Lepide Detect
Real Time Threat Detection and Response Solution
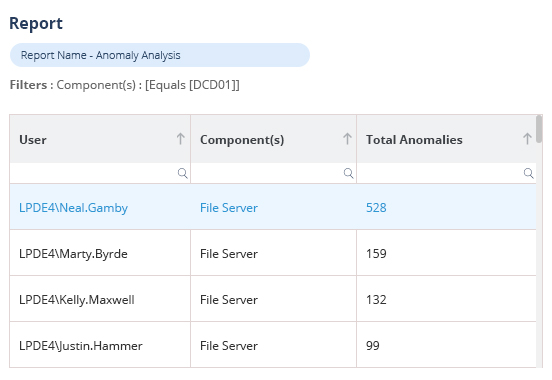
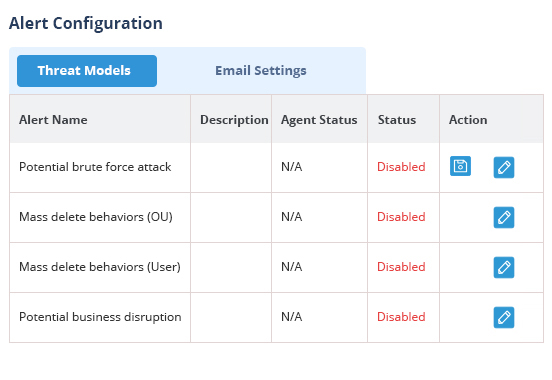
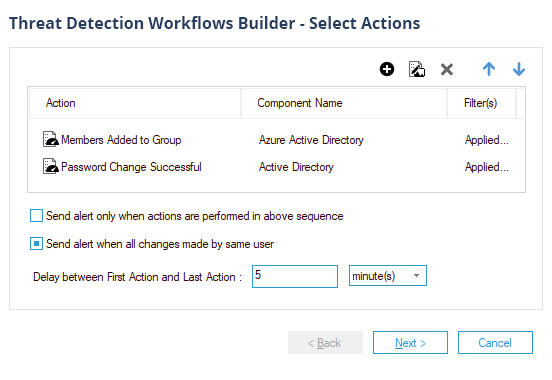
Pre-defined threat models, and automated threat response, mean you can detect the signs of a compromise or security incident, and react in real time before it causes significant damage.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x