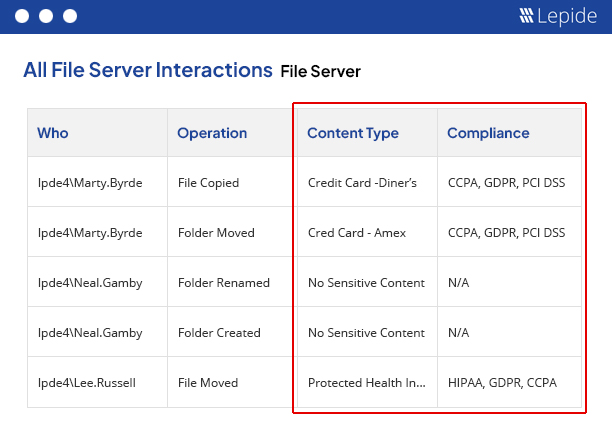
The Complete Ransomware Protection Solution
Improve your ransomware attack protection capabilities and safeguard your on-premise and cloud data with Lepide.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x