Quickly and Easily Reduce Risk to Your Data and Systems
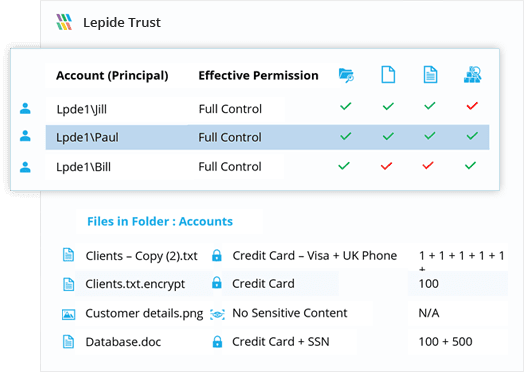
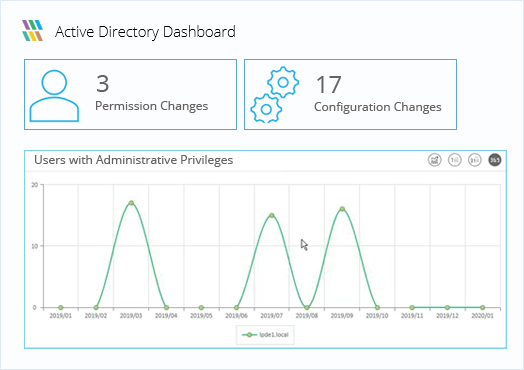
Instantly identify and reduce risk to your most sensitive data and critical infrastructure through visibility over privileged users and over exposed data.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x