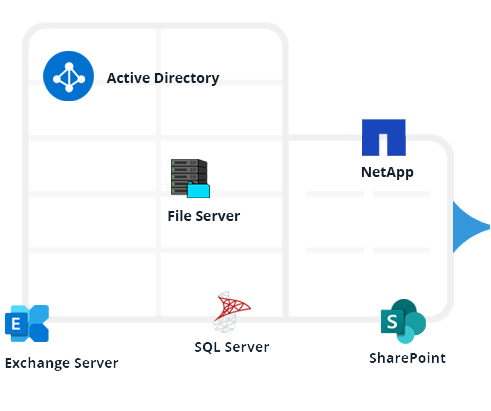
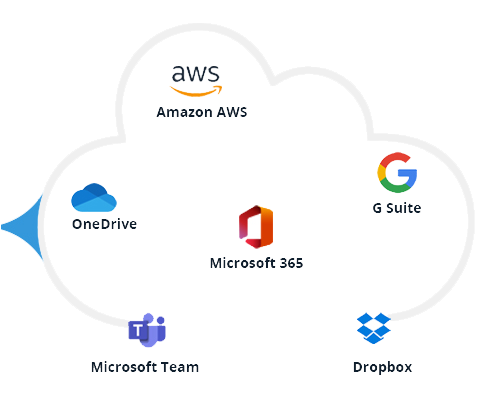
Modelled on a proven framework, our Data Security Platform uses tried and tested techniques to help you protect sensitive data, detect threats, and achieve compliance.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x