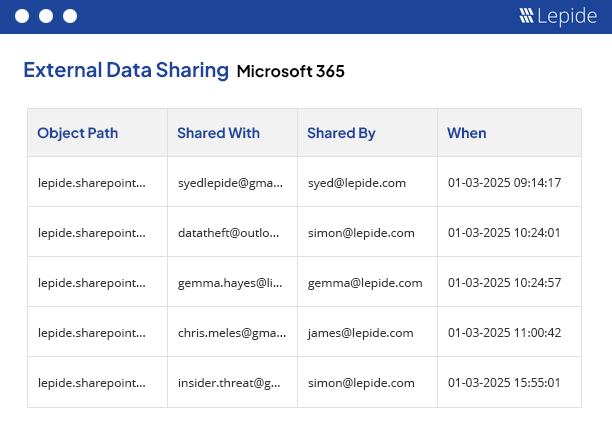
Understand what’s happening with your data and whether the changes being made are affecting security.
Determine whether any changes made to permissions, configurations or security groups are putting your data at risk.
Discover and classify sensitive data on OneDrive so that you can prioritize risk and focus your security strategy on what matters most.