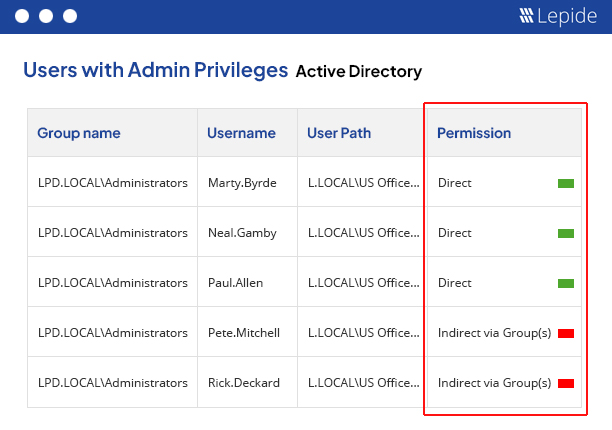
Privileged Access Management Solution
Fortify security, control privileges, and streamline compliance with our cutting-edge privileged access management tool.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x