Microsoft 365 Copilot Security Solution
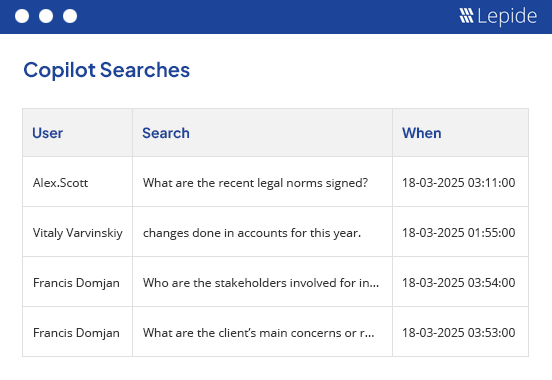
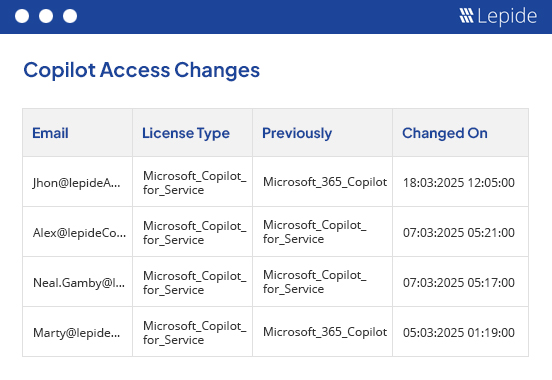
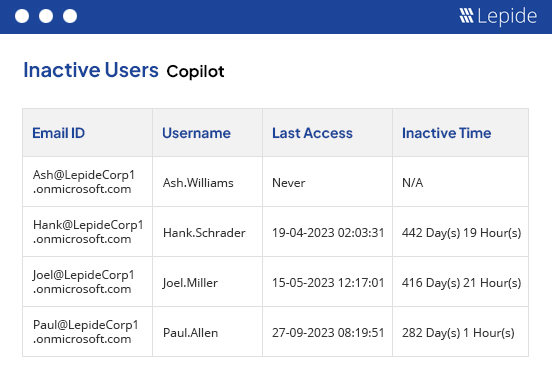
Ensure that your sensitive data remains secure before, during and after the implementation of Microsoft 365 Copilot. Understand who has access, why they have access and what is happening to your data.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x