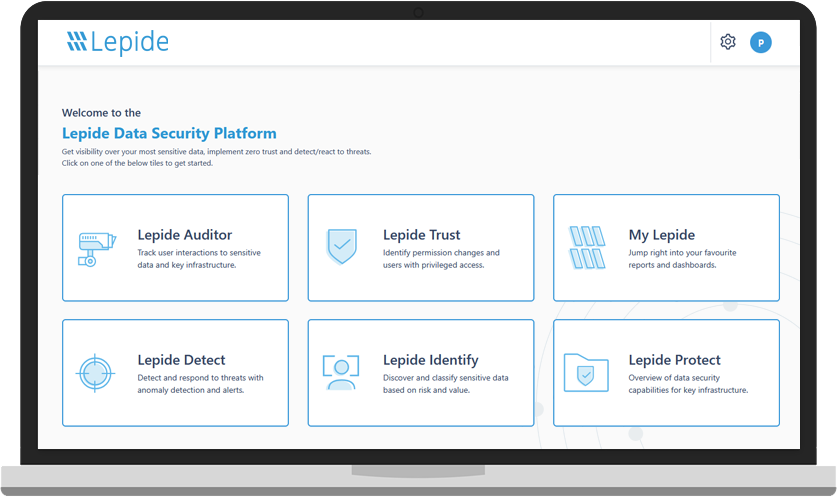
Microsoft Teams Auditing and Reporting
Microsoft Teams is more popular than ever before. As with any sharing and collaboration platform, Teams brings with it a host of security risks, usually down to rushed deployments with misconfigured permissions. Take the complexity out of MS Teams security and get more visibility over your Office 365 environment with Lepide.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x